Silica Aerogel (TEOS, Base-Catalyzed)
Editor’s Note: This is an adaptation of the silica aerogel procedure from the Lawrence Berkeley National Laboratory site about aerogels, which for a long time was the only procedure for making aerogels publicly available. That procedure, we’re sorry to say, does not work. Maybe you’ve tried it. If you have, you’ll have noticed that the solution stays separated as two layers and a gel never forms. That’s because there’s not enough alcohol. Maybe it was a typo. So we modified that procedure and present the modified version that works for us below. If for some reason you have trouble with the procedure below, please leave a comment!
Materials
- Tetraethoxysilane (tetraethyl orthosilicate), Si(OC2H5)4
- Absolute (200-proof) ethanol
- Deionized water
- Ammonium hydroxide, 28-30 wt % in water
- Ammonium fluoride, NH4F
Optional
Gel Preparation
An
Excel calculator for determining amounts of chemicals required by target volume (mL) or mass (g) is available.
- Weigh 1.852 g NH4F and add it to 100 mL of water. Add 20.50 g (22.78 mL) ammonium hydroxide solution. Store this in a bottle so you can reuse it later. This is the “ammonium fluoride/ammonium hydroxide stock solution”. If you already have stock solution prepared you can skip down to step 2.
- Mix 4.7 g (5.0 mL) TEOS and 8.68 g (11.0 mL) ethanol in a beaker. This is the “alkoxide solution”.
- Mix 7.0 g (7.0 mL) water and 8.68 g (11.0 mL) ethanol in another beaker. Add 0.364 g (0.371 mL, ~8-10 drops from a disposable pipette) of ammonium fluoride/ammonium hydroxide stock solution. This mixture is the “catalyst solution”.
- Pour the catalyst solution into the alkoxide solution and stir. This is the “sol”.
- Pour the sol into molds and allow gel to form. Gel time is approximately 8-15 min.
What Everything Does
TEOS is the source of the silica. Water is what hydrolyzes the TEOS so that it can polymerize. Ethanol is a co-solvent that is miscible with both TEOS and water to get both into the same phase so they can react. Ammonium hydroxide is a basic (alkaline) catalyst that helps to make the reactions go faster. Fluoride ion is a catalyst that helps hydrolysis happen more quickly.
What Doesn’t Work
- Not using ammonium fluoride. It actually makes a big difference with TEOS. Although fluoride also makes reactions with TMOS go faster, TMOS will work fine with just a basic catalyst without fluoride.
- Using denatured alcohol that contains anything other than methanol or isopropanol as a denaturant instead of absolute ethanol. Some hardware store alcohol works, some doesn’t.
- Using sodium hydroxide (NaOH) instead of ammonium hydroxide in equal molar concentration. NaOH is a strong base so if you use it you’ll need to use a lower molar concentration of it than for ammonium hydroxide.
Variables You Can Play With
- Try adjusting the amount of solvent used to adjust the density of the resulting aerogel.
- Try adjusting the amount of the catalysts in the stock solution or the amount of stock solution you add. This will change the gel time and possibly the clarity of the gel (more catalyst means faster gel time but possibly lower transparency).
- You can substitute sodium hydroxide, sodium carbonate, or potassium carbonate for ammonium hydroxide but you will have to experiment with the amount.
- You can substitute sodium fluoride for ammonium fluoride in equal molar concentration, although your gel time may be affected since you lose the buffering effect of the extra ammonium ions.
Gel Processing Conditions
- Once the gel has set, place it under ethanol and allow the gel to age for at least 24 h.
- Exchange into 200-proof ethanol or acetone at least four times over the course of several days to a week.
- Supercritically dry. A suggested procedure would be to heat the CO2 through its critical point (31.1°C and 72.9 bars) to ~45°C while maintaining a pressure of ~100 bars. Depressurize at a rate of ~7 bar h-1.
What You Should Get
A transparent silica aerogel with a blue cast from Rayleigh scattering that appears yellowish when viewed in front of a light source from Mie scattering.
