// START_DEFINITION
/**
* Fingerprint Tor authoritative directories enacting the directory protocol.
*/
fingerprint('anonymizer/tor/node/authority') = $tor_authority
and ($tor_directory or preappid(/anonymizer\/tor\/directory/));
// END_DEFINITION
// START_DEFINITION
/*
Global Variable for Tor foreign directory servers. Searching for potential Tor
clients connecting to the Tor foreign directory servers on ports 80 and 443.
*/
$tor_foreign_directory_ip = ip('193.23.244.244' or '194.109.206.212' or
'86.59.21.38' or '213.115.239.118' or '212.112.245.170') and port ('80' or
'443');
// END_DEFINITION
// START_DEFINITION
/*
this variable contains the 3 Tor directory servers hosted in FVEY countries.
Please do not update this variable with non-FVEY IPs. These are held in a
separate variable called $tor_foreign_directory_ip. Goal is to find potential
Tor clients connecting to the Tor directory servers.
*/
$tor_fvey_directory_ip = ip('128.31.0.39' or '216.224.124.114' or
'208.83.223.34') and port ('80' or '443');
// END_DEFINITION
// START_DEFINITION
requires grammar version 5
/**
* Identify clients accessing Tor bridge information.
*/
fingerprint('anonymizer/tor/bridge/tls') =
ssl_x509_subject('bridges.torproject.org') or
ssl_dns_name('bridges.torproject.org');
/**
* Database Tor bridge information extracted from confirmation emails.
*/
fingerprint('anonymizer/tor/bridge/email') =
email_address('bridges@torproject.org')
and email_body('https://bridges.torproject.org/' : c++
extractors: {{
bridges[] = /bridge\s([0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}):?([0-9]{2,4}?[^0-9])/;
}}
init: {{
xks::undefine_name("anonymizer/tor/torbridges/emailconfirmation");
}}
main: {{
static const std::string SCHEMA_OLD = "tor_bridges";
static const std::string SCHEMA_NEW = "tor_routers";
static const std::string FLAGS = "Bridge";
if (bridges) {
for (size_t i=0; i < bridges.size(); ++i) {
std::string address = bridges[i][0] + ":" + bridges[i][1];
DB[SCHEMA_OLD]["tor_bridge"] = address;
DB.apply();
DB[SCHEMA_NEW]["tor_ip"] = bridges[i][0];
DB[SCHEMA_NEW]["tor_port_or"] = bridges[i][1];
DB[SCHEMA_NEW]["tor_flags"] = FLAGS;
DB.apply();
}
xks::fire_fingerprint("anonymizer/tor/directory/bridge");
}
return true;
}});
// END_DEFINITION
// START_DEFINITION
/*
The fingerprint identifies sessions visiting the Tor Project website from
non-fvey countries.
*/
fingerprint('anonymizer/tor/torpoject_visit')=http_host('www.torproject.org')
and not(xff_cc('US' OR 'GB' OR 'CA' OR 'AU' OR 'NZ'));
// END_DEFINITION
// START_DEFINITION
/*
These variables define terms and websites relating to the TAILs (The Amnesic
Incognito Live System) software program, a comsec mechanism advocated by
extremists on extremist forums.
*/
$TAILS_terms=word('tails' or 'Amnesiac Incognito Live System') and word('linux'
or ' USB ' or ' CD ' or 'secure desktop' or ' IRC ' or 'truecrypt' or ' tor ');
$TAILS_websites=('tails.boum.org/') or ('linuxjournal.com/content/linux*');
// END_DEFINITION
// START_DEFINITION
/*
This fingerprint identifies users searching for the TAILs (The Amnesic
Incognito Live System) software program, viewing documents relating to TAILs,
or viewing websites that detail TAILs.
*/
fingerprint('ct_mo/TAILS')=
fingerprint('documents/comsec/tails_doc') or web_search($TAILS_terms) or
url($TAILS_websites) or html_title($TAILS_websites);
// END_DEFINITION
// START_DEFINITION
requires grammar version 5
/**
* Aggregate Tor hidden service addresses seen in raw traffic.
*/
mapreduce::plugin('anonymizer/tor/plugin/onion') =
immediate_keyword(/(?:([a-z]+):\/\/){0,1}([a-z2-7]{16})\.onion(?::(\d+)){0,1}/c : c++
includes: {{
#include
}}
proto: {{
message onion_t {
required string address = 1;
optional string scheme = 2;
optional string port = 3;
}
}}
mapper: {{
static const std::string prefix = "anonymizer/tor/hiddenservice/address/";
onion_t onion;
size_t matches = cur_args()->matches.size();
for (size_t pos=0; pos < matches; ++pos) {
const std::string &value = match(pos);
if (value.size() == 16)
onion.set_address(value);
else if(!onion.has_scheme())
onion.set_scheme(value);
else
onion.set_port(value);
}
if (!onion.has_address())
return false;
MAPPER.map(onion.address(), onion);
xks::fire_fingerprint(prefix + onion.address());
return true;
}}
reducer: {{
for (values_t::const_iterator iter = VALUES.begin();
iter != VALUES.end();
++iter) {
DB["tor_onion_survey"]["onion_address"] = iter->address() + ".onion";
if (iter->has_scheme())
DB["tor_onion_survey"]["onion_scheme"] = iter->scheme();
if (iter->has_port())
DB["tor_onion_survey"]["onion_port"] = iter->port();
DB["tor_onion_survey"]["onion_count"] = boost::lexical_cast(TOTAL_VALUE_COUNT);
DB.apply();
DB.clear();
}
return true;
}});
/**
* Placeholder fingerprint for Tor hidden service addresses.
* Real fingerpritns will be fired by the plugins
* 'anonymizer/tor/plugin/onion/*'
*/
fingerprint('anonymizer/tor/hiddenservice/address') = nil;
// END_DEFINITION
// START_DEFINITION
appid('anonymizer/mailer/mixminion', 3.0, viewer=$ascii_viewer) =
http_host('mixminion') or
ip('128.31.0.34');
// END_DEFINITION
Saturday, September 5, 2015
source code NSA Keyscore
Wednesday, August 5, 2015
Exploding chips could foil laptop thieves
A new way of making silicon explode could mean anyone trying to use a stolen laptop or mobile will be confronted by this message: “This machine is stolen and will self-destruct in ten seconds … “.
Until now scientists have only managed to make silicon go bang by mixing it with either liquid oxygen or nitric acid. But Michael Sailor and his colleagues at the University of California in San Diego have found a way to blow up silicon chips using an electrical signal.
They say their method could be used to fry circuitry in devices that fall into the wrong hands. For instance, the American spy plane impounded by China last year could have used it to destroy its secret electronics systems.
Sailor’s team hit upon this new way of exploding silicon when they applied the oxidising chemical gadolinium nitrate to a porous silicon wafer. As colleague Fred Mikulec used a diamond scribe to split the wafer it blew up in his face, giving Mikulec the shock of his life. Luckily, only a minute quantity of silicon was involved so it was a small bang. “It’s a bit like a cap in a cap gun going off,” says Sailor.
In a stolen mobile phone, the network would send a trigger signal to the part of the chip containing the gadolinium nitrate “detonator”, triggering the explosion. “We have shown that you can store this stuff and detonate it at will,” says Sailor.
Other applications suggested for the technology include testing for toxic substances in groundwater. The device could be used on the spot to burn minute samples on a disposable chip and analyse their chemical composition. Alternatively, it could be used as a fuel supply for microscopic machines etched onto silicon wafers, says Sailor.
Porous silicon-based explosive PATENT
US 7942989 B2
Until now scientists have only managed to make silicon go bang by mixing it with either liquid oxygen or nitric acid. But Michael Sailor and his colleagues at the University of California in San Diego have found a way to blow up silicon chips using an electrical signal.
