From: goncalo.costa at kpnqwest.pt (Goncalo Costa)
Subject: JAP back doored
>
> Don't be a smart ass.
>
Well, good morning to you too !
> Your arguments have nothing to do with the argument at hand which is quite
> simple: Governments should have no right to force developers to trojanize
> their applications and keep silent about it.
>
Governments have a lot of powers they should not have but German government
had nothing to do with this.
I hope you can tell the difference between a government eavesdropping on
someone and a judge/court order to eavesdrop on a suspect to gather evidence
against him.
> There have been some notes come out of this:
1> Germany has now removed this legal action, which is great
I think you should stop for a minute and try to learn the difference between
Germany (country), the German state, the German government and the German
judicial system.
"Germany" did nothing.
If you want to talk about the German government you could talk about
http://www.gnupg.org/aegypten
> 2> They intended to only watch traffic to a single German server
It seems you did not follow some posts on this list. I believe someone from
Germany explained the why and how of this JAP backdoor, and mentioned that.
3> The developers may not
> have been so forced into doing this, as much as willing -- I rather doubt
> this, especially since the order was rescinded, but their culpability does
> factor into this
So you mean these guys offering a free public anonymizing service are to
blame for complying with a court order ? I'm sure you would rather go to
jail. Where's the free public anonymizing service you're providing to the
Internet ? I'd like to use it. I'm sure I can trust you to keep my id safe.
4> I, personally, admit I would not care if they did this
> for a very serious reason such as for pedophiles or terrorists... I think a
> lot of people outraged would have to agree with this... However, I am sure
> a lot would not
>
(I believe the same person also wrote) it was a pedophilia case.
> As for the US government, this is utterly unimportant. I was playing around
> even to begin to mess with that. Yes, I am unaware of the US actively
> trojanizing applications by forcing the developers to do this.
Lotus Notes NSA backdoor ?
We're not talking about a court order here.
And Notes was not free software - its customers paid for it.
Nor it was open source software as is the case with JAP.
> So are you.
> This is illegal. You wouldn't like it if it was the US doing this. So, what
> are your real motives here?
>
Besides money that is ? :-)
Your emails seemed more focused on the German government than anything else.
German government had nothing to do with this. This was a judge/court order.
My motives were plain and simple:
- you seem to believe that your government and its agencies always play by
the book - I was trying to show you that they don't
- you should not bash (especially the way you did) the German government when
your own government has a much worse track record on eavesdropping on
everyone else around the world
- you should not blindly trust your government nor its agencies as you seem
to. They have abused their powers in the past. They are abusing their
powers in the present. They will abuse their powers in the future.
Governments are made of people like you and me (worse in fact ;-).
Complaining of these decisions (which are mandated by a judge or court) is
really useless and a paradox. In my opinion either:
case 1. you don't trust the state/authorities/whatever and you cannot trust
anything and you cannot expect anonymous services to work as
advertised (this is the case in dictatorships/authoritarian regimes)
case 2. you are a hardcore privacy advocate and accept no eavesdropping on
anyone no matter what - not even eavesdropping on the suspect of
kidnapping your child
case 3. you (almost) trust the state/authorities/whatever and recognize/accept
the need to do certain things, as eavesdropping, that need to be done
in "some situations but not all" to "some people but not all"
As you said:
> 4> I, personally, admit I would not care if they did this for a very
> serious reason such as for pedophiles or terrorists...
So you are clearly in case 3.
(probably the same goes for everyone else who complained about this)
But if you trust the system then you must also trust that this is done only
when "it has to be done", and there's no use in complaining there, is there ?
In this case you were clearly not trusting the German state and were bashing
it as if it was a "case 1" (dictatorship or authoritarian regime).
Will there be _abuses_ by the authorities and the people behind them ?
Sure, but we'll complain about _that_ with reason on our side then.
>
> >
> > The world is made of people and people are the same
> > everywhere. Time and place don't seem to make a great
> > difference. Being naive and keeping your eyes shut doesn't
> > help either.
>
> I love being called na?ve by teenagers that have never even seen a dead
> body.
>
As I said before, from your posts to this list regarding this thread you seem
to have a blind faith in your government and its agencies. I would call that
being naive.
Thanks for the tip: I've modified my mail headers not to leak my age again !
And please explain that "dead body" part again.
>
> You think for some reason that I am opposed to intelligence actions by the
> US? I am not even opposed to Germany if they did this because it was
> against terrorists or pedophiles.
>
Well. As I explained before, if you accept this for some reasons then you
must trust "them" to know when to do it.
> You are the one quite na?ve if you believe your nation can exist free
> without an intelligence agency.
