Intercepting non HTTP/S traffic with Mallory
I was testing an application for a client and found that I could intercept the initial login request and response using burp suite, after that the application displayed a spinning wait dial and then closed down. When I removed the proxy the application would function so clearly something was amiss.
The problem with setting your devices to use burp is that it only fully handles HTTP/S and websockets, and it tends to drop traffic which does not fit this criteria. There are likely a number of ways to get around this by redirecting traffic but we also want to play with that non HTTP/S traffic so for this we will use Mallory Proxy.
Mallory is a transparent TCP and UDP proxy and it’s quite a powerful tool! Unfortunately it hasn’t been updated in quite a while and a lot of the documentation is TBC so it can take a while to get to know the ins and outs of it.
The following tutorial is pretty good at getting Mallory set up on a Kali box:
http://blog.opensecurityresearch.com/2012/05/mallory-mitm-fix-ssl-decryption.html
http://blog.opensecurityresearch.com/2012/05/mallory-mitm-fix-ssl-decryption.html
If you have any specific issues a more up to date thread can be found here
https://intrepidusgroup.com/insight/2013/07/getting-mallory-to-run-in-modern-versions-of-ubuntu/
https://intrepidusgroup.com/insight/2013/07/getting-mallory-to-run-in-modern-versions-of-ubuntu/
I don’t believe at the time of setup I ran into any issues with the setup script which downloads all the dependencies etc.
When Mallory is running it will listen on a specific port the problem is getting traffic to that port.
I found that setting my Kali vmware to act as a gateway was the best option. I set two bridged interfaces to link onto my testing LAN:
eth0 inet addr:192.168.0.184 Bcast:192.168.168.255 Mask:255.255.255.0
eth1 inet addr:192.168.0.180 Bcast:192.168.168.255 Mask:255.255.255.0
eth1 inet addr:192.168.0.180 Bcast:192.168.168.255 Mask:255.255.255.0
On the device I set the gateway to eth1/192.168.0.180 and then allow traffic to flow between the interfaces using iptables:
iptables -F
iptables -X
iptables -t nat -F
iptables -t nat -X
iptables -t mangle -F
iptables -t mangle -X
iptables -P INPUT ACCEPT
iptables -P FORWARD ACCEPT
iptables -P OUTPUT ACCEPT
iptables –table nat –append POSTROUTING –out-interface eth0 -j MASQUERADE
iptables –append FORWARD –in-interface eth1 -j ACCEPT
echo 1 > /proc/sys/net/ipv4/ip_forward
iptables -X
iptables -t nat -F
iptables -t nat -X
iptables -t mangle -F
iptables -t mangle -X
iptables -P INPUT ACCEPT
iptables -P FORWARD ACCEPT
iptables -P OUTPUT ACCEPT
iptables –table nat –append POSTROUTING –out-interface eth0 -j MASQUERADE
iptables –append FORWARD –in-interface eth1 -j ACCEPT
echo 1 > /proc/sys/net/ipv4/ip_forward
At this point you can fire up Wireshark and start to profile your application. What you want to do is pick out is the flow of traffic to specific hosts as well as the ports. At this point we start picking through and identifying our application traffic so as to redirect it to our respective proxies. Whilst Mallory is a powerful tool it lacks the flexibility that burp has which is why I separate the traffic streams.
