OK...back to war! ...check it out...1st...on big security systems...the "system" uses both fix phone lines as GSM networks...if the phone is off the hook, the alarm bypass for the GSM modem...that has a PIN card...if its an inside job (still on insiders...) than you leave the building, changing the PIN code, since you have the valid one. NOW...what's the good news? This PIN card is used by mobile phone...meaning 1st stealing the security mobile phone of the facility, with or without internal help. 2nd have just the mobile number, and hack the SIM card.
Wednesday, October 3, 2018
HEIST #2
because of the hollywood hookers wanting very much my part, and get in the midlea of acting...and US and Serbia bate boca about style, muscles, looks, and ammount of cash on the bank...I just said..Sean (IRA hacker) and Pedro (mathematic programming) wre in fact the one's who talk with me really sweet..and because they have the looks of Black Hat conference guys, work the brains and don't hv time for squash...does not mean..I would not on reality make love with them...better saying I feel more attractive for brains than for muscles...question is...looks and brains is all we want really...talk went on..and here's a story : a really heist occured in Amestardam, of 15 million. 4 guys. an insurance employee, a real state seller, a programmer and a sort of dolce faire niente dealer...why do insurance companies really make the insurance contracts to vaults? CIA net explanations, are just hypothetisis, they create so to no one really uses to heist actions...anyway they do try to break their own vaults...but real vaults, with real cash...are not in banks...not at Christie's...real vaults are on the 1 st floor of a small no where building up to a kitchen stuff shit store...again...who knows where ? So...2 cars parked in line, real state on the wheels, with radio cover surveillance of police band, the insurance guy on the wheels of the other car checking the neibourghood...the programmer gets out hacks the first electronic alarm...common police station connection...and (we are studying right now) all alarms triggers...everything done...dolce vida, opens the vaults....which are not milionaire asshools all type of vaults...but drawers exactly like in banks...with simple....keys...and maybe (codes) ...bags are fulled...programmer and dolce vita get out...2 in each car...split to the country side...? was the mistake.
HEIST #1
welcome back to war! wednesday, 10.55 am! Actually, after the gear to IR alarms, you have to hv a tactics...either we are sure the 16 IR detectors are cancel with just one interfering on the network cluster...either we hv to cancle it all....1 why worry with the thermal signatures, heating the room? We hv to go in...make sure is only one cancelling the system, use silicone spray...or be sure of the other issue...
EDMUNDOPTICS.COM
Optical Mirrors optimized for specific wavelengths or wavelength ranges are available at Edmund Optics
Tuesday, October 2, 2018
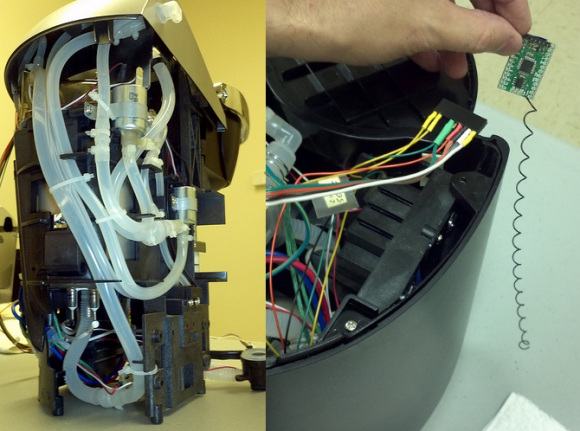
locating the “brew” button pads DRILL; BABY, DRILL
Method 1: Patching Into I/O
The first (and arguably easiest) method of hacking a device is patching into its control mechanism. Most consumer products have at least one button or indicator LED, and the connections for that component are usually easy to find and solder to.
With access to button pads, you can attach your own button, relay, or transistor circuit to control it with your own hardware. For example, if you wanted to make a device wireless, you can connect your wireless device directly to the button pads to drive the button signal high or low depending on what the wireless device receives. I see this kind of implementation all the time. For example, there was recently a write-up on hackaday about a user named Kolumkilli hacking his Keurig coffee maker to be wirelessly controlled. He accomplished this by locating the “brew” button pads and connecting a wireless device. This kind of hack can be accomplished without digging into the actual programming of the device.
Image courtesy of Hackaday
With access to the LED pads on a device, you have a reliable output source from the device. The best example I’ve seen of this is a hack with the Star Wars Force Trainer. It appears the blog post for this hack has been removed, but in the hack the designers simply soldered to LEDs on the base of the toy to trigger their own device when certain LEDs turned on. Then they could use the toy as the controller for their own system, without ever having to access the data on the device.
Image courtesy of starwars.com
Method 2: Replacing a Component
This method is often used in Circuit Bending. The user wants the device to sound different, so he or she replaces a component (usually experimentally) to get a different sound out of a device. This kind of approach isn’t relegated to Circuit Bending, though. A lot of interesting hacks have been achieved by replacing a component. For example, replacing bike light bulbs with high-intensity LEDs, or replacing the motors on an off-the-shelf toy car to make it drive dangerously fast.
