21
January
January
When we are involved in an incident handling and we are in charge of analyzing a traffic capture in a pcap format related to an attack, one of the things we usually need to do is get the files which were downloaded. The reason is that we need to have a copy of the malware or the exploit to analyze it by reversing engineer or similar...
We usually detect the original sources where these files were downloaded from just analyzing the pcap file, but they disappear in a short period of time from they were originally hosted. Because of that, we will need to extract them directly from the pcap file.
In this post, I will show you three different ways to achieve this goal using the the pcap hosted in Barracuda related to the www.php.net compromise which can be downloaded here:
http://barracudalabs.com/downloads/5f810408ddbbd6d349b4be4766f41a37.pcap
http://barracudalabs.com/downloads/5f810408ddbbd6d349b4be4766f41a37.pcap
Wireshark
As you know, Wireshark is the most popular network protocol analyzer. It is capable of extracting all the files which were downloaded and captured.If you load the pcap file in you Wireshark and use the command below...
http contains "in DOS mode"
... you can check that some executables were downloaded.
We are able to download all files which were downloaded like executables, pictures, javascripts, etc... by clicking File --> Export Objects --> HTTP and clicking on "Save all".
In the picture below shows you the files which are been recovered.
We use the command below to filter only the executables.
If we upload these files to Virustotal, we check that all of them have been categorized as malicious.
https://www.virustotal.com/en/
https://www.virustotal.com/en/
https://www.virustotal.com/en/
https://www.virustotal.com/en/
https://www.virustotal.com/en/
https://www.virustotal.com/en/
https://www.virustotal.com/en/
https://www.virustotal.com/en/
https://www.virustotal.com/en/
NetworkMinner
NetworkMiner is another Network Forensic Analysis Tool (NFAT) for Windows. Also, it can be installed on Linux using Mono. This tool is a great alternative to Wireshark if you just want to extract the files which were downloaded, look at the sessions, discover the DNS queries or get details about the mails detected from a pcap file.
Just loaded the traffic capture file, Network Minner downloads all files from it. Because of that, if you are using an Antivirus, It is possible it warns you if some file is detected as malicious.
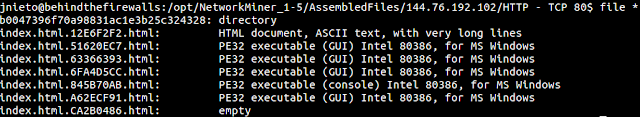
You can find the folder where files have been recovered by right-clicking on a file and selecting "Open Folder". In the Picture below you can see this folder.
If we get the SHA256 checksum of the PE files, we can see that the results are exactly the same than using Wireshark. We have got the sames files.
Foremost
Foremost is a well known file carving tool. It was developed by the United States Air Force Office of Special Investigations and The Centre for Information Systems Security Studies and Research and now, it has been opened to the general public.
This tool has been designed to work on image files, such as those generated by dd, Safeback, Encase, etc, or directly on a drive...
Although I usually use Wireshark or NetworkMinner I have read some blogs where they describe how to use Foremost to extract files from a pcap file. For this, I have decided to use it in our example.
Just downloaded we extract all files from the pcap file, we execute the command in the picture below to extract all the files.
We can check that a "/output/exe" folder has been created containing six files.
But the checksum is different than we got with Wireshark or NetworkMinner. It seems like Foremost hasn't work well with the pcap file... For this reason I don't usually use it with a pcap file...
I've uploaded these files to my Cuckoo Sandbox and it seems to be corrupted because the files couldn't run properly...
The VirusTotal links below redirect you to the reports of the corrupted executables:










.png)
No comments:
Post a Comment