>
I don't remember having written this in my post. Did I ?
> Regardless, the existence of intelligence agencies is entirely a different
> matter.
Again: I don't remember having written anything about this in my post.
> What errors these agencies may have done in the past - US or German
Errors ? What errors ? Errors are something you do by mistake.
These agencies make no errors (unless when they're caught).
They deliberately abuse their powers when they have to.
> - is entirely irrelevant.
>
To this thread and list: yes.
To know history and to learn from it: no.
> Each matter must be taken at a time.
>
> Apples give no insight into oranges.
>
I always suspected that ! :-)
> > I would also suggest a daily reading at http://cryptome.org/
>
> Yeah, a lot of great American sites like this. In fact, I bet you know a
> lot more about the US intelligence then you do about Portugese.
>
You almost got it right: "Portuguese". Don't hesitate to ask me if you
need help with your English ! :-)
(I do hope you have a sense of humour)
> In fact, I bet you know a
> lot more about the US intelligence then you do about Portugese.
>
Well ! That's easy isn't it ?
There's not much to know about Portuguese intelligence agencies is there ?
And I'd like to hear your comments on my post to FD included below
(http://lists.netsys.com/pipermail/full-disclosure/2003-August/009108.html)
Best Regards to you too
Goncalo
-------------------------------------------------------
Subject: Java Anonymous Proxy (JAP) backdoored - another interesting story
Date: Tue, 26 Aug 2003 11:02:32 +0100
From: Goncalo Costa goncalo.costa@...qwest.pt
To: full-disclosure@...ts.netsys.com
For those of you shocked at learning that JAP had been backdoored at
the request/order of a judge/court to investigate a criminal, here is
another interesting story.
Notice the SURFOLA.com disclaimer.
---------- Forwarded Message ----------
>Date: Sat, 23 Aug 2003 00:00:11 +0200
From: Barry Wels
>Subject: blackmail / real world stego use
>Sender: owner-cryptography@...zdowd.com
>To: cryptography@...zdowd.com
Thursday, September 22, 2016
Wednesday, September 21, 2016
telegram-bot-bootstrap A bootstrap for Telegram bot with directly deployable sample bot and JS-wrapped API methods
A bootstrap for Telegram bot with directly deployable sample bot and
JS-wrapped API methods. You can use all methods available in the
Telegram API directly, and send any supported media (we serialize the
formData for you to send over HTTP).
https://www.npmjs.com/package/telegram-bot-bootstrap
See the full API documentation of this project.
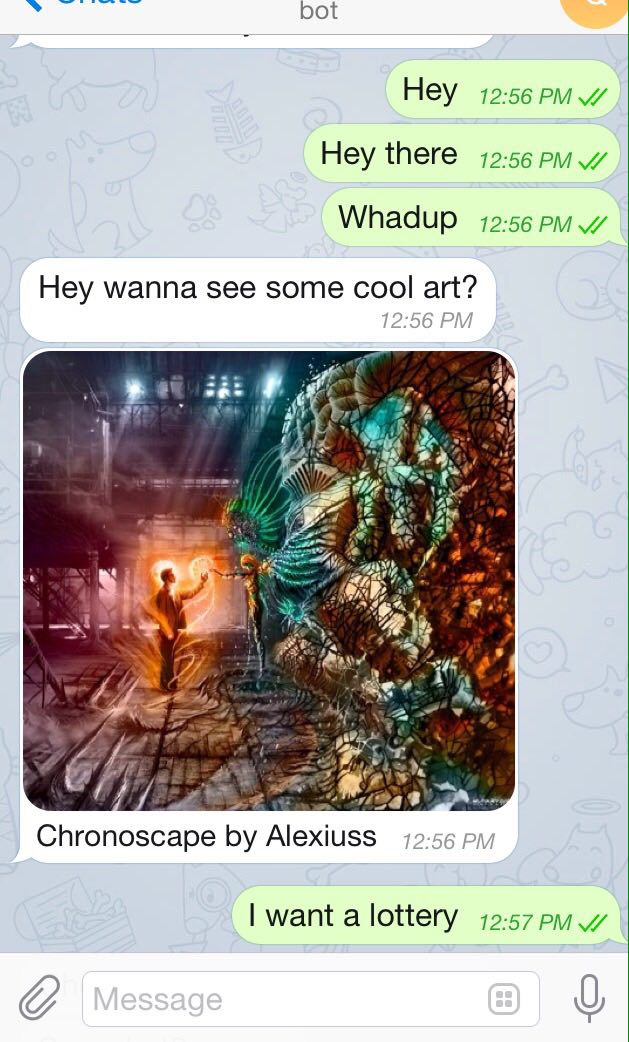
Either way you'll get a module with the Telegram bot API wrapped in Node, and a bootstrapped, deploy-ready project.
