WPA-PSK(TKIP)
1. Beacon frames are transmitted periodically to anonunce presence of wireless network and contain all information about it(data rates, channels, security ciphers, key management etc):
2. Probe request, is sent by STA to obtain information from AP:

3. Probe response, AP responds with with a probe response frame, containing capability information, supported data rates, etc., when after it receives a probe request frame from STA:

4. 802.11 authentication is a process whereby the access point either accepts or rejects the identity of a radio NIC. The NIC begins the process by sending an authentication frame containing its identity to the access point. With open system authentication (the default), the radio NIC sends only one authentication frame, and the access point responds with an authentication frame as a response indicating acceptance (or rejection).:
a. Dot11 authentication request:

b. Dot11 authentication response:

5.
802.11 association enables the access point to allocate resources for and synchronize with a radio NIC. A NIC begins the association process by sending an association request to an access point. This frame carries information about the NIC (e.g., supported data rates) and the SSID of the network it wishes to associate with.
a. Dot11 association request:

After receiving the association request, the access point considers associating with the NIC, and (if accepted) reserves memory space and establishes an association ID for the NIC.
b. Dott11 association response:

6. 4-way handshake, during this phase PTK is created, PSK is used as PMK to construct those values:
a. AP sends 802.1x authentication frame with ANonce, STA now has all information to construct PTK:

b. STA responds with 802.1x authentication frame with SNonce and MIC:

c. AP constructs 802.1x frame with new MIC and GTK with sequence number, This sequence number will be used in the next multicast or broadcast frame, so that the receiving STA can perform basic replay detection:

d. STA sends ACK:

From that point all data is sent encrypted.
WPA2-PSK(AES/TKIP)
The process if fairly the same as in previous section, I’ll highlight only information that is different.
1. WPA2 AP management frame include RSN element that included unicast cipher suite, AKM information and GTK cipher suite (if both AES and TKIP are selected, then less stronger encryption method will be used for GTK).

2. During 4-way handshake frames contain version information for WPA2 in “Type” fields.

Note: you can decrypt WEP/WPA-PSK/WPA2-PSK encrypted wireless traffic if 4-way handshake key exchange frames are included in trace and PSK is known.
In order to encrypt wireless traffic in wireshark open Preferences-> Protocols->IEEE 802.11 and provide PSK information and select “Enable decryption option”.
To decrypt WPA/WPA2 encrypted traffic specify Key in format:
“wpa-psk:PSK:SSID”
Note: In order to filter out WLAN traffic from specific STA in wireshark you could use “WLAN Statistic” option.
In order to filter traffic from specific STA go to “Statistics -> WLAN Traffic”, from the list of SSIDs select corresponding SSID STA is associated with, and apply filter based on the STA.

WPA/WPA2 Enterprise
1) WPA(TKIP)/WPA2(AES) with dot1x (PEAP)
This process follows the same steps like previous except for the AKM method and deriving PTK/GTK and AP advertised attributes in 802.11 management frames.
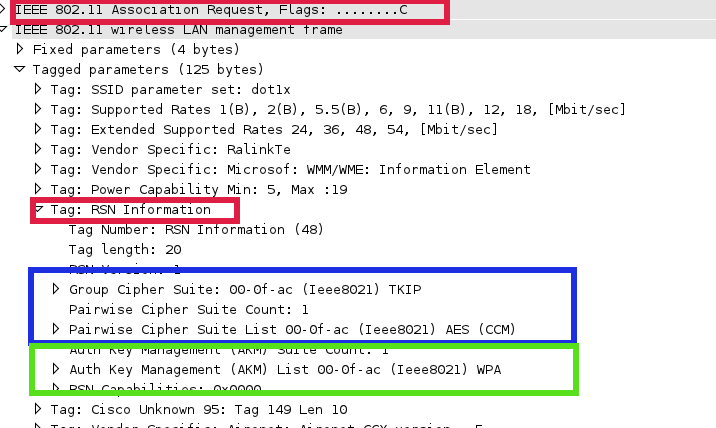
a. In this example AP advertises WPA(TKIP)/WPA2(AES) with dot1x authentication, both RSN and WPA tag attributes for AKM contain WPA value, whether in case of PSK authentication this field contains “PSK”. Also in this example TKIP is used for WPA and AES is used for WPA2

b. STA selects one of authentication methods and cipher suites advertised by AP. In this case WPA2 with AES was selected, that can be seen in RSN IE parameters.
c. After successful dot11 association dot1x authentication takes place, during this process we can see what EAP method is used by STA for authentication and certificate(s) exchange information between supplicant and AAA server.

d. After successful dot1x authentication PMK is trasmited to AP in “Access-Accept” message from AAA server and the same PMK is derived on the client, next 4-way handshake takes place and PTK and GTK establishment.
Radius exchange between WLC and AAA server:

General flow diagram:

WPA(TKIP)/WPA2(AES) with dot1x (EAP-TLS)
Difference for this type of authentication compared to the previous one is that client provides its certificate in “Client Hello” message and mutual authentication is performed between client and AAA server based on certificates.
EAP exchange between STA and WLC:

Radius exchange between WLC and AAA server:

General flow diagram:

2) WPA(TKIP)/WPA2(AES) with dot1x (FAST)
Only dot1x authentication stage is a bit different comparing to the previous example. After successful dot11 association dot1x authentication takes place, AP sends dot1x identity request to the STA and STA provides identity response, the response depends on what PAC provisioning is been in use (in-band PAC provisioning (phase 0) or out-of-band PAC provisioning). In case of in-band provisioning PAC is sent to the client from AAA server, once client has PAC it goes to EAP-FAST phase1 from this point TLS tunnel establishment starts (phase 1)

After TLS tunnel is established inner authentication method (phase 2) starts inside encrypted tunnel. On successful authentication PMK is send in “Access-Accept” message to AP from AAA server, the same key is derived based on dot1x exchange on STA. This key (PMK) is used to calculate PTK during 4-way handshake that will be used to secure communication between STA and AP.
General flow diagram:




No comments:
Post a Comment