They say their method could be used to fry circuitry in devices that fall into the wrong hands. For instance, the American spy plane impounded by China last year could have used it to destroy its secret electronics systems.
Sailor’s team hit upon this new way of exploding silicon when they applied the oxidising chemical gadolinium nitrate to a porous silicon wafer. As colleague Fred Mikulec used a diamond scribe to split the wafer it blew up in his face, giving Mikulec the shock of his life. Luckily, only a minute quantity of silicon was involved so it was a small bang. “It’s a bit like a cap in a cap gun going off,” says Sailor.
Fast burn
The gadolinium nitrate used the energy from the diamond scribe to oxidise the silicon fuel, which burns fast because its crystals have a large surface area. “The faster the burn, the bigger the bang,” explains Sailor. You would only need a tiny quantity of the chemical to do irreparable damage to delicate transistors, so it would be cheap and easy to add when the chips are being made.In a stolen mobile phone, the network would send a trigger signal to the part of the chip containing the gadolinium nitrate “detonator”, triggering the explosion. “We have shown that you can store this stuff and detonate it at will,” says Sailor.
Other applications suggested for the technology include testing for toxic substances in groundwater. The device could be used on the spot to burn minute samples on a disposable chip and analyse their chemical composition. Alternatively, it could be used as a fuel supply for microscopic machines etched onto silicon wafers, says Sailor.
Journal reference: Advanced Materials (vol 14, p 38)
US 7942989 B2
Resumo
An initiator explosive for detonating a second explosive that includes nanocrystalline silicon containing a plurality of pores and a solid state oxidant disposed within said pores.
CHANGE THE BIOS FOR THE MOBILE OPERATOR CAN'T MODIFY THE DETONATOR TIME
Create a USB Boot CD that can be used to boot Xubuntu 9.04 from USB flash drive on computers using a system BIOS that does not natively support booting from USB. The boot CD works by loading the initrd and vmlinuz kernel from the CD. Once the necessary USB drivers have been loaded, the boot CD proceeds to locate and load the filesystem from the USB flash drive. Because the USB driver modules are preloaded from the CD, the compressed filesystem can then be detected and loaded from the USB device even if your system BIOS does not support booting from USB.
Read the rest of this entry…
Read the rest of this entry…
Listed under Use a Boot CD to Boot from USB
Make a USB Boot CD for Kubuntu 9.04
This tutorial explains how to create a USB Boot CD that can be used to boot Kubuntu 9.04 from a USB flash drive on computers utilizing a system BIOS that does not natively support booting from USB. Kubuntu is a derivative of Ubuntu that uses the KDE desktop environment instead of Gnome. The USB boot CD created using this tutorial launches the initrd and vmlinuz kernel from the CD along with the necessary USB drivers, and then proceeds to locate the filesystem on the USB drive. Because the USB driver modules are preloaded from the initrd on the CD, the compressed filesystem can then be detected and loaded from the USB device.
Read the rest of this entry…
Read the rest of this entry…
Listed under Use a Boot CD to Boot from USB
Make a USB Boot CD for Kubuntu 8.10
This USB Boot CD can be used to boot Kubuntu 8.10 from a USB flash drive on computers with a BIOS that does not support booting from USB (including the Apple Mac, Macbook and, Macbook Pro). Kubuntu is a derivative of Ubuntu that uses the KDE desktop environment instead of Gnome. This boot CD loads the initrd and vmlinuz kernel from the CD and then loads the necessary USB drivers, proceeding to locate and extract the filesystem from the USB flash drive.
Read the rest of this entry…
Read the rest of this entry…
Listed under Use a Boot CD to Boot from USB
Make a USB Boot CD for Xubuntu 8.10
Much like a USB Boot CD that can be used to boot Ubuntu 8.10 from USB, this USB Boot CD can be used to boot a prepared Xubuntu 8.10 USB flash drive on computers containing a system BIOS that does not natively support booting from USB. The boot CD works by loading the initrd and vmlinuz kernel from the CD. Once the necessary USB drivers have been loaded, the boot CD proceeds to locate and load the filesystem from the USB flash drive.
Read the rest of this entry…
Read the rest of this entry…
Listed under Use a Boot CD to Boot from USB
Make a USB Boot CD for Ubuntu 8.10
This USB Boot CD can be used to boot a Ubuntu 8.10 USB flash drive on computers with a BIOS that does not natively support booting from USB. The boot CD contains a grub bootloader that loads the initrd and vmlinuz kernel from the CD and then proceeds to locate the filesystem on the USB flash drive. Because the USB drivers are preloaded from the initrd on the CD, the USB flash drive can then easily be detected.
Read the rest of this entry…
Read the rest of this entry…
Listed under Use a Boot CD to Boot from USB
How to Access BIOS
How to Access BIOS. Computer and motherboard manufacturers and BIOS suppliers may use varying keyboard keys or key combinations that can be pressed during system post to access your system BIOS. Unfortunately there is no standard method to universally access or enter a motherboard BIOS. The following is a list of some popular BIOS suppliers, Computer Vendors and the keyboard key combinations that have been known to work with them.
Read the rest of this entry…
Read the rest of this entry…
Listed under USB BIOS boot options
Booting Linux using USB-ZIP on older systems
If you have an older computer system, your BIOS might not support USB-HDD boot. In this case, it may still be possible to boot Linux from USB if your BIOS does list USB-ZIP as a boot option. In order for this to happen, we need to trick the BIOS into thinking that the USB flash drive is a zip drive.
We can trick the BIOS by modifying the number of heads and sectors being displayed from the USB flash device to match that of a zip drive. Then we partition the drive using partition 4 (the partition that zip drives typically use). For this tutorial we will use the mkdiskimage application that comes with syslinux.
Read the rest of this entry…
http://www.pendrivelinux.com/tag/bios/
Having the correct balance of fuel and oxidizer is key to having a stable burn in a thermite reaction. The thermite recipe for red iron oxide and aluminum is 3 parts iron oxide red to 1 part aluminum fuel. In pyrotechnic compositions the finer the ingredients and more well mixed they are, generally the easier it is to ignite, and the faster the reaction will progress.
So our goals in selecting thermite ingredients are ease of ignition and a stable, non-explosive burn.
For this example, we are using Skylighter's -325 mesh red iron oxide and Skylighter's -325 mesh bright aluminum, which has an average particle size of 45 microns.
Thermite#1 Mixture
To make a 4 ounce batch of thermite, first weigh out 3 ounces of red iron oxide. Then weigh out 1 ounce of aluminum powder. Dump them into a plastic tub, and put the top on. Shake them until the color is consistent throughout.
Then pass the mix through a 10-mesh or finer screen. If there are any clumps break them up with your fingers. Screen the mix two more times, or more, until you have a uniformly colored powder.
This can be a dusty process, so be sure and do it an area where the aluminum dust will not cause a problem. Do not try this where air is moving. The better you mix the ingredient, the faster and hotter the reaction will be. Thermite needs a very high temperature to ignite it.
Your thermite kit comes with 6 gold sparklers. The iron in them burns at around 1800 degrees F.
Here's how to use sparklers to ignite your thermite. Place your thermite mix in a plastic tub. Make a hole near the bottom on the side of the tub big enough for a sparkler to go through.
Push 1 to 2 of inches of the sparkler through the hole in the side of the tub into the mix inside. Leave at least 2-3 inches of your sparkler sticking out. Place the plastic tub on a metal surface that want to burn through. Light the sparkler, and get back 40 or 50 feet.
WARNING: Do NOT attempt to ignite your thermite by dipping your sparkler into the mix by hand. The mix can and does ignite violently, and will spray you with burning metal.
WARNING: A violent ignition of thermite can throw molten metal in all directions. Do not stand close to the mix when it is igniting or burning.