If you haven't already, get a bot from BotFather and remember your bot token!
AFTER THE BOT CONVENIENTLY INSTALLED WE MIGHT NEED THIS:https://www.npmjs.com/package/telegram-bot-bootstrap
See the full API documentation of this project.


Installation
Do either of
npm install telegram-bot-bootstrap
git clone https://github.com/kengz/telegram-bot-bootstrap.git
If you haven't already, get a bot from BotFather and remember your bot token!
Features
- Wrapped API methods take either a JSON object or multiple parameters.
- Auto serialization for HTTP formData: send photos/keyboards/media directly.
- API methods return
promises(uses q) for easy chaining and flow control. - Complete documentation and examples usages.
- Bootstrapped and directly deployable bot.
How to cast object in jBPM web service
I have been cracking my head on how to do this. I have a web service
where I am sending an Integer (ideally I want to send an Object) to the
service and expecting an Object in return.
It appears as though
the outbound SOAP message is working because in the console of my web
service I can see the database query being returned. However, in JBoss
BPMS I get the following error messagehttps://developer.jboss.org/thread/240965
Tuesday, September 20, 2016
Saturday, September 17, 2016
Business is booming in warplanes, missiles, and helicopters for
Portuguese arms traders like Luis Nogueira. This former in the
Portuguese Marines is one of a handful of Lisbon-based arms dealers,
many of whom have been in business for decades. At the first scent of
war in the Gulf, several of them came scurrying around to the Iraqi
Embassy, catalogues in hand, to peddle their wares....
He admits that earlier this year he gave the South Africans a design to convert water cannons for riot control into lethal instruments capable of transmitting high-voltage electric shocks through the jet of water. But that was just a favor for a friend.
Mr. Nogueira's family runs a string of arms-dealing companies from its office in a dingsy Lisbon office block
Informed sources in the arms trade allege that Mr. Nogueira arranged the sale of French antitank missiles and Belgian antiaircraft guns to Iraq last summer.
The arms dealers divert a large slice of Portugal's official exports to clandestine customers as well.
Over the past two years, about $15 million worth of arms and ammunition issued with export licenses for Gabon, Thailand, and Pakistan has vanished after leavint the Lisbon dockside. It was never ordered by these countries nor delivered, but much is thought to end up in South Africa.
http://www.csmonitor.com/1980/1112/111248.html
He admits that earlier this year he gave the South Africans a design to convert water cannons for riot control into lethal instruments capable of transmitting high-voltage electric shocks through the jet of water. But that was just a favor for a friend.
Mr. Nogueira's family runs a string of arms-dealing companies from its office in a dingsy Lisbon office block
Informed sources in the arms trade allege that Mr. Nogueira arranged the sale of French antitank missiles and Belgian antiaircraft guns to Iraq last summer.
The arms dealers divert a large slice of Portugal's official exports to clandestine customers as well.
Over the past two years, about $15 million worth of arms and ammunition issued with export licenses for Gabon, Thailand, and Pakistan has vanished after leavint the Lisbon dockside. It was never ordered by these countries nor delivered, but much is thought to end up in South Africa.
http://www.csmonitor.com/1980/1112/111248.html
the
Gideon spies are" Gideon, who was a Judge from 1145 to 1105 B.C., had
to remind the people how God wanted them to be ruled when they tried to
make HIM king!
22. And the men of Israel said to Gideon, "Rule over
us, both you and your son, and your son's son also, for you have
delivered us from the hand of Midian." 23. And Gideon said to them, "I
will not rule over you, neither shall my son rule over you. The LORD
shall rule over you" (Judges 8:22 - 23, Holy Bible in Its Original
Order"
Friday, September 16, 2016
Trapping signals in Docker containers Have you ever stopped a Docker container?
As an example, let’s run the following application (program.js) inside a container and examine signal handlers.