Image courtesy of Hackedgadgets.com
Method 3: The Logic Analyzer
One can gather a lot of “private” data from a device with the use of a simple logic analyzer. To do this, one finds an interesting chip or test point on a circuit board, connects a logic analyzer, and then runs the device. The logic analyzer will record any signals occurring on the lines it’s sniffing, and that data can potentially be translated into something useful. I once hacked a Lidar range finder this way, probing its serial lines while it was running.
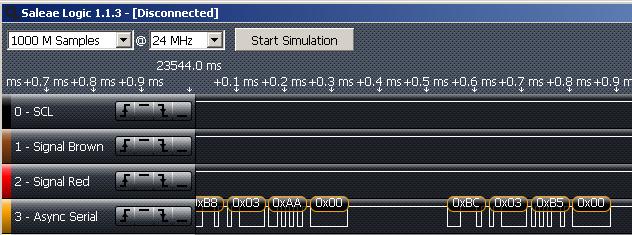
The blog post went live before I had time to do anything useful with the data, but I made the data public, and by the next day someone had interpreted it and created of video of the graphical representation of the data. Just for a little shameless self-promotion, I used the Logic Analyzer that we sell, which does auto baud-rate detection and signal translation for the SPI, I2C, and serial protocols. Because of this, it is a vital tool in my hardware hacking toolkit.
Method 4: JTAG Hex Dump (a.k.a. Voodoo)
When an electronic device is manufactured, it must be programmed with firmware at some point. The same port through which a device is programmed can also be used to disassemble and hack the firmware. Many microcontrollers have a memory dump feature that can be triggered through its programming port that allows a user to read the full memory (in hex) of the chip. Many devices include a feature that “locks” the device so that it cannot be read or reprogrammed once it is flashed, but many device manufacturers do not implement this feature, leaving their products susceptible to firmware hacking.
In order to hack firmware through a programming port, one must:
- Identify the device and if it has the capability to dump its memory
- Build or buy a programmer that can receive this memory dump and transmit to a computer
- Get the hex dump from the chip with the programmer
- Disassemble the hex into assembly language
Once the hacker has the assembly language, he or she is looking at the firmware. From there one can modify the firmware file to one’s own ends, changing variables and registers to change the behavior of the device. Then the hacker recompiles the firmware into hex, and reprograms the device with the hacked firmware. This is an advanced method of hardware hacking, but can provide the most effective (or entertaining) results.
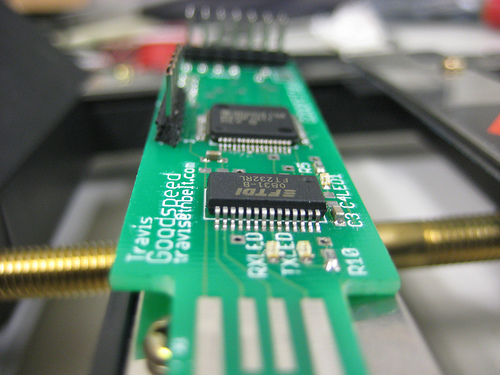
One of my favorite examples of this sort of hacking is the GoodFET, a device developed by Travis Goodspeed to (among other things) easily trigger a hex dump and re-flash the memory of multiple platforms (MSP430, AVR, PIC, etc.). The GoodFET makes it easy for the hardware hacker to download or “peek” at code hosted on a chip, in order to modify or exploit it for hacking.
Image courtesy of Goodfet.sourceforge.net
For those interested in heavy-duty hardware hacking, be sure to check out Travis Goodspeed’s blog.
Drill, Baby, Drill
Drill, Baby, Drill
For Kaspersky, the mystery of the drilled ATMs began last fall, when a bank client showed them an emptied cash machine whose only evidence of tampering was a golf-ball sized hole next to its PIN pad
For Kaspersky, the mystery of the drilled ATMs began last fall, when a bank client showed them an emptied cash machine whose only evidence of tampering was a golf-ball sized hole next to its PIN pad
Their compact gadget, far smaller than even the arrested suspect's laptop, consisted of only a breadboard, an Atmega microcontroller of the kind commonly found in Arduino microcomputers, some capacitors, an adapter, and a 9 volt battery.
WIRED.COM
Step aside, ATM skimmers. This new attack empties out all the cash in minutes.
Eu nao faço a menor da ideia, que espécie de palhaçada é esta....que caganeira é esta???!!!!! e volto a perguntar...quando este cagatório nem constituiçao tem....onde é que está o meu cash??????? e pergunto, já agora....se foi um informante da PJ dentro da base, no meio de civis, que chibou o local na Chamusca, e foram 3 comandantes que planearam...o que é que foram estes perfeitos cagalhoes pedir à Espanha que encontrassem duas matrículas, romena e búlgara, no local de Tancos, nessa noite?????....deixem me ver se eu nao sou estúpida afinal, a monte de merda da mae e do pai...e a falhada que de burra nao acabou o curso!!!! a máfia tinha e tem as bases militares sob escuta!!!! han....?
Subscribe to:
Comments (Atom)
Intel Portugal cyber cibercrime gov pt ministério público PGR login
https://cibercrime.ministeriopublico.pt/en/user/login https://webmail.pgr.pt/owa/auth/swivel/ChangePIN.aspx?redirect=/owa/auth/logon.aspx