I found that my mobile app was talking MQTT to a Mosquito server on a specific host, it was this MQTT traffic which Burp suite was dropping and thus causing the application to crash. So say we want to direct this traffic to our Mallory proxy we would use:
iptables -t nat -A PREROUTING -p tcp –dport -d -j REDIRECT –to-ports
If there is traffic to a certain host you want to just pass through you can use:
iptables -t nat -A PREROUTING -p tcp -d > -j ACCEPT
We can then tell iptables to route all our other 443 traffic to a burp instance:
iptables -t nat -A PREROUTING -p tcp –dport 443 -j DNAT –to-destination :
iptables -t nat -A POSTROUTING -p tcp –dport 443 -j MASQUERADE
iptables -t nat -A POSTROUTING -p tcp –dport 443 -j MASQUERADE
The following will redirect our port 80 traffic to a burp instance:
iptables -t nat -A PREROUTING -p tcp –dport 80 -j DNAT –to-destination :
iptables -t nat -A POSTROUTING -p tcp –dport 80 -j MASQUERADE
iptables -t nat -A POSTROUTING -p tcp –dport 80 -j MASQUERADE
Also the order of the IP tables rules is important, you need to have you host specific redirects before you main catch all redirects.
For a sanity check the following rules will redirect https://pentestpatners.com to Mallory and everything else to burp suite. I put my iptables rules in a little bash script so I can easily edit and rerun them.
#!/bin/bash
iptables -F
iptables -X
iptables -t nat -F
iptables -t nat -X
iptables -t mangle -F
iptables -t mangle -X
iptables -P INPUT ACCEPT
iptables -P FORWARD ACCEPT
iptables -P OUTPUT ACCEPT
iptables –table nat –append POSTROUTING –out-interface eth0 -j MASQUERADE
iptables –append FORWARD –in-interface eth1 -j ACCEPT
echo 1 > /proc/sys/net/ipv4/ip_forward
iptables -F
iptables -X
iptables -t nat -F
iptables -t nat -X
iptables -t mangle -F
iptables -t mangle -X
iptables -P INPUT ACCEPT
iptables -P FORWARD ACCEPT
iptables -P OUTPUT ACCEPT
iptables –table nat –append POSTROUTING –out-interface eth0 -j MASQUERADE
iptables –append FORWARD –in-interface eth1 -j ACCEPT
echo 1 > /proc/sys/net/ipv4/ip_forward
#redirect ssl pentestpartners.com to mallory
iptables -t nat -A PREROUTING -p tcp –dport 443 -d 78.129.201.147 -j REDIRECT –to-ports 4443
iptables -t nat -A PREROUTING -p tcp –dport 443 -d 78.129.201.147 -j REDIRECT –to-ports 4443
#redirect HTTP to burp
iptables -t nat -A PREROUTING -p tcp –dport 80 -j DNAT –to-destination 192.168.0.118:8080
iptables -t nat -A POSTROUTING -p tcp –dport 80 -j MASQUERADE
iptables -t nat -A PREROUTING -p tcp –dport 80 -j DNAT –to-destination 192.168.0.118:8080
iptables -t nat -A POSTROUTING -p tcp –dport 80 -j MASQUERADE
#redirect other SSL to burp
iptables -t nat -A PREROUTING -p tcp –dport 443 -j DNAT –to-destination 192.168.0.118:8080
iptables -t nat -A POSTROUTING -p tcp –dport 443 -j MASQUERADE
iptables -t nat -A PREROUTING -p tcp –dport 443 -j DNAT –to-destination 192.168.0.118:8080
iptables -t nat -A POSTROUTING -p tcp –dport 443 -j MASQUERADE
The following shows the streams running through Mallory
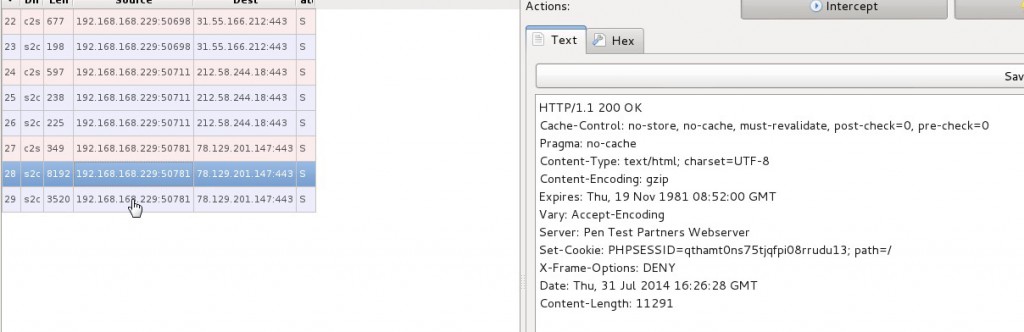
At this point hopefully you have successfully routed you troublesome traffic to Mallory and your standard HTTP/S to burp and your application should be running without any crashes. Mallory has some tampering features like burp which we will look at in the following section.