'use strict';
var http = require('http');
var server = http.createServer(function (req, res) {
res.writeHead(200, {'Content-Type': 'text/plain'});
res.end('Hello World\n');
}).listen(3000, '0.0.0.0');
console.log('server started');
var signals = {
'SIGINT': 2,
'SIGTERM': 15
};
function shutdown(signal, value) {
server.close(function () {
console.log('server stopped by ' + signal);
process.exit(128 + value);
});
}
Object.keys(signals).forEach(function (signal) {
process.on(signal, function () {
shutdown(signal, signals[signal]);
});
});
Here we create an HTTP-server that listens on port 3000 and setup two signal handlers for SIGINT and SIGTERM. When handled, the following message will be printed to stdout: `server stopped by [SIGNAL]`.
forces to decode the most probable coded sequence that succeeds the verification of the outer code
| /* |
| RFSniffer |
| Usage: ./RFSniffer [ |
| [] = optional |
| Hacked from http://code.google.com/p/rc-switch/ |
| by @justy to provide a handy RF code sniffer |
| */ |
|
|
| #include "../rc-switch/RCSwitch.h" |
| #include <stdlib.h> |
| #include <stdio.h> |
| |
| |
| RCSwitch mySwitch; |
| |
|
|
|
|
| int main(int argc, char *argv[]) { |
| |
| // This pin is not the first pin on the RPi GPIO header! |
| // Consult https://projects.drogon.net/raspberry-pi/wiringpi/pins/ |
| // for more information. |
| int PIN = 2; |
| |
| if(wiringPiSetup() == -1) { |
| printf("wiringPiSetup failed, exiting..."); |
| return 0; |
| } |
|
|
| int pulseLength = 0; |
| if (argv[1] != NULL) pulseLength = atoi(argv[1]); |
|
|
| mySwitch = RCSwitch(); |
| if (pulseLength != 0) mySwitch.setPulseLength(pulseLength); |
| mySwitch.enableReceive(PIN); // Receiver on interrupt 0 => that is pin #2 |
| |
| |
| while(1) { |
| |
| if (mySwitch.available()) { |
| |
| int value = mySwitch.getReceivedValue(); |
| |
| if (value == 0) { |
| printf("Unknown encoding\n"); |
| } else { |
| |
| printf("Received %i\n", mySwitch.getReceivedValue() ); |
| } |
| |
| mySwitch.resetAvailable(); | |||
| |
| } |
| |
| |
| } |
|
|
| exit(0); |
|
|
|
|
https://github.com/ninjablocks/433Utils/blob/master/RPi_utils/RFSniffer.cpp
Tuesday, September 13, 2016
Shor’s Algorithm – Breaking RSA Encryption
"If we determine several random divisors of (p-1)(q-1) by trying
different random values of x, then we can multiply those divisors
together to obtain (p-1)(q-1) itself. Once we know (p-1)(q-1), we can
then determine p and q. - ...."
http://blogs.ams.org/mathgradblog/2014/04/30/shors-algorithm-breaking-rsa-encryption/#sthash.h9GOM0Sn.dpbs
NEXT QUESTION :
NEXT QUESTION: WHAT'S THE HARDWARE?
http://blogs.ams.org/mathgradblog/2014/04/30/shors-algorithm-breaking-rsa-encryption/#sthash.h9GOM0Sn.dpbs
NEXT QUESTION :
What is the fastest factorization algorithm?
http://stackoverflow.com/questions/2267146/what-is-the-fastest-factorization-algorithm
NEXT QUESTION: WHAT'S THE HARDWARE?
Revolutionary TempFlat™ MEMS Resonators
https://www.sitime.com/technology/mems-resonators
Monday, September 12, 2016
I have here a software able do decode a quadrature of signals, which is exacly the protocol used by satelite GPS positions information, that is depending always on 4 satelites transmission togehter, to get precise positions, because of the amplification receivers noise. In this software meanning data aquisition processor port decoder command; on this attack I'm pretending to duplicate the signal, and confuse the call, so the satelite will think my signal is the true one.
Quadrature encoding and decoding
The purpose of theQDECODE command is to
monitor and decode pulse sequences that arrive on a pair of
digital lines on the Data Acquisition Processor digital
input port. These particular digital logic signals are produced
by a quadrature encoder attached to a device that can rotate
forward or backward. The QDECODE command must
determine the current angular position by monitoring the digital
pulses. You can do this monitoring using special
hardware devices, with excellent efficiency at high speeds.
When you don't have the high speeds, however, this command
might allow you to dispense with that extra hardware. http://www.mstarlabs.com/apeng/techniques/qdec.html
Subscribe to:
Comments (Atom)
Back@War @EmbaixadaRusPt Ambassador André Ventura @PartidoCHEGA @PJudiciaria T Constitucional sobre as contas da candidatura falta de provas 40€ despesas de telemóvel 98€ de refeições @MarinhaPT @fap_pt @Exercito_pt @govpt @EMGFA_RP @JNegocios @ojeconomico @dntwit @ecb @FT Portugal Intel eleições 2026
https://www.tribunalconstitucional.pt/tc/file/Relatorio_PR2021_AndreVentura_vf.pdf?src=1&mid=8303&bid=7012