TIP: If you have trouble igniting your thermite with a sparkler, try mixing some magnesium powder or chips into a small amount of thermite mix. Then you should be able to ignite the magnesium mix using your sparkler.
WARNING: Thermite burns extremely hot and produces molten iron slag that can melt though a car's engine block! Burning thermite can spatter molten iron a long way from the burning pile. Stay as far back as you can. And make sure there is nothing nearby that can catch fire. Start your thermite experiments with small amounts at first, until you understand how it behaves, and how far it will throw molten metal slag.
WARNING: You cannot extinguish a thermite fire with water. Do not attempt to put the fire out with water, or you may have a violent, steam explosion, which can throw molten slag as well. Likewise, do not use any wet materials to attempt to extinguish the fire.
http://www.skylighter.com/fireworks/how-to-make/Thermite.asp
FOR SALE SEARCH FOR THE CAS NUMBER:
Metal Nano Powder
We can trick the BIOS by modifying the number of heads and sectors being displayed from the USB flash device to match that of a zip drive. Then we partition the drive using partition 4 (the partition that zip drives typically use). For this tutorial we will use the mkdiskimage application that comes with syslinux.
Read the rest of this entry…
http://www.pendrivelinux.com/tag/bios/
Making Thermite Using Red Iron Oxide
Having the correct balance of fuel and oxidizer is key to having a stable burn in a thermite reaction. The thermite recipe for red iron oxide and aluminum is 3 parts iron oxide red to 1 part aluminum fuel. In pyrotechnic compositions the finer the ingredients and more well mixed they are, generally the easier it is to ignite, and the faster the reaction will progress.
So our goals in selecting thermite ingredients are ease of ignition and a stable, non-explosive burn.
For this example, we are using Skylighter's -325 mesh red iron oxide and Skylighter's -325 mesh bright aluminum, which has an average particle size of 45 microns.
| Ingredient | Parts by Wt. | Parts by % |
| Red iron oxide -325 mesh | 3 | 75 |
| Aluminum flake -325 mesh | 1 | 25 |
| Total | 100% |
To make a 4 ounce batch of thermite, first weigh out 3 ounces of red iron oxide. Then weigh out 1 ounce of aluminum powder. Dump them into a plastic tub, and put the top on. Shake them until the color is consistent throughout.
Then pass the mix through a 10-mesh or finer screen. If there are any clumps break them up with your fingers. Screen the mix two more times, or more, until you have a uniformly colored powder.
This can be a dusty process, so be sure and do it an area where the aluminum dust will not cause a problem. Do not try this where air is moving. The better you mix the ingredient, the faster and hotter the reaction will be. Thermite needs a very high temperature to ignite it.
Your thermite kit comes with 6 gold sparklers. The iron in them burns at around 1800 degrees F.
Here's how to use sparklers to ignite your thermite. Place your thermite mix in a plastic tub. Make a hole near the bottom on the side of the tub big enough for a sparkler to go through.
Push 1 to 2 of inches of the sparkler through the hole in the side of the tub into the mix inside. Leave at least 2-3 inches of your sparkler sticking out. Place the plastic tub on a metal surface that want to burn through. Light the sparkler, and get back 40 or 50 feet.
WARNING: Do NOT attempt to ignite your thermite by dipping your sparkler into the mix by hand. The mix can and does ignite violently, and will spray you with burning metal.
WARNING: A violent ignition of thermite can throw molten metal in all directions. Do not stand close to the mix when it is igniting or burning.
TIP: If you have trouble igniting your thermite with a sparkler, try mixing some magnesium powder or chips into a small amount of thermite mix. Then you should be able to ignite the magnesium mix using your sparkler.
WARNING: Thermite burns extremely hot and produces molten iron slag that can melt though a car's engine block! Burning thermite can spatter molten iron a long way from the burning pile. Stay as far back as you can. And make sure there is nothing nearby that can catch fire. Start your thermite experiments with small amounts at first, until you understand how it behaves, and how far it will throw molten metal slag.
WARNING: You cannot extinguish a thermite fire with water. Do not attempt to put the fire out with water, or you may have a violent, steam explosion, which can throw molten slag as well. Likewise, do not use any wet materials to attempt to extinguish the fire.
http://www.skylighter.com/fireworks/how-to-make/Thermite.asp
FOR SALE SEARCH FOR THE CAS NUMBER:
Metal Nano Powder
Thursday, July 30, 2015
Optical Emission Security – Frequently Asked Questions
Markus Kuhn In the paperOptical Time-Domain Eavesdropping Risks of CRT Displays,I describe a new eavesdropping technique that reconstructs text on computer screens from diffusely reflected light. This publication resulted in some wide media attention (BBC, New Scientist,Wired, Reuters, Slashdot). Here are answers to some of the questions I have received, along with some introductory information for interested readers looking for a more highlevel summary than the full paper, which was mainly written for an audience of hardware-security and optoelectronics professionals. Q: How does this new eavesdropping technique work? To understand what is going on, you have to recall how a cathode-ray display works. An electron beam scans across the screen surface at enormous speed (tens of kilometers per second) and targets one pixel after another. It targets this way tens or hundreds of millions of pixels every second to convert electron energy into light. Even though each pixel shows an afterglow for longer than the time the electron beam needs to refresh an entire line of pixels, each pixel is much brighter while the e-beam hits it than during the remaining afterglow. My discovery of this very short initial brightness in the light decay curve of a pixel is what makes this eavesdropping technique work. An image is created on the CRT surface by varying the electron beam intensity for each pixel. The room in which the CRT is located is partially illuminated by the pixels. As a result, the light in the room becomes a measure for the electron beam current. In particular, there is a little invisible ultrafast flash each time the electron beam refreshes a bright pixel that is surrounded by dark pixels on its left and right. So if you measure the brightness of a wall in this room with a very fast photosensor, and feed the result in another monitor that receives the exact same synchronization signals for steering its electron beam, you get to see an image like this:
2002 IEEE Symposium on Security and Privacy, Berkeley, California, May 2002.
- The eavesdropped videosignal is periodic over at least a few seconds, therefore periodic averaging over a few hundred frames can help significantly to reduce the noise.
- If you know exactly what font is used, many of the equalization and symbol detection techniques used in modems or pattern recognition applications can be applied to recover the text (remote optical character recognition).
- Optical filters can eliminate other colours from background light.
- A large sensor aperture (telelens, telescope) can improve the photon count.
- Reception is difficult if not impossible from well-lit rooms, in which CRTs do not make a visible contribution to the ambient illumination. Don't work in the dark.
- No not assume that etched or frosted glass surfaces prevent this technique if there is otherwise a direct line of sight to the screen surface.
- This particular eavesdropping technique is not applicable to LCDs and other flat-panel displays that refresh all pixels in a row simultaneously.
- Make sure, nobody can install eavesdropping equipment within a few hundred meters line-of-sight to your window.
- Use a screen saver that removes confidential information from the monitor in your absence.
created 2002-03-05 – last modified 2004-11-29 – http://www.cl.cam.ac.uk/~mgk25/emsec/optical-faq.html
Saturday, July 4, 2015
Friday, July 3, 2015
Stealing Keys from PCs using a Radio:
Cheap Electromagnetic Attacks on Windowed Exponentiation
| Daniel Genkin | Lev Pachmanov | Itamar Pipman | Eran Tromer |
| Technion and Tel Aviv University | Tel Aviv University | Tel Aviv University | Tel Aviv University |
This web page contains an overview of, and Q&A about, our recent results published in a technical paper (PDF, 2.1MB), archived as IACR ePrint 2015/170. It will be presented at the Workshop on Cryptographic Hardware and Embedded Systems (CHES) 2015 in September 2015.
This research was conducted at the Laboratory for Experimental Information Security (LEISec).
