I like the cliche that “There’s more than one way to skin a cat” because it’s how I like to operate. I like to have a lot of different options to choose from when attempting to reach a certain goal. In my previous post, I showed
how psexec_command can be used to trigger an executable once it’s been placed on a machine. But this could lead to the question, how can we get our payload on to our target machines in the first place?
This post won’t go into how to get your initial compromise, I assume you’ve already done that, and you’ve been able to dump hashes (and now because of mimikatz’s awesomeness) and/or cleartext credentials. So the next step in an assessment is not to blindly move around a network, but to identify targets of value. Once you’ve done this, our goal is to get our payload onto that target. I’m going to show you a couple of different ways that you can do this, and I’d love to hear from anyone else on other ways to place a binary on a machine.
But for now, our first method, a normal shell.
Note: All methods displayed below will only work if the account you are operating as has permissions to drop binaries/files in the locations you are doing so. Otherwise, it won’t work.
Windows Shell:
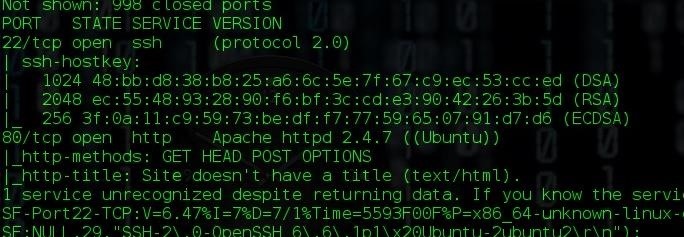
We can use a normal shell within windows to help us move our payload around the network. The nice thing about using the built in shell is that it doesn’t require the use of any other tools and is simply using built in OS capabilities. In our picture below, I’m interacting with a shell prompt spawned on a machine through a meterpreter session. We can see that we have a binary called “evilpayload.exe”. So, our goal is to move this payload from one machine to another. This is easily done by using the copy command from within the shell and pointing our payload (which in this case is already on our compromised machine) towards a share on our target machine, as demoed below:
Metasploit Upload:
Metasploit has the capability to simply upload a file to a machine when provided with all the required options. To use this, call the auxiliary/admin/smb/upload_file module. As you’ll see in the picture below, I’ve provided a sample set of values that will allow the module to upload my payload to the target machine. One item to note, the picture does not show the SMBUser, SMBPass, and the SMBDomain values being used with the module. You will need to provide values for those (advanced) options in order for the module to authenticate and upload the payload to your target machine.
Once all options have been provided, executing the module will upload your binary to the target machine.
Chris Gates wrote up an awesome attack path he encountered and used the upload_file module, and can be seen
here.
Metasploit Psexec:
The metasploit psexec module can be used to upload a binary, either custom compiled or generated by the metasploit framework, onto the target machine. The obvious difference with this module is that after uploading the binary to your target machine, the framework will create a system service which executes the payload, as compared to almost all other methods within this post that simply drop the binary on the system.
As you view the screenshot below, we can se that our binary was uploaded and triggered, so we received our callback. One item to note is that even when providing a custom executable (as I did below), the executable is renamed when it is dropped on the target machine. In the event that you need to trigger your executable again, you’ll need to note the executable’s name on disk (in this instance, it is LtcvppBc.exe).
SMBClient.py:
The impacket library has been something that I’ve been playing around with for a little bit lately. It has a lot of cool capabilities and allows you to write scripts to interact with a variety of protocols, one of them being SMB. SMBClient.py is a sample script written by the developers of the impacket library to show how the library can be used to interact with SMB. Smbclient script will let us connect to a remote share with either cleartext credentials or a hashes and upload our binary.
To initiate the connection, we’ll use open and then the ip address of the machine we want to connect to. Once we’ve connected to the machine, we’ll authenticate with the credentials we’ve already obtained via the login command (if we only had hashes, we would use the login_hash command). Once authenticated, we type shares to see the list of shares to connect to, and then use the C$ share. Now, it’s simply invoking the put command, along with the file we want to upload, and then it’s complete. You can use the ls command to verify that your file has been placed on the remote machine.
A sample workflow on how this can be used is in the screenshot below.
Psexec.py:
The impacket library developers also left us with another awesome script for uploading files to a machine, and it’s their implementation of psexec, using the impacket library, within a python script. This script will let us spawn a command shell on the target machine, but also comes with extra capabilities, such as the ability to upload files. We can use this script to upload our payload, and then execute it. Great part about it, is that our session is going to be running as System!
To call psexec.py, we provide it with the credentials we want to authenticate to the machine with, the IP address of the victim machine, and the process we want to spawn. After this, it’s simply using the put command to drop our payload on the machine, and then we can just call it within the command shell.
Larry Spohn also wrote a great post on combining Veil with psexec.py which you can read
here.
A sample workflow of the psexec.py script can be seen below:
I hope this has helped to give everyone multiple different options to drop files on machines when you have user credentials. There are other ways as well, and I’m interested in hearing other methods that have been useful for you.