- Density 0.040 g cm-3
- Surface area 700 m2 g-1
Useful Information
Tetraethoxysilane (tetraethyl orthosilicate):
- Molecular weight 208.33 g mol-1
- Density 0.933 g mL-1
- Smells a little bit like spearmint
- Sigma-Aldrich part number 131903
Ethanol:
- Molecular weight 46.07 g mol-1
- Density 0.789 g mL-1
- Sigma-Aldrich part number 459836 or 459844, or get Everclear from a liquor store
Ammonium fluoride:
- Molecular weight 37.04 g mol-1
- Form is a fluffy, lightweight solid
- Sigma-Aldrich part number 216011
Ammonium hydroxide:
- Concentration is 28-30 wt % in water typically
- Molecular weight of NH4OH is 35.05 g mol-1, but this is not the molecular weight of the solution
- Density 0.9 g mL-1
- Form is a pungent liquid that smells like cleaning ammonia, use in a vent hood
- Sigma-Aldrich part number 221228
http://www.aerogel.org/?p=1027



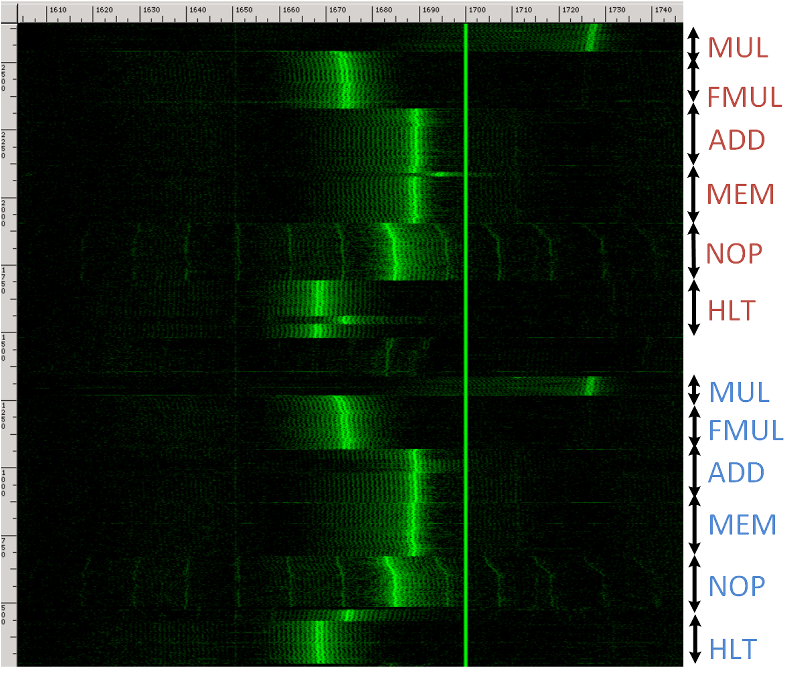
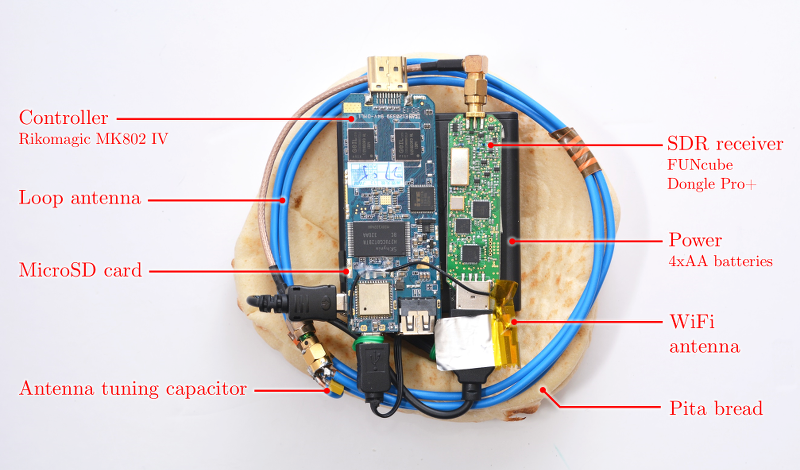
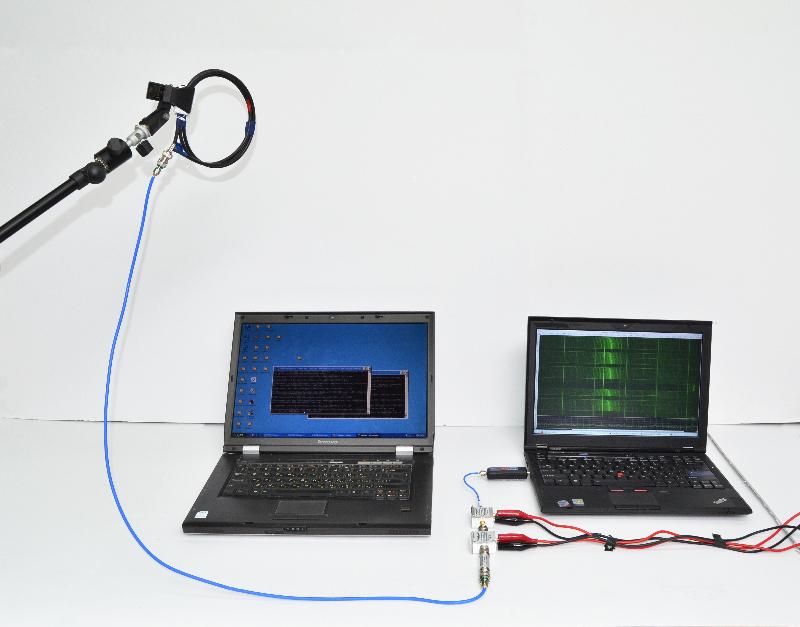
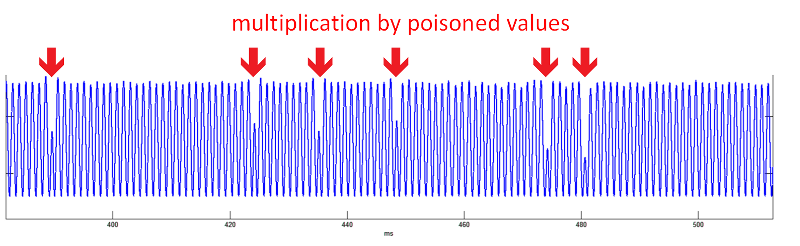








1 comment:
$1200: The price of (legally) 3D printing your own metal AR-15 rifle at home
Share This article
The Ghost Gunner itself is a small box about one foot on each side. Inside is an Arduino controller and a custom-designed spindle that holds a steel carbide drill bit. It works like any other CNC machine — the drill spins up and moves in three dimensions to carve items out of blocks of metal. However, this machine is specifically intended to make an AR-15 lower receiver. That’s the part of a gun that connects the stock, barrel, and magazine. You could say it’s the “gun” part of a gun. It’s also the part