Overview
We demonstrate the extraction of secret decryption keys from laptop computers, by nonintrusively measuring electromagnetic emanations for a few seconds from a distance of 50 cm. The attack can be executed using cheap and readily-available equipment: a consumer-grade radio receiver or a Software Defined Radio USB dongle. The setup is compact and can operate untethered; it can be easily concealed, e.g., inside pita bread. Common laptops, and popular implementations of RSA and ElGamal encryptions, are vulnerable to this attack, including those that implement the decryption using modern exponentiation algorithms such as sliding-window, or even its side-channel resistant variant, fixed-window (m-ary) exponentiation.We successfully extracted keys from laptops of various models running GnuPG (popular open source encryption software, implementing the OpenPGP standard), within a few seconds. The attack sends a few carefully-crafted ciphertexts, and when these are decrypted by the target computer, they trigger the occurrence of specially-structured values inside the decryption software. These special values cause observable fluctuations in the electromagnetic field surrounding the laptop, in a way that depends on the pattern of key bits (specifically, the key-bits window in the exponentiation routine). The secret key can be deduced from these fluctuations, through signal processing and cryptanalysis.
The attack can be mounted using various experimental setups:
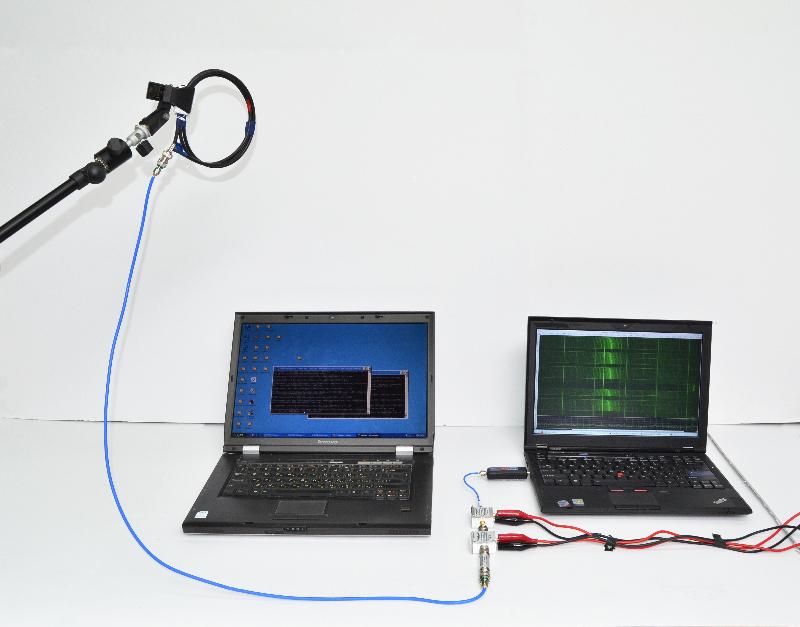
- Software Defined Radio (SDR) attack. We constructed a simple shielded loop antenna (15 cm in diameter) using a coaxial cable. We then recorded the signal produced by the probe using an SDR receiver. The electromagnetic field, thus measured, is affected by ongoing computation, and our attacks exploit this to extract RSA and ElGamal keys, within a few seconds.
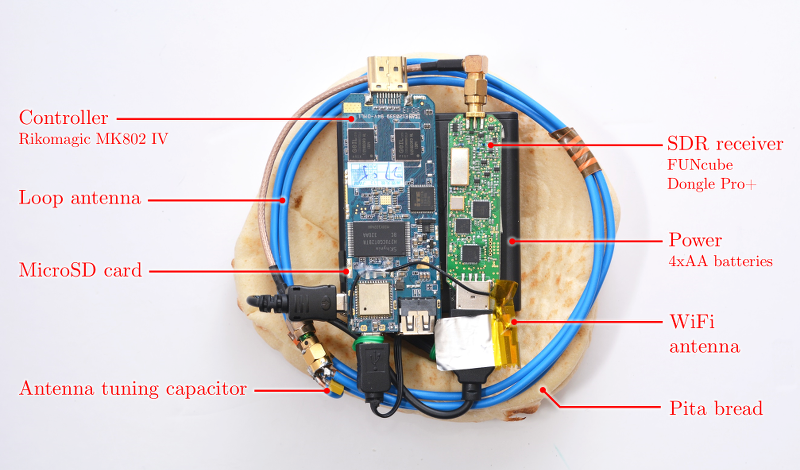
- Untethered SDR attack. Setting out to simplify and shrink the analog and analog-to-digital portion of the measurement setup, we constructed the Portable Instrument for Trace Acquisition (Pita), which is built of readily-available electronics and food items (see instructions here). Pita can be operated in two modes. In online mode, it connects wirelessly to a nearby observation station via WiFi, and provides real-time streaming of the digitized signal. The live stream helps optimize probe placement and allows adaptive recalibration of the carrier frequency and SDR gain adjustments. In autonomous mode, Pita is configured to continuously measure the electromagnetic field around a designated carrier frequency, and records the digitized signal into an internal microSD card for later retrieval, by physical access or via WiFi. In both cases, signal analysis is done offline, on a workstation.
- Consumer radio attack. Despite its low price and compact size, assembly of the Pita device still requires the purchase of an SDR device. As discussed, the leakage signal is modulated around a carrier circa 1.7 MHz, located in the range of the commercial AM radio frequency band. We managed to use a plain consumer-grade radio receiver to acquire the desired signal, replacing the magnetic probe and SDR receiver. We then recorded the signal by connecting it to the microphone input of an HTC EVO 4G smartphone.
Q&A
Q1: What information is leaked by the electromagnetic emanations from computers?
This depends on the specific computer hardware. We have tested numerous laptop computers, and found the following:- In almost all machines, it is possible to tell, with sub-millisecond precision, whether the computer is idle or performing operations.
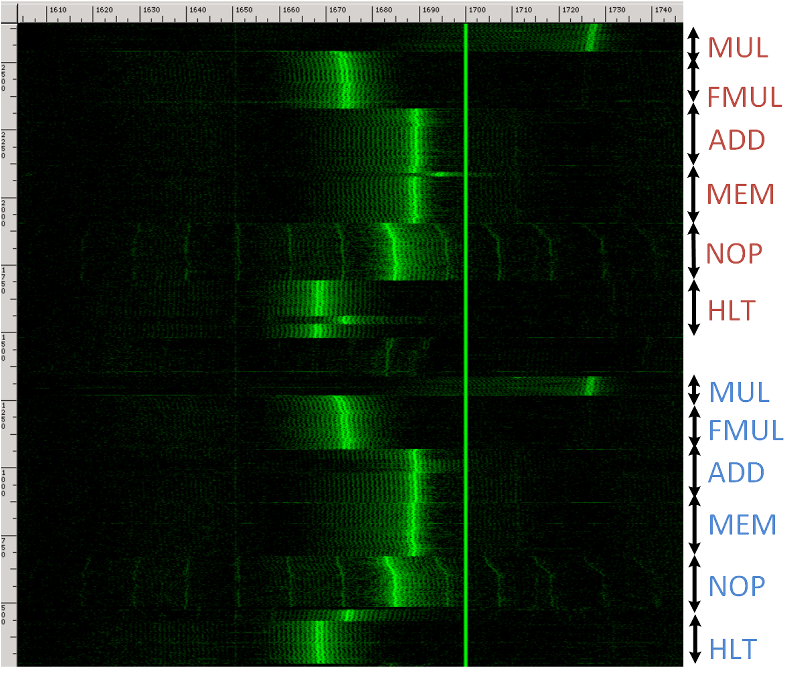
- On many machines, it is moreover possible to distinguish different patterns of CPU operations and different programs.
- Using GnuPG as our study case, we can, on some machines:
- distinguish between the spectral signatures of different RSA secret keys (signing or decryption), and
- fully extract decryption keys, by measuring the laptop's electromagnetic emanations during decryption of a chosen ciphertext.
