This can be achieved with WinDbg. It seems you already know WinDbg, since you used the tag. Establish a remote kernel session (MSDN).
Once connected, use
.dump /f to take a full kernel dump, which is the contents of the physical RAM.Memory Forensics: How to Pull Passwords from a Memory Dump
Last time, we talked about a quick and easy way to get a memory dump on a Windows based PC. This time, we will cover pulling passwords out of captured memory files.
Several programs exist for memory analysis, we will be using “Volatility” from Volatile Systems. If you are performing your analysis on a Windows system I recommend downloading the stand alone .exe version. If you don’t then you will also need to install Python.
Once Volatility is installed, we need to get some information from the memory dump. Open up a command prompt and run the following command:
volatility imageinfo -f memorydumpfilename.raw
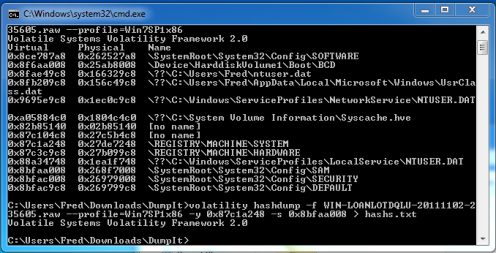
This command gives you several pieces of information, for now, we just need to know the profile type of the memory dump, in this case Win7SP1x86. We will use this in the next few steps.
Now, we need the hive list so we can get the starting location in memory of where the registry information resides:
volatility hivelist -f memdumpfilename.raw –profile=Win7SP1x86 (Use double dashes in front of profile for some reason they are showing up as a single)
We now have a list of where several key items are located in the memory dump. Next, we will extract the password hashes from the memory dump. To do this we need to know the starting memory locations for the system and sam keys. We look in the dump above and copy down the numbers in the first column that correspond to the SAM and SYSTEM locations. Then output the password hashes into a text file called hashs.txt:
volatility hashdump -f memdumpfilename.raw –profile=Win7SP1x86 -y 0x87c1a248 -s 0x8bfaa008 > hashs.txt (double dashes in front of profile)
Open the hash dump file in a text editor and you should see hashes of all the user’s passwords:
Now, if you are using Windows XP and have passwords shorter than 14 characters (LM passwords), you can run them through a password cracker like John the Ripper. Or better yet, you can copy the long alphanumeric string after the user id number (500 or 1000 numbers) and paste them in Objectif Sécurité’s Online XP Hash cracking program. This utility cracks most LM based password hashes in 5 seconds or less. For more information see Cracking 14 Character Complex Passwords in 5 Seconds.
This will not work on Windows 7 passwords or XP passwords longer than 14 characters though. These hashes are stored in the more secure NTLM format and can take a lot longer to crack. One cool thing though is that you do not need to crack the NTLM hash to get access to a system. You can log into a system using the hash itself as the password!
The password could be a simple 14 character password or a complex 32 character monster, it does not matter. You can still use the hash to get a command prompt. For more information see NTLM Passwords: Can’t Crack it? Just Pass it!
This really goes to show that passwords really are not as safe as one might think. Dual or multiple authentication systems are really the way to go on secure systems.
Well, that wraps up pulling passwords off of a memory dump, next we will learn how to view the active network connections and processes from a memory dump.






No comments:
Post a Comment