that’s regulated by the ATF and assigned a serial number. Selling it without a license is illegal, but making it yourself is perfectly fine. An untraceable gun built without a serial number is often called a “ghost gun” by gun control advocates, so of course Defense Distributed borrowed the term to ruffle feathers.
3D printing guns like the Liberator was more of a statement — it showed that a new era of manufacturing tech is upon us. Of course, no one would ever want to use a plastic gun if given the choice. The Liberator is prone to failure (video below), and usually only manages a few poorly aimed shots. In designing a cheap CNC machine specifically to make gun parts, Defense Distributed is delivering a viable weapon (other CNC mills cost many thousands of dollars). If you can make a lower receiver, all the other parts can be ordered online cheaply and legally.
The Ghost Gunner is capable of making anything that fits in the build envelope, as long as it’s created with Defense Distributed’s Physibles Development SDK (pDev) and distributed as a .dd file. In that respect, it’s not much different than any number of 3D printers. This is an entirely new era in the manufacturing of real world objects, in both plastic and metal. It used to be that you needed training as a gunsmith to make your own firearm, but that’s no longer the case. Whether or not you agree with Defense Distributed on the value of untraceable firearms in a free society, this is happening and regulation is miles behind the technological curve.
http://www.extremetech.com/extreme/191388-1200-the-price-of-legally-3d-printing-your-own-metal-ar-15-rifle-at-home