Q2: Why does this happen?
Different CPU operations have different power requirements. As different computations are performed during the decryption process, different electrical loads are placed on the voltage regulator that provides the processor with power. The regulator reacts to these varying loads, inadvertently producing electromagnetic radiation that propagates away from the laptop and can be picked up by a nearby observer. This radiation contains information regarding the CPU operations used in the decryption, which we use in our attack.Q3: How can I construct such a setup?
- Software Defined Radio (SDR) attack. The main component in the first setup is a FUNcube Dongle Pro+ SDR receiver. Numerous cheap alternatives exist, including ``rtl-sdr'' USB receivers based on the Realtek RTL2832U chip (originally intended for DVB-T television receivers) with a suitable tuner and upconverter; the Soft66RTL2 dongle is one such example.
- Untethered SDR attack. The Pita device uses an unshielded loop antenna made of plain copper wire, wound into 3 turns of diameter 13 cm, with a tuning capacitor chosen to maximize sensitivity at 1.7 MHz (which is where the key-dependent leakage signal is present). These are connected to the aforementioned FUNcube Dongle Pro+ SDR receiver. We control the SDR receiver using a small embedded computer, the Rikomagic MK802 IV. This is an inexpensive Android TV dongle based on the Rockchip RK3188 ARM SoC. It supports USB host mode, WiFi and flash storage. We replaced the operating system with Debian Linux, in order to run our software, which operates the SDR receiver via USB and communicates via WiFi. Power is provided by 4 NiMH AA batteries, which suffice for several hours of operation.
- Consumer radio attack. We have tried many consumer-grade radio receivers and smartphones with various results. Best results were achieved using a "Road Master" brand consumer radio connected to the microphone jack of an HTC EVO 4G smartphone, sampling at 48 kHz, through an adapter cable. The dedicated line-in inputs of PCs and sound cards do not require such an adapter, and yield similar results.
Q4: What is the range of the attack?
In order to extend the attack range, we added a 50dB gain stage using a pair of inexpensive low-noise amplifiers (Mini-Circuits ZFL-500LN+ and ZFL-1000LN+ in series, 175$ total). We also added a low-pass filter before the amplifiers. With this enhanced setup, the attack can be mounted from 50 cm away. Using better antennas, amplifiers and digitizers, the range can be extended even further.Q5: What if I can't get physically close enough to the target computer?
There are still attacks that can be mounted from large distances.- Laptop-chassis potential, measured from the far end of virtually any shielded cable connected to the laptop (such as Ethernet, USB, HDMI and VGA cables) can be used for key-extraction, as we demonstrated in a paper presented at CHES'14.
- Acoustic emanations (sound), measured via a microphone, can also be used to extract keys from a range of several meters, as we showed in a paper presented at CRYPTO'14.
Q6: What's new since your previous papers?
- Cheap experimental setup. The previous papers required either a long attack time (about an hour) when using inexpensive equipment, or a fast attack (a few seconds) but using an expensive setup. In this paper we achieve the best of both, presenting an experimental setup which extracts keys quickly while remaining simple and cheap to construct.
- New cryptographic technique addressing modern implementations. In the previous papers we attacked the naive square-and-multiply exponentiation algorithm and the square-and-always-multiply variant (which reduces side-channel leakage). However, most modern implementations utilize faster exponentiation algorithms: sliding-window, or for better side-channel resistance, m-ary exponentiation. In this paper we demonstrate a low-bandwidth attack on the latter two algorithms, extracting their secret keys.
Q7: How can low-frequency (kHz) leakage provide useful information about a much faster (GHz) computation?
We use two main techniques.- Leakage self-amplification. Individual CPU operations are too fast for our measurement equipment to pick up, but long operations (e.g., modular exponentiation in RSA and ElGamal) can create a characteristic (and detectable) spectral signature over many milliseconds. Using a suitably chosen ciphertext, we are able to use the algorithm's own code to amplify its own key leakage, creating very drastic changes, detectable even by low-bandwidth means.
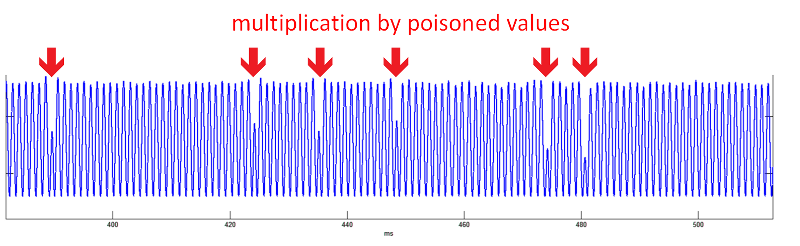
- Data-dependent leakage. While most implementations (such as GnuPG) attempt to decouple the secret key from the sequence of performed operations, the operands to these operations are key-dependent and often not fully randomized. The attacker can thus attempt to craft special inputs (e.g., ciphertexts to be decrypted) to the cryptographic algorithm that "poison" the intermediate values inside the algorithm, producing a distinct leakage pattern when used as operands during the algorithm's execution. Measuring leakage during such a poisoned execution can reveal in which operations the operands occurred, and thus leak secret-key information.
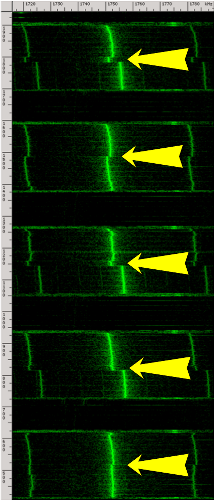
For example, the figure presents the leakage signal (after suitable processing) of an ElGamal decryption. The signal appears to be mostly regular in shape, and each peak corresponds to a multiplication performed by GnuPG's exponentiation routine. However, an occasional "dip" (low peak) can be seen. These dips correspond to a multiplication by a poisoned value performed within the exponentiation routine.
Q8: How vulnerable is GnuPG now?
We have disclosed our attack to GnuPG developers under CVE-2014-3591, suggested suitable countermeasures, and worked with the developers to test them. GnuPG 1.4.19 and Libgcrypt 1.6.3 (which underlies GnuPG 2.x), containing these countermeasures and resistant to the key-extraction attack described here, were released concurrently with the first public posting of these results.Q9: How vulnerable are other algorithms and cryptographic implementations?
This is an open research question. Our attack requires careful cryptographic analysis of the implementation, which so far has been conducted only for the GnuPG 1.x implementation of RSA and ElGamal. Implementations using ciphertext blinding (a common side-channel countermeasure) appear less vulnerable.Q10: Is there a realistic way to perform a chosen-ciphertext attack on GnuPG?
GnuPG is often invoked to decrypt externally-controlled inputs, fed into it by numerous frontends, via emails, files, chat and web pages. The list of GnuPG frontends contains dozens of such applications, each of them can be potentially used in order to make the target decrypt the chosen ciphertexts required by our attack. As a concrete example, Enigmail (a popular plugin to the Thunderbird e-mail client) automatically decrypts incoming e-mail (for notification purposes) using GnuPG. An attacker can e-mail suitably-crafted messages to the victims (using the OpenPGP and PGP/MIME protocols), wait until they reach the target computer, and observe the target's EM emanations during their decryption (as shown above), thereby closing the attack loop. We have empirically verified that such an injection method does not have any noticeable effect on the leakage signal produced by the target laptop. GnuPG's Outlook plugin, GpgOL also did not seem to alter the target's leakage signal.Q11: What countermeasures are available?
Physical mitigation techniques of electromagnetic radiation include Faraday cages. However, inexpensive protection of consumer-grade PCs appears difficult. Alternatively, the cryptographic software can be changed, and algorithmic techniques employed to render the emanations less useful to the attacker. These techniques ensure that the rough-scale behavior of the algorithm is independent of the inputs it receives; they usually carry some performance penalty, but are often used in any case to thwart other side-channel attacks. This is what we helped implement in GnuPG (see Q8).Q12: Why software countermeasures? Isn't it the hardware's responsibility to avoid physical leakage?