Using Mallory
Mallory can be quite troublesome to get working, as we have setup our own iptables rules do not toggle any of the options on the “Interfaces” tab. The protocols tab is pretty self-explanatory, you may need to define a new port if your traffic is non-standard but the help section is a little more complete there.
The streams tab will show the flow of traffic as well as the contents of each request, you need to enable “Intercept” and “Auto Send” on this page, if you disable auto send you have the option of editing requests before they go to the server and then manually send them.
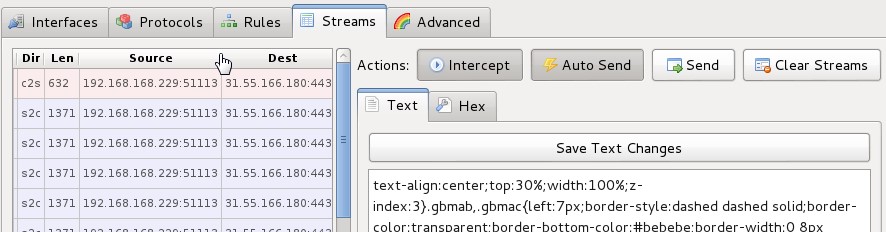
The documentation for the rules tab is a little lighter:
The data will be affected by the rules sequentially top to bottom and the rule we are likely to use the most is the “Muck” rule.
These rules are configured as follows:
- Name: Name of the rule
- Direction: Do we want to replace server to client, client to server or both
- Address: Do we want to only target one address
- Port: Do we want to target one port
- Payload: A string to patch in the requests/response before the rule will run
- Muck: This is a regex like in the sed command FIND/REPLACE/GLOBALLY
- Passthu: Does the packet then go to the next rule?
Mallory won’t decode gziped responses so it’s best to remove the accept Encoding-Header from requests using the following rule:
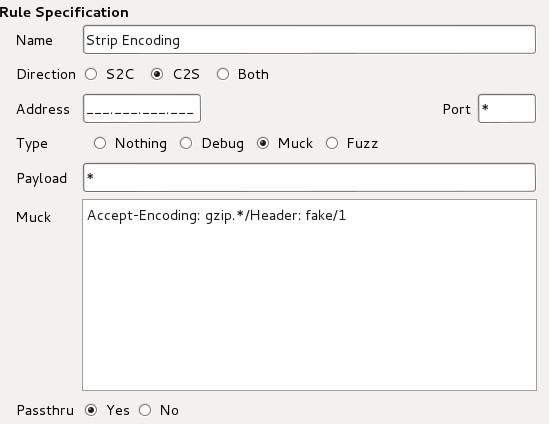
Make sure the rule is at the top of the list.
For a test we can use the following rule:
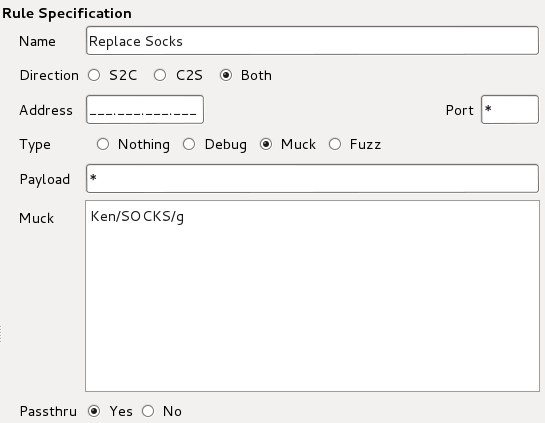
With the results:

For SSL traffic you can replace the ca.cer and ca.key in /mallory/current/src/ca/ with your exported burp files or you can import the ca.cer which Mallory generates onto your device.
