Optical Emission Security – Frequently Asked Questions
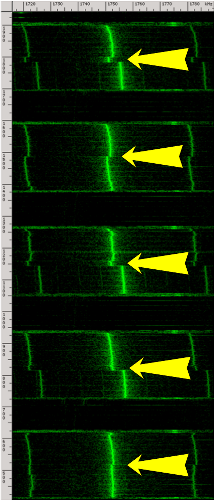
Markus Kuhn In the paperOptical Time-Domain Eavesdropping Risks of CRT Displays,I describe a new eavesdropping technique that reconstructs text on computer screens from diffusely reflected light. This publication resulted in some wide media attention (BBC, New Scientist,Wired, Reuters, Slashdot). Here are answers to some of the questions I have received, along with some introductory information for interested readers looking for a more highlevel summary than the full paper, which was mainly written for an audience of hardware-security and optoelectronics professionals. Q: How does this new eavesdropping technique work? To understand what is going on, you have to recall how a cathode-ray display works. An electron beam scans across the screen surface at enormous speed (tens of kilometers per second) and targets one pixel after another. It targets this way tens or hundreds of millions of pixels every second to convert electron energy into light. Even though each pixel shows an afterglow for longer than the time the electron beam needs to refresh an entire line of pixels, each pixel is much brighter while the e-beam hits it than during the remaining afterglow. My discovery of this very short initial brightness in the light decay curve of a pixel is what makes this eavesdropping technique work. An image is created on the CRT surface by varying the electron beam intensity for each pixel. The room in which the CRT is located is partially illuminated by the pixels. As a result, the light in the room becomes a measure for the electron beam current. In particular, there is a little invisible ultrafast flash each time the electron beam refreshes a bright pixel that is surrounded by dark pixels on its left and right. So if you measure the brightness of a wall in this room with a very fast photosensor, and feed the result in another monitor that receives the exact same synchronization signals for steering its electron beam, you get to see an image like this:
2002 IEEE Symposium on Security and Privacy, Berkeley, California, May 2002.
- The eavesdropped videosignal is periodic over at least a few seconds, therefore periodic averaging over a few hundred frames can help significantly to reduce the noise.
- If you know exactly what font is used, many of the equalization and symbol detection techniques used in modems or pattern recognition applications can be applied to recover the text (remote optical character recognition).
- Optical filters can eliminate other colours from background light.
- A large sensor aperture (telelens, telescope) can improve the photon count.
- Reception is difficult if not impossible from well-lit rooms, in which CRTs do not make a visible contribution to the ambient illumination. Don't work in the dark.
- No not assume that etched or frosted glass surfaces prevent this technique if there is otherwise a direct line of sight to the screen surface.