It is tempting to enforce proper layering and decree that preventing physical leakage is the responsibility of the physical hardware. Unfortunately, such low-level leakage prevention is often impractical due to the very bad cost vs. security tradeoff: (1) any leakage remnants can often be amplified by suitable manipulation at the higher levels, as we indeed do in our chosen-ciphertext attack; (2) low-level mechanisms try to protect all computation, even though most of it is insensitive or does not induce easily-exploitable leakage; and (3) leakage is often an inevitable side effect of essential performance-enhancing mechanisms (e.g., consider cache attacks).Application-layer, algorithm-specific mitigation, in contrast, prevents the (inevitably) leaked signal from bearing any useful information. It is often cheap and effective, and most cryptographic software (including GnuPG and libgcrypt) already includes various sorts of mitigation, both through explicit code and through choice of algorithms. In fact, the side-channel resistance of software implementations is nowadays a major concern in the choice of cryptographic primitives, and was an explicit evaluation criterion in NIST's AES and SHA-3 competitions.
Q13: What does the RSA leakage look like?
Here is an example of a spectrogram (which plots the measured power as a function of time and frequency) for a recording of GnuPG decrypting the same ciphertext using different randomly generated RSA keys:In this spectrogram, the horizontal axis (frequency) spans ranges from 1.72 MHz to 1.78 MHz, and the vertical axis (time) spans 1.2 seconds. Each yellow arrow points to the middle of a GnuPG RSA decryption. It is easy to see where each decryption starts and ends. Notice the change in the middle of each decryption operation, spanning several frequency bands. This is because, internally, each GnuPG RSA decryption first exponentiates modulo the secret prime p and then modulo the secret prime q, and we can actually see the difference between these stages. Moreover, each of these pairs looks different because each decryption uses a different key. So in this example, by simply observing electromagnetic emanations during decryption operations, using the setup from this figure, we can distinguish between different secret keys.
Q14: What is the difference between your attack and the recent cache attack by Yarom et al.?
Cache side channel (timing cross-talk between processes or virtual machines) apply to scenarios where the attacker can execute code on the same physical machine as the targeted process (e.g., in shared computers, such as Infrastructure as a Service cloud computing).Our attack exploits
Acknowledgments
We thank Werner Koch, lead developer of GnuPG, for the prompt response to our disclosure and the productive collaboration in adding suitable countermeasures. Erik Olson's Baudline signal analysis software was used for some of the analysis.
This work was sponsored by the Check Point Institute for Information Security; by the European Union's Tenth Framework Programme (FP10/2010-2016) under grant agreement 259426 ERC-CaC; by the Leona M. & Harry B. Helmsley Charitable Trust; by the Israeli Ministry of Science and Technology; by the Israeli Centers of Research Excellence I-CORE Program (center 4/11); and by NATO's Public Diplomacy Division in the Framework of "Science for Peace".
https://www.tau.ac.il/~tromer/radioexp/
This work was sponsored by the Check Point Institute for Information Security; by the European Union's Tenth Framework Programme (FP10/2010-2016) under grant agreement 259426 ERC-CaC; by the Leona M. & Harry B. Helmsley Charitable Trust; by the Israeli Ministry of Science and Technology; by the Israeli Centers of Research Excellence I-CORE Program (center 4/11); and by NATO's Public Diplomacy Division in the Framework of "Science for Peace".
https://www.tau.ac.il/~tromer/radioexp/
Tuesday, June 16, 2015
EXPLOSIVES TEXTILES
welcome back to war! Today's subject as I already said yesterday explosive textiles:
"Rayon is a fiber produced from recycled wood pulp or bamboo cellulose processed by a combination of many chemicals involving carbon disulphide, sulfuric acid, ammonia, acetone and caustic soda to bear regular washing and constant wearing"
"Acrylic’s manufacturing process, if not properly monitored can result in an explosion. Acrylic fibers are highly inflammable and not easy recyclable nor biodegradable in the environment. "
ITS NEED AN ORGANIC SOLVENT:
2-Butanol, or sec-butanol, is an organic compound with formula CH3CH(OH)CH2CH3. This secondary alcohol is a flammable, colorless liquid that is soluble in 3 parts water and completely miscible with polar organic solvents such as ethers and other alcohols. It is produced on a large scale, primarily as a precursor to the industrial solvent methyl ethyl ketone. 2-Butanol is chiral and thus can be obtained as either of two stereoisomers designated as (R)-(−)-2-butanol and (S)-(+)-2-butanol. It is normally found as an equal mixture of the two stereoisomers — a racemic mixture
precision solvent cleaners, which are mixtures of various hydrocarbon solvents
"Rayon is a fiber produced from recycled wood pulp or bamboo cellulose processed by a combination of many chemicals involving carbon disulphide, sulfuric acid, ammonia, acetone and caustic soda to bear regular washing and constant wearing"
"Acrylic’s manufacturing process, if not properly monitored can result in an explosion. Acrylic fibers are highly inflammable and not easy recyclable nor biodegradable in the environment. "
ITS NEED AN ORGANIC SOLVENT:
2-Butanol, or sec-butanol, is an organic compound with formula CH3CH(OH)CH2CH3. This secondary alcohol is a flammable, colorless liquid that is soluble in 3 parts water and completely miscible with polar organic solvents such as ethers and other alcohols. It is produced on a large scale, primarily as a precursor to the industrial solvent methyl ethyl ketone. 2-Butanol is chiral and thus can be obtained as either of two stereoisomers designated as (R)-(−)-2-butanol and (S)-(+)-2-butanol. It is normally found as an equal mixture of the two stereoisomers — a racemic mixture
precision solvent cleaners, which are mixtures of various hydrocarbon solvents
Saturday, June 13, 2015
RF Safe-Stop Shuts Down Car Engines With Radio Pulse
An anonymous reader writes with news of a device built by a company in the U.K. which uses pulses of electromagnetic energy to disrupt the electronic systems of modern cars, causing them to shut down and cut the engine. Here's a description of how it works: "At one end of a disused runway, E2V assembled a varied collection of second-hand cars and motorbikes in order to test the prototype against a range of vehicles. In demonstrations seen by the BBC a car drove towards the device at about 15mph (24km/h). As the vehicle entered the range of the RF Safe-stop, its dashboard warning lights and dials behaved erratically, the engine stopped and the car rolled gently to a halt. Digital audio and video recording devices in the vehicle were also affected.''It's a small radar transmitter,' said Andy Wood, product manager for the machine. 'The RF [radio frequency] is pulsed from the unit just as it would be in radar, it couples into the wiring in the car and that disrupts and confuses the electronics in the car causing the engine to stall.'
http://news.slashdot.org/story/13/12/03/1919230/rf-safe-stop-shuts-down-car-engines-with-radio-pulse
Where to Buy :
guided wave radar transmitter :)
http://dir.indiamart.com/impcat/radar-level-transmitter.HTML
http://news.slashdot.org/story/13/12/03/1919230/rf-safe-stop-shuts-down-car-engines-with-radio-pulse
Where to Buy :
guided wave radar transmitter :)
http://dir.indiamart.com/impcat/radar-level-transmitter.HTML
Wednesday, June 10, 2015
Tuesday, June 9, 2015
Defense Distributed: Successful test fire of first 3D printed pistol (video)
Defense Distributed has released a video of the successful test firing by hand of their first complete 3D printed pistol, the "Liberator". The Liberator has only one metal part, the firing pin, made from a common nail. In the video, Cody Wilson is shown firing the pistol by hand, to dramatically illustrate his faith in the design. The Liberator is a single shot pistol in .380 (9X17) caliber. While firearms have been made in home workshops ever since they have been in existence, the ability to download computer files and have a computer controlled machine print all the parts to a functioning firearm has caught the public attention. Dean Weingarten, Defense Distributed Distributor
 Defense Distributed has made a habit of provoking government regulators in its quest to bring 3D-printed firearms to home hobbyists. The most recent loophole exploited by Defense Distributed is once again about creating a working firearm at home, but unlike the 3D-printed Liberator pistol, this one isn’t made of plastic. The Ghost Gunner is a small CNC milling machine that costs a mere $1200 and is capable of spitting out an aluminum lower receiver for an AR-15 rifle. This device allows people with no gunsmith training to assemble a working assault rifle at home with no licensing or serial number — and it’s completely legal.