The downside of mallory is that there is no way to export the streams into a meaningful format which can dissect the data, such as wireshark.
…unless you write a script to do it.
To save you the time and effort I have written one called mallory2pcap.py. There’ll be a separate post on that but there is a link to the code here. When given the mallory SQLite database and an output name it will write a pcap file on the fly using the contents of the database:
…unless you write a script to do it.
To save you the time and effort I have written one called mallory2pcap.py. There’ll be a separate post on that but there is a link to the code here. When given the mallory SQLite database and an output name it will write a pcap file on the fly using the contents of the database:
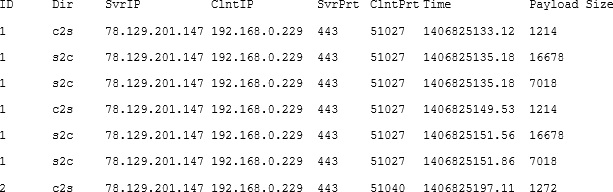
When this file is opened wireshark will dissect the requests and hopefully display the correct data:
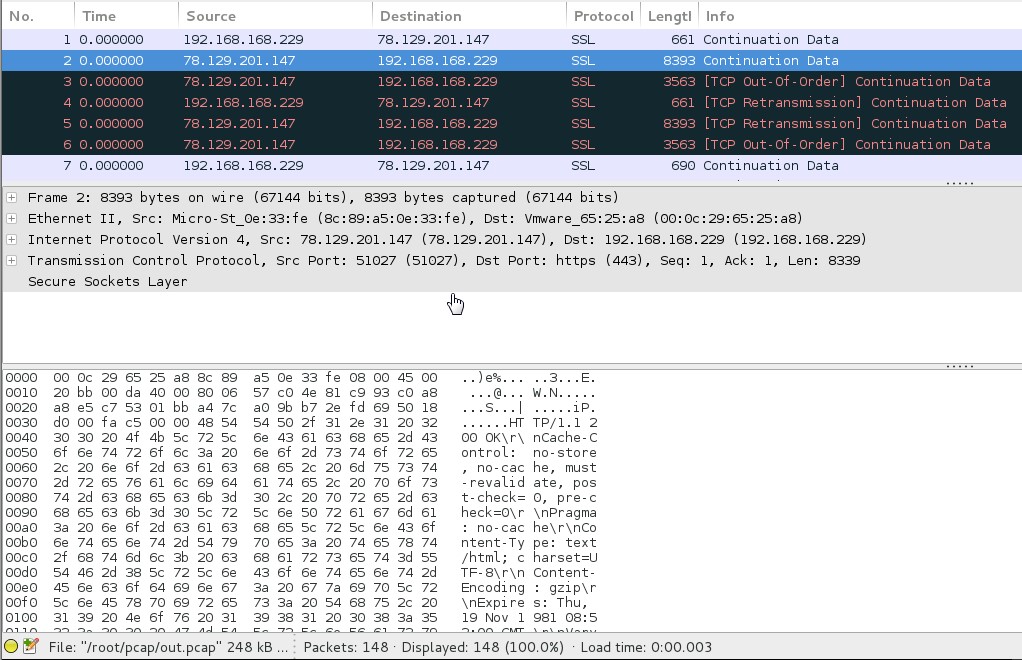
I do have to say several bottles of strong cider were consumed when this script was coded so there may be bugs and it’s mainly held together with tape but it should work!!
Hopefully this how-to has provided an insight into intercepting mobile application traffic and using some less known tools and tricks.



No comments:
Post a Comment