- This particular eavesdropping technique is not applicable to LCDs and other flat-panel displays that refresh all pixels in a row simultaneously.
- Make sure, nobody can install eavesdropping equipment within a few hundred meters line-of-sight to your window.
- Use a screen saver that removes confidential information from the monitor in your absence.
created 2002-03-05 – last modified 2004-11-29 – http://www.cl.cam.ac.uk/~mgk25/emsec/optical-faq.html



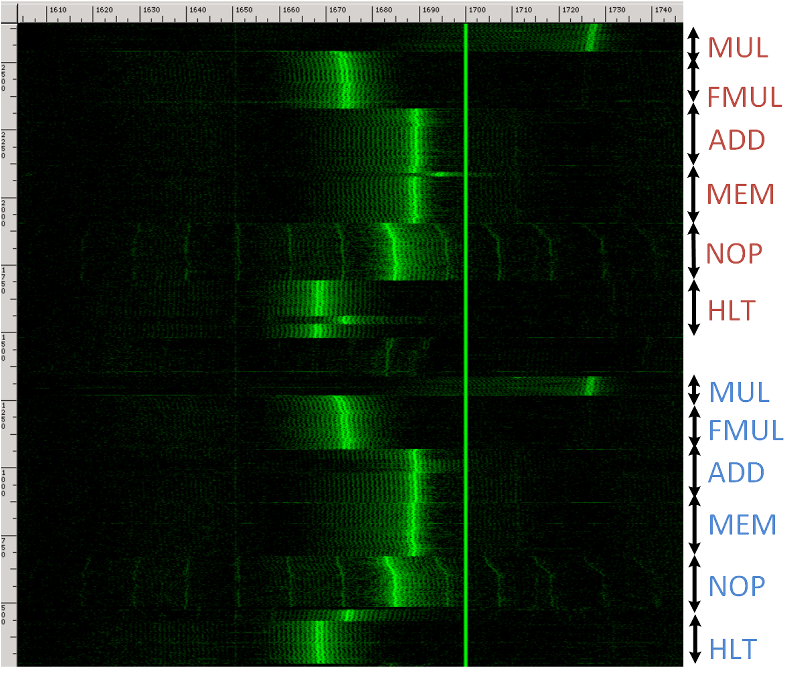
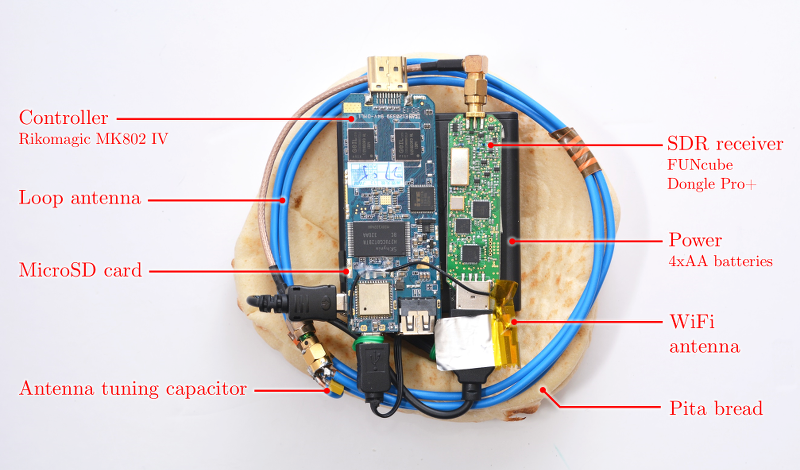
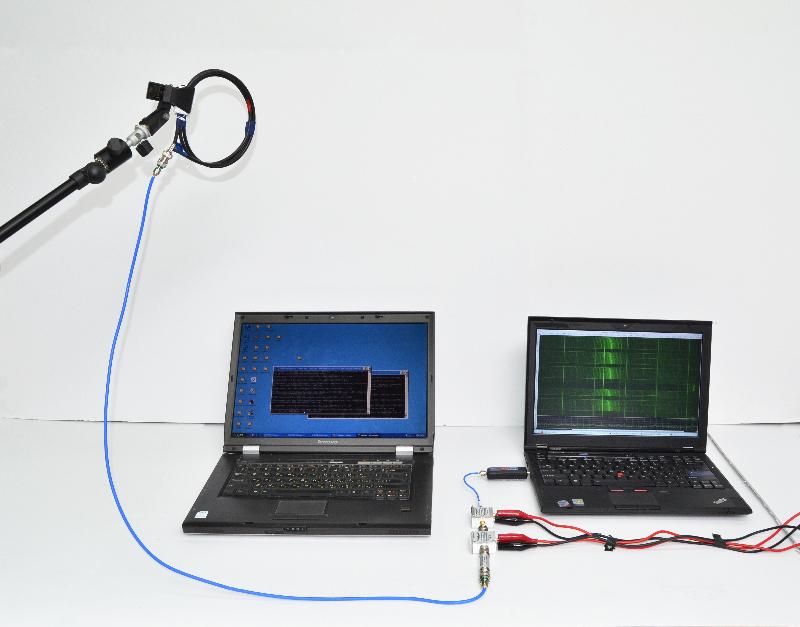
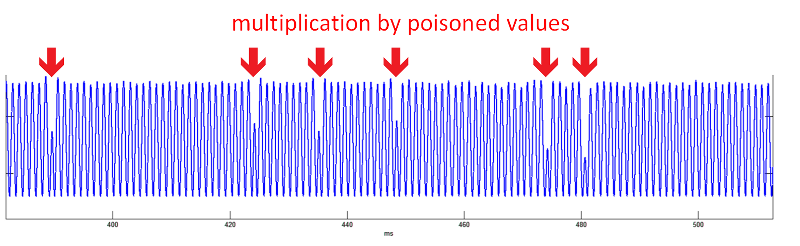








1 comment:
$1200: The price of (legally) 3D printing your own metal AR-15 rifle at home
Share This article
The Ghost Gunner itself is a small box about one foot on each side. Inside is an Arduino controller and a custom-designed spindle that holds a steel carbide drill bit. It works like any other CNC machine — the drill spins up and moves in three dimensions to carve items out of blocks of metal. However, this machine is specifically intended to make an AR-15 lower receiver. That’s the part of a gun that connects the stock, barrel, and magazine. You could say it’s the “gun” part of a gun. It’s also the part that’s regulated by the ATF and assigned a serial number. Selling it without a license is illegal, but making it yourself is perfectly fine. An untraceable gun built without a serial number is often called a “ghost gun” by gun control advocates, so of course Defense Distributed borrowed the term to ruffle feathers.
3D printing guns like the Liberator was more of a statement — it showed that a new era of manufacturing tech is upon us. Of course, no one would ever want to use a plastic gun if given the choice. The Liberator is prone to failure (video below), and usually only manages a few poorly aimed shots. In designing a cheap CNC machine specifically to make gun parts, Defense Distributed is delivering a viable weapon (other CNC mills cost many thousands of dollars). If you can make a lower receiver, all the other parts can be ordered online cheaply and legally.
The Ghost Gunner is capable of making anything that fits in the build envelope, as long as it’s created with Defense Distributed’s Physibles Development SDK (pDev) and distributed as a .dd file. In that respect, it’s not much different than any number of 3D printers. This is an entirely new era in the manufacturing of real world objects, in both plastic and metal. It used to be that you needed training as a gunsmith to make your own firearm, but that’s no longer the case. Whether or not you agree with Defense Distributed on the value of untraceable firearms in a free society, this is happening and regulation is miles behind the technological curve.
http://www.extremetech.com/extreme/191388-1200-the-price-of-legally-3d-printing-your-own-metal-ar-15-rifle-at-home