Defense Distributed has made a habit of provoking government regulators in its quest to bring 3D-printed firearms to home hobbyists. The most recent loophole exploited by Defense Distributed is once again about creating a working firearm at home, but unlike the 3D-printed Liberator pistol, this one isn’t made of plastic. The Ghost Gunner is a small CNC milling machine that costs a mere $1200 and is capable of spitting out an aluminum lower receiver for an AR-15 rifle. This device allows people with no gunsmith training to assemble a working assault rifle at home with no licensing or serial number — and it’s completely legal.
The Ghost Gunner itself is a small box about one foot on each side. Inside is an Arduino controller and a custom-designed spindle that holds a steel carbide drill bit. It works like any other CNC machine — the drill spins up and moves in three dimensions to carve items out of blocks of metal. However, this machine is specifically intended to make an AR-15 lower receiver. That’s the part of a gun that connects the stock, barrel, and magazine. You could say it’s the “gun” part of a gun. It’s also the part that’s regulated by the ATF and assigned a serial number. Selling it without a license is illegal, but making it yourself is perfectly fine. An untraceable gun built without a serial number is often called a “ghost gun” by gun control advocates, so of course Defense Distributed borrowed the term to ruffle feathers.
This is only the latest example of Defense Distributed pushing the bounds of home manufacturing technology to make a point. The organization is run by founder Cody Wilson, who isn’t shy about explaining his radically libertarian ideals. Allowing everyone to create an assault rifle with a few clicks is his way of showing that technology can always evade regulation and render the state obsolete. If a few people are shot by ghost guns, that’s just the price we have to pay for freedom, according to Wilson.
3D printing guns like the Liberator was more of a statement — it showed that a new era of manufacturing tech is upon us. Of course, no one would ever want to use a plastic gun if given the choice. The Liberator is prone to failure (video below), and usually only manages a few poorly aimed shots. In designing a cheap CNC machine specifically to make gun parts, Defense Distributed is delivering a viable weapon (other CNC mills cost many thousands of dollars). If you can make a lower receiver, all the other parts can be ordered online cheaply and legally.
The Ghost Gunner is capable of making anything that fits in the build envelope, as long as it’s created with Defense Distributed’s Physibles Development SDK (pDev) and distributed as a .dd file. In that respect, it’s not much different than any number of 3D printers. This is an entirely new era in the manufacturing of real world objects, in both plastic and metal. It used to be that you needed training as a gunsmith to make your own firearm, but that’s no longer the case. Whether or not you agree with Defense Distributed on the value of untraceable firearms in a free society, this is happening and regulation is miles behind the technological curve.
http://www.extremetech.com/extreme/191388-1200-the-price-of-legally-3d-printing-your-own-metal-ar-15-rifle-at-home
Fadal VMC4020 CNC Vertical Machining Center Milling Machine 3 Axis
Defense Distributed has released a video of the successful test firing by hand of their first complete 3D printed pistol, the "Liberator". The Liberator has only one metal part, the firing pin, made from a common nail. In the video, Cody Wilson is shown firing the pistol by hand, to dramatically illustrate his faith in the design. The Liberator is a single shot pistol in .380 (9X17) caliber. While firearms have been made in home workshops ever since they have been in existence, the ability to download computer files and have a computer controlled machine print all the parts to a functioning firearm has caught the public attention. Dean Weingarten, Defense Distributed Distributor
1 comment:
- Scotty said...
- A metal detector could sense the steel firing pin nail and/or the bullet itself if set to high sensitivity. The entire weapon would be detected by most other types of body scanners. The point is - it's not guaranteed to make it through the current screening technology. As for legality, all existing gun ownership laws would still apply. For instance: If you print and assemble one in Massachusetts without a license, background check, and required training, you will be arrested if caught with it in your home or possession. The gun's printed material cannot withstand the heat and wear of repeated firing, particularly with more powerful rounds where chamber pressures may exceed 35,000 psi. Rifling, necessary for accuracy at more than a few yards, is not feasible and will disappear after the first few firings. (if not the first) Finally, if you want a durable gun and are not willing to get it legally, well, just ask a bank robber how it's done. But if you're willing or able to secure whatever permit your state requires, then pick up a used pistol at the local gun store for a quarter the cost of a printer. I'm as disgusted by the over-reaching nature of the federal government as most gun owners, but really - this is not the answer
- http://gunwatch.blogspot.pt/2013/05/defense-distributed-successful-test.HTML
$1200: The price of (legally) 3D printing your own metal AR-15 rifle at home
- By Ryan Whitwam on October 2, 2014 at 1:10 pm
The Ghost Gunner itself is a small box about one foot on each side. Inside is an Arduino controller and a custom-designed spindle that holds a steel carbide drill bit. It works like any other CNC machine — the drill spins up and moves in three dimensions to carve items out of blocks of metal. However, this machine is specifically intended to make an AR-15 lower receiver. That’s the part of a gun that connects the stock, barrel, and magazine. You could say it’s the “gun” part of a gun. It’s also the part that’s regulated by the ATF and assigned a serial number. Selling it without a license is illegal, but making it yourself is perfectly fine. An untraceable gun built without a serial number is often called a “ghost gun” by gun control advocates, so of course Defense Distributed borrowed the term to ruffle feathers.
This is only the latest example of Defense Distributed pushing the bounds of home manufacturing technology to make a point. The organization is run by founder Cody Wilson, who isn’t shy about explaining his radically libertarian ideals. Allowing everyone to create an assault rifle with a few clicks is his way of showing that technology can always evade regulation and render the state obsolete. If a few people are shot by ghost guns, that’s just the price we have to pay for freedom, according to Wilson.
3D printing guns like the Liberator was more of a statement — it showed that a new era of manufacturing tech is upon us. Of course, no one would ever want to use a plastic gun if given the choice. The Liberator is prone to failure (video below), and usually only manages a few poorly aimed shots. In designing a cheap CNC machine specifically to make gun parts, Defense Distributed is delivering a viable weapon (other CNC mills cost many thousands of dollars). If you can make a lower receiver, all the other parts can be ordered online cheaply and legally.
The Ghost Gunner is capable of making anything that fits in the build envelope, as long as it’s created with Defense Distributed’s Physibles Development SDK (pDev) and distributed as a .dd file. In that respect, it’s not much different than any number of 3D printers. This is an entirely new era in the manufacturing of real world objects, in both plastic and metal. It used to be that you needed training as a gunsmith to make your own firearm, but that’s no longer the case. Whether or not you agree with Defense Distributed on the value of untraceable firearms in a free society, this is happening and regulation is miles behind the technological curve.
http://www.extremetech.com/extreme/191388-1200-the-price-of-legally-3d-printing-your-own-metal-ar-15-rifle-at-home
Fadal VMC4020 CNC Vertical Machining Center Milling Machine 3 Axis
Friday, June 5, 2015
NON DETECTABLE GLOCK 7
welcome back to war! Today's subject, ceramic guns non detectable! Ok, everybody knows here I've been trought the Glock 7, everybody wants to ge the hands on smile emoticon Now, we already have a 3D design for a Glock piece, but we didn't have teh right material, which the Glock 7 is made of, so here it is:
How It Works
Carbide wear is due to micro-fracturing, macro-fracturing, grain pull out, corrosion of the binder, adhesion between the carbide and the material being cut, and tribological functions which are similar to a naturally occurring electro-etching.
Cermet II technology uses a variety of carbides such a titanium carbide, tungsten carbide, Tantalum carbide, Niobium carbide and others. Steel is iron with a very small amount of carbide but it is very different than plain iron. The addition of a very small amount of the right material can make a huge difference in carbide performance as well.
Cermet II grades also use unique binder formulations. Cobalt is a good binder material and is used in standard grades. It was the first binder used and is still easiest to use. However cobalt is pure metal and is subject to chemical attack. Part of the secret of our Cermet II grades is to chemically alloy special binders with a proprietary metalloid which makes the cobalt binder non-reactive so it doesn’t corrode. It also greatly strengthens the binder so grinds aren’t pulled out.
Cermet II grades have special binder properties so that they behave more as a solid piece of material than as a cemented piece of material. Think of a steel alloy as compared to concrete.
Grain Size
The most important reason for this widening of the spectrum of available WC grades is that, besides those variations achieved by cobalt contents and some carbide additives, the properties of WC-Co hardmetals such as hardness, toughness, strength, modulus of elasticity, abrasion resistance and thermal conductivity can be widely varied by means of the WC grain size. While the spectrum of available WC grain sizes ranged from 2.0 to 5.0 µm in the early days of the hardmetal industry in the mid 1920’s, the grain sizes of WC powders now used in hardmetals range from 0.15 µm to 50 µm, or even 150 µm for some very special applications.
Grain Size
The history of tungsten carbide powder metallurgy, and especially that of the hardmetal industry, is characterized by a steadily widening range of available grain sizes for processing in the industry; while, at the same time, the grain size distribution for each grade of WC powder became narrower and narrower.
The most important reason for this widening of the spectrum of available WC grades is that, besides those variations achieved by cobalt contents and some carbide additives, the properties of WC-Co hardmetals such as hardness, toughness, strength, abrasion resistance and thermal conductivity can be widely varied by means of the WC grain size. While the spectrum of available WC grain sizes ranged from 2.0 to 5.0 µm in the early days of the hardmetal industry in the mid 1920’s, the grain sizes of WC powders now used in hardmetals range from 0.5 µm to 50 µm, or even 150 µm for some very special applications.
The first submicron hardmetals were launched on the market in the late 1970s and, since this time, the micro-structures of such hardmetals have become finer and finer. The main interest in hardmetals with such finer grain sizes derives from the understanding that hardness and wear resistance increase with decreasing WC grain size.
With optimum grade selection, sub micron grain size tungsten carbide can be sharpened to a razor edge without the inherent brittleness frequently associated with conventional carbide. Although not as shock-resistant as steel, carbide is extremely wear-resistant, with hardness equivalent to Rc 75-80. Blade life of at least 50X conventional blade steels can be expected if chipping and breakage is avoided.
Advanced Manufacturing Techniques
Better, cleaner powder has been achieved through improved solvent extraction in tungsten chemistry as well as new techniques in hydrogen reduction and carburization to improve the purity and uniformity of tungsten and tungsten carbide powder.
New powder milling, spray drying and sintering techniques have resulted in improved hardmetal properties and performance. Notably, the continuous improvement of vacuum sintering technology and, starting from the late 1980’s, hot isostatic pressure sintering (SinterHIP) led to new standards in hardmetal quality.
http://www.carbideprocessors.com/pages/carbide-parts/making-cermet-material.html
Making Cermet II Materials
What follows are some explanations of how to make advanced carbide. These are pretty short explanations but they will give an idea of all that is possible.
Obviously we use different techniques for different grades and applications. We have compiled a great deal of infomation on Carbide and Advanced Materials in our Tool Tipping Index. How It Works
Carbide wear is due to micro-fracturing, macro-fracturing, grain pull out, corrosion of the binder, adhesion between the carbide and the material being cut, and tribological functions which are similar to a naturally occurring electro-etching.
Cermet II technology uses a variety of carbides such a titanium carbide, tungsten carbide, Tantalum carbide, Niobium carbide and others. Steel is iron with a very small amount of carbide but it is very different than plain iron. The addition of a very small amount of the right material can make a huge difference in carbide performance as well.
Cermet II grades also use unique binder formulations. Cobalt is a good binder material and is used in standard grades. It was the first binder used and is still easiest to use. However cobalt is pure metal and is subject to chemical attack. Part of the secret of our Cermet II grades is to chemically alloy special binders with a proprietary metalloid which makes the cobalt binder non-reactive so it doesn’t corrode. It also greatly strengthens the binder so grinds aren’t pulled out.
Cermet II grades have special binder properties so that they behave more as a solid piece of material than as a cemented piece of material. Think of a steel alloy as compared to concrete.
Grain Size
The most important reason for this widening of the spectrum of available WC grades is that, besides those variations achieved by cobalt contents and some carbide additives, the properties of WC-Co hardmetals such as hardness, toughness, strength, modulus of elasticity, abrasion resistance and thermal conductivity can be widely varied by means of the WC grain size. While the spectrum of available WC grain sizes ranged from 2.0 to 5.0 µm in the early days of the hardmetal industry in the mid 1920’s, the grain sizes of WC powders now used in hardmetals range from 0.15 µm to 50 µm, or even 150 µm for some very special applications.
Grain Size
The history of tungsten carbide powder metallurgy, and especially that of the hardmetal industry, is characterized by a steadily widening range of available grain sizes for processing in the industry; while, at the same time, the grain size distribution for each grade of WC powder became narrower and narrower.
The most important reason for this widening of the spectrum of available WC grades is that, besides those variations achieved by cobalt contents and some carbide additives, the properties of WC-Co hardmetals such as hardness, toughness, strength, abrasion resistance and thermal conductivity can be widely varied by means of the WC grain size. While the spectrum of available WC grain sizes ranged from 2.0 to 5.0 µm in the early days of the hardmetal industry in the mid 1920’s, the grain sizes of WC powders now used in hardmetals range from 0.5 µm to 50 µm, or even 150 µm for some very special applications.
The first submicron hardmetals were launched on the market in the late 1970s and, since this time, the micro-structures of such hardmetals have become finer and finer. The main interest in hardmetals with such finer grain sizes derives from the understanding that hardness and wear resistance increase with decreasing WC grain size.
With optimum grade selection, sub micron grain size tungsten carbide can be sharpened to a razor edge without the inherent brittleness frequently associated with conventional carbide. Although not as shock-resistant as steel, carbide is extremely wear-resistant, with hardness equivalent to Rc 75-80. Blade life of at least 50X conventional blade steels can be expected if chipping and breakage is avoided.
Advanced Manufacturing Techniques
Better, cleaner powder has been achieved through improved solvent extraction in tungsten chemistry as well as new techniques in hydrogen reduction and carburization to improve the purity and uniformity of tungsten and tungsten carbide powder.
New powder milling, spray drying and sintering techniques have resulted in improved hardmetal properties and performance. Notably, the continuous improvement of vacuum sintering technology and, starting from the late 1980’s, hot isostatic pressure sintering (SinterHIP) led to new standards in hardmetal quality.
http://www.carbideprocessors.com/pages/carbide-parts/making-cermet-material.html
Subscribe to:
Comments (Atom)
Intel Portugal cyber cibercrime gov pt ministério público PGR login
https://cibercrime.ministeriopublico.pt/en/user/login https://webmail.pgr.pt/owa/auth/swivel/ChangePIN.aspx?redirect=/owa/